Onboarding for AWS Member Accounts
Please read first:Before proceeding with onboarding for this type of cloud account, you must ensure the required pre-onboarding steps have been completed first.
For more information on what these prerequisites are and how to address them, please refer to the Pre-Onboarding for AWS Member Accounts user guide.
Introduction
An AWS member account is linked to a master account for consolidated billing, governance, and management. This setup allows organizations to manage multiple AWS accounts efficiently, applying policies, tracking costs, and ensuring compliance across all member accounts.
The account onboarding process follows a step-by-step flow with five steps, described in the list below. Users must complete every step by filling in the appropriate details so that they can proceed to the next step.
The onboarding flow for AWS cloud accounts covers the following main steps:
- AWS Cloud Account Type: Select the type of AWS cloud account that needs to be onboarded.
- Prerequisites: Select the cloud account scope, access type, and product(s).
- Add & Validate Credentials: Select the authentication type and provide the required AWS account credentials.
- Basic Settings: Select and/or input the basic settings for the cloud account.
- Advanced Settings (optional): This optional step allows users to add tags and set up any required governance configurations. Account governance configurations can also be done after the onboarding steps.
As users add all necessary details for each step in the onboarding flow, it will be marked as completed and no longer appears greyed out in the left sidebar.
Detailed onboarding steps are explained in the sections below.
Note:Before starting the onboarding process on the platform, make sure that you have followed and completed all the prerequisite steps in the AWS cloud portal. Refer to the PRE-ONBOARDING user guides for more information on how to complete these steps.
Member Account Onboarding Steps
Perform the following steps to onboard an AWS Member Account:
Navigating to the Onboard Accounts Page
Log in to the platform and on the left menu bar, go to Settings > Onboard Accounts.
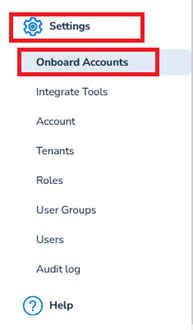
The Onboard Cloud Accounts starting page will appear. Here, users can select which cloud provider to onboard a new account for based on the available options.
Note:Users can also use the Dashboard button in the upper right corner of the page to go directly to the Account Governance Dashboard (Cloud Accounts) as a shortcut.
Select Onboarding Option
To start the onboarding process, hover over the AWS option under Public Cloud Providers, and an Onboard button should appear. Select Onboard to proceed.
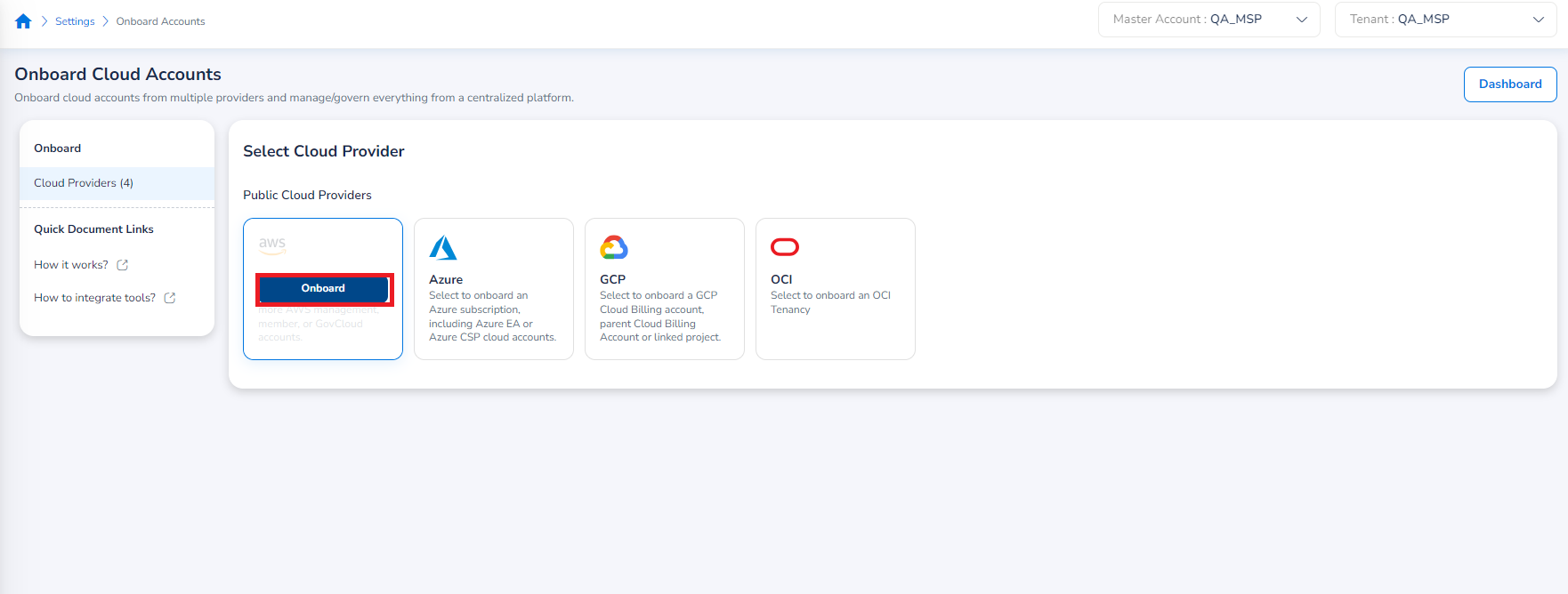
Select Cloud Account and Environment
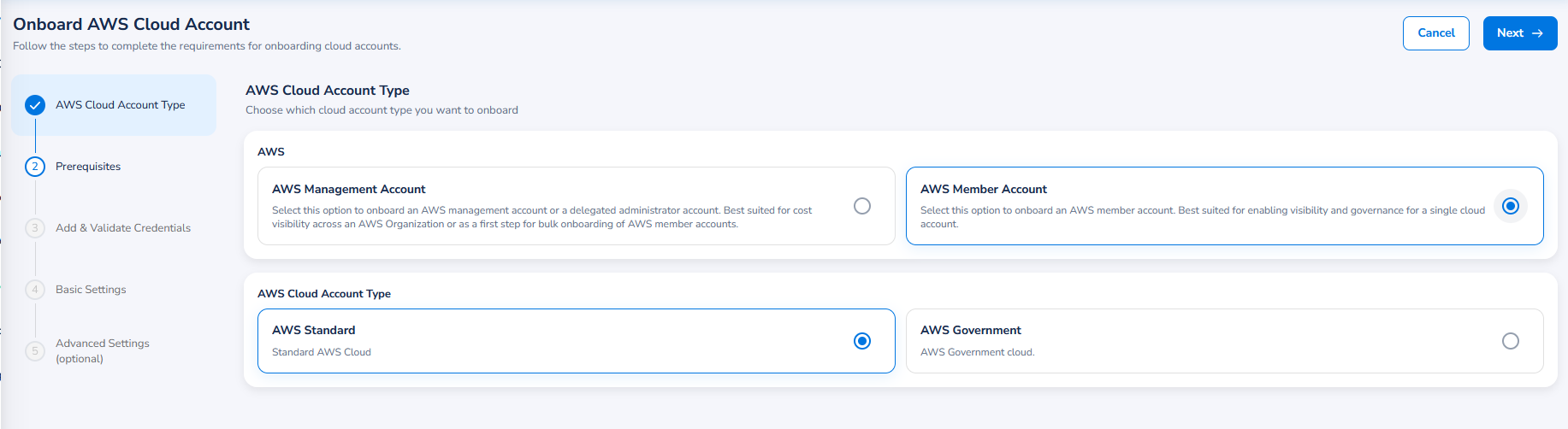
Once you’ve selected the AWS option, the page for the first step of the onboarding workflow should appear – AWS Cloud Account Type. In this step, users must select the specific AWS cloud account type to onboard, along with the AWS environment type (if applicable).
You can select one of the following cloud account types to be onboarded:
- AWS Management Account - Select this option to onboard an AWS management account or a delegated administrator account. Best suited for cost visibility across an AWS Organization or as a first step for bulk onboarding of AWS member accounts.
- AWS Member Account - Select this option to onboard an AWS member account. Best suited for enabling visibility and governance for a single cloud account.
And you can select one of the following environments to onboard a cloud account from:
- AWS Standard – Select this option to onboard cloud accounts from the AWS standard cloud environment.
- AWS Government – Select this option to onboard an AWS account from AWS Government cloud.
In this case, select AWS Member Account for the cloud account type, then either AWS Standard or AWS Government, based on your needs.
Note:The AWS Government option for Environment is currently only supported for AWS Member Accounts.
Click Next. The Prerequisites section appears.
Prerequisites
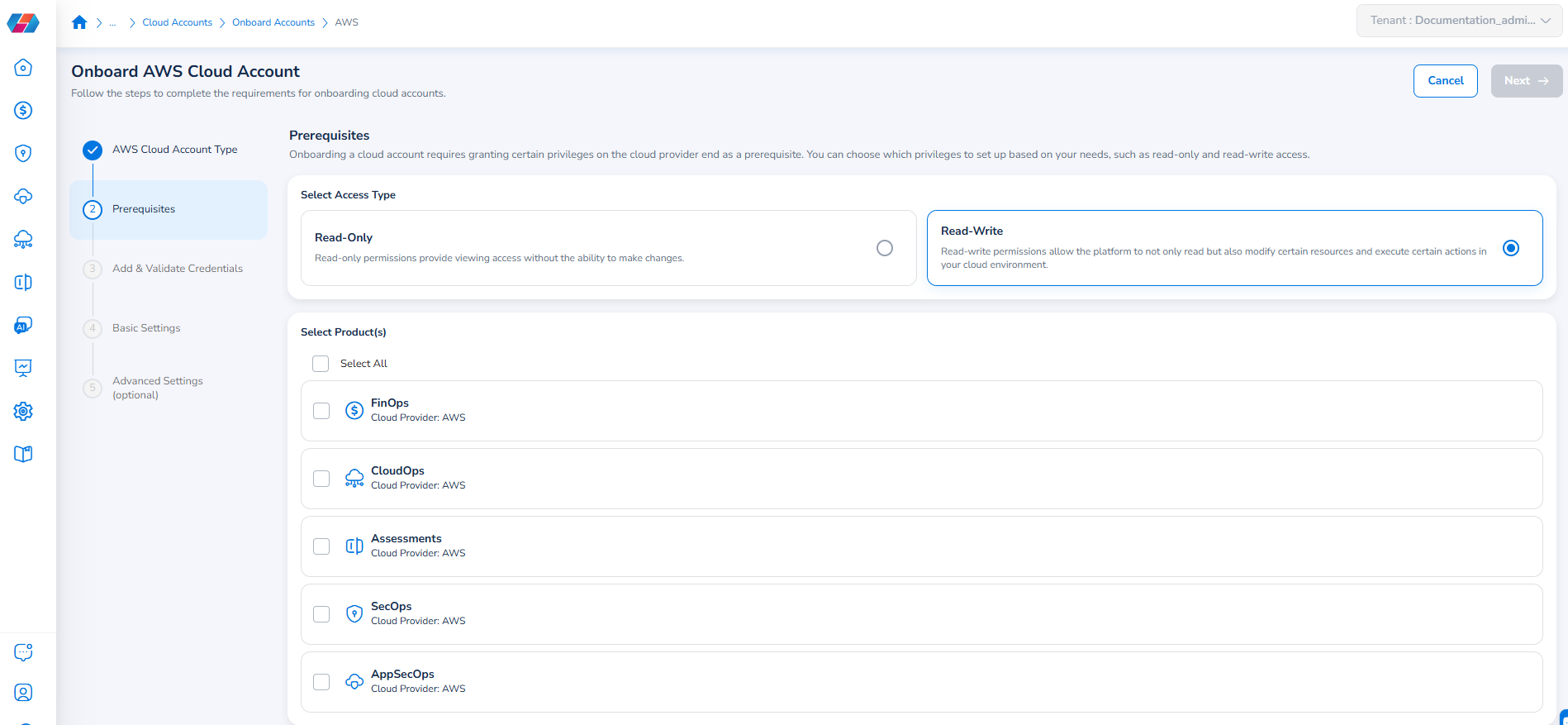
In the Select Access Type field, select one of the following options:
- Read-Only: This option provides viewing access without the ability to make changes.
- Read-Write: This option allows the users to view, modify, and manage resources.
Note:For AWS Member Accounts using the AWS Government environment option, Read-Write access is currently not supported.
In the Select Product(s) field, select the products that will be accessible through this account. The available products are shown based on the product bundle that was chosen during the account master creation. For example, the Governance product bundle includes: FinOps, SecOps, and CloudOps.
Note:For AWS Member Accounts using the AWS Government environment option, the FinOps product is currently not supported.
Click Next. The Add & Validate Credentials section appears.
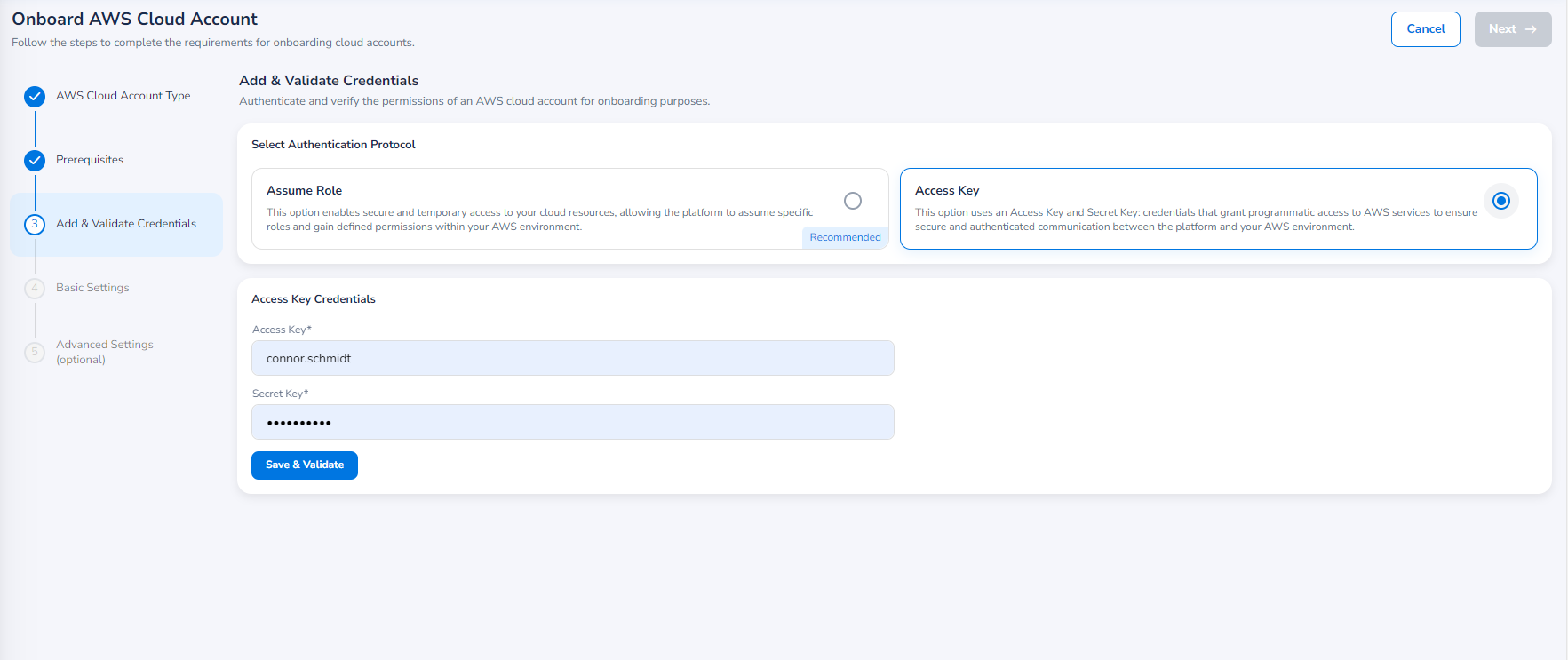
Add & Validate Credentials
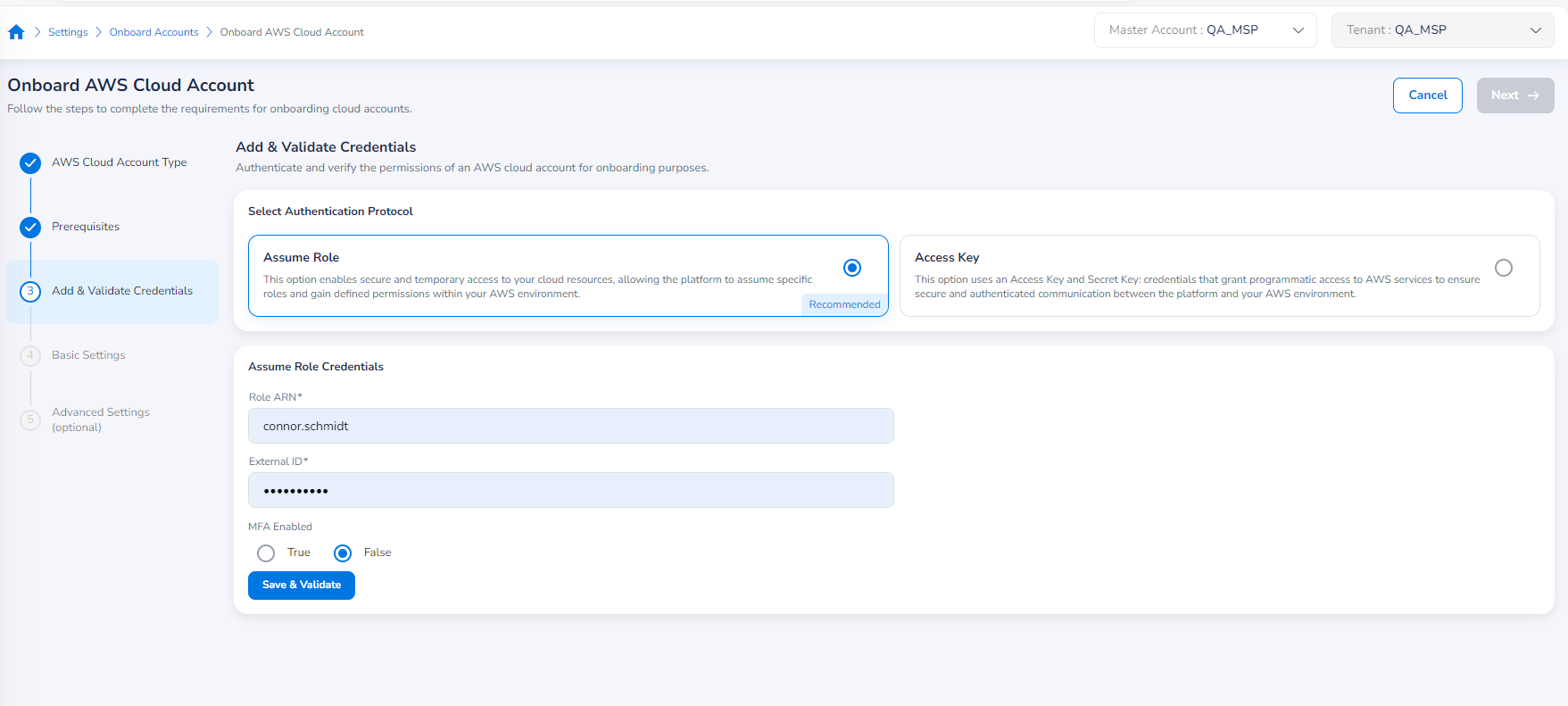
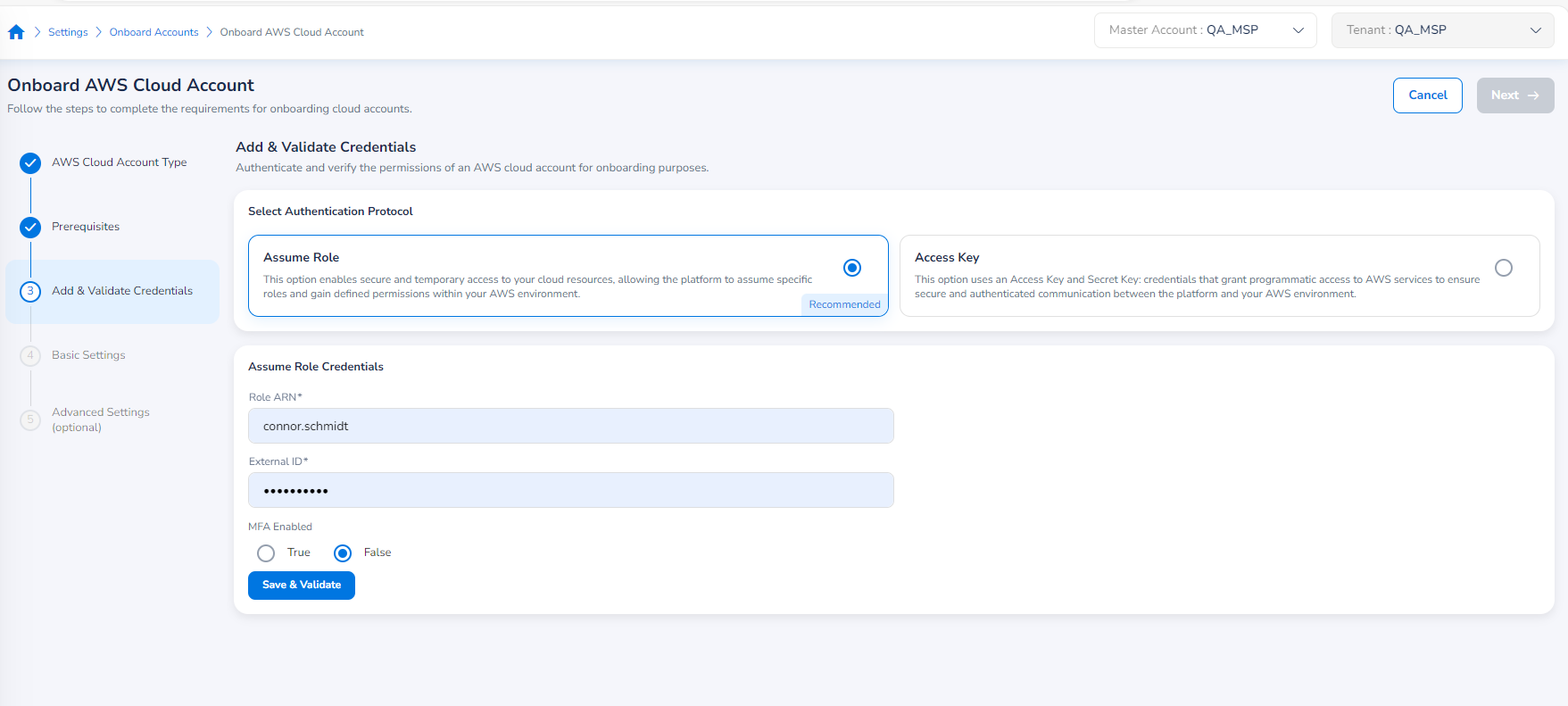
In the Select Authentication Protocol field, you will have two options to select from:
- Assume Role (recommended option)
- Access Key
Assume Role Option
If the user selects Assume Role, then ARN will be used for authentication of the AWS cloud account during onboarding. The following fields are enabled and needs to be filled:
- In the Role ARN box, type the ARN of the AWS account that needs to be onboarded.
- In the External ID box, type the external ID.
- In the MFA Enabled field, select True or False based on the Multi-Factor Authentication settings.
- Click Save & Validate.
Access Key Option
If the user selects Access Key, then the access key and secret key will be used for authentication of the AWS cloud account during onboarding. The following fields are enabled and needs to be filled:
- In the Access Key box, type the access key.
- In the Secret Key box, type the secret key.
- Click Save & Validate.
Validation
If the validation is successful, then a success message will be displayed.
If the validation fails, then an error message will be displayed along with an option for View Log. You can click View Log to view the error details and then click Re-Validate to retry the validation.
Note:After the completion of successful validation, the Save & Validate button turns to Re-Validate. You can click Re-Validate to validate the account again.
Click Next. The Basic Settings section appears.
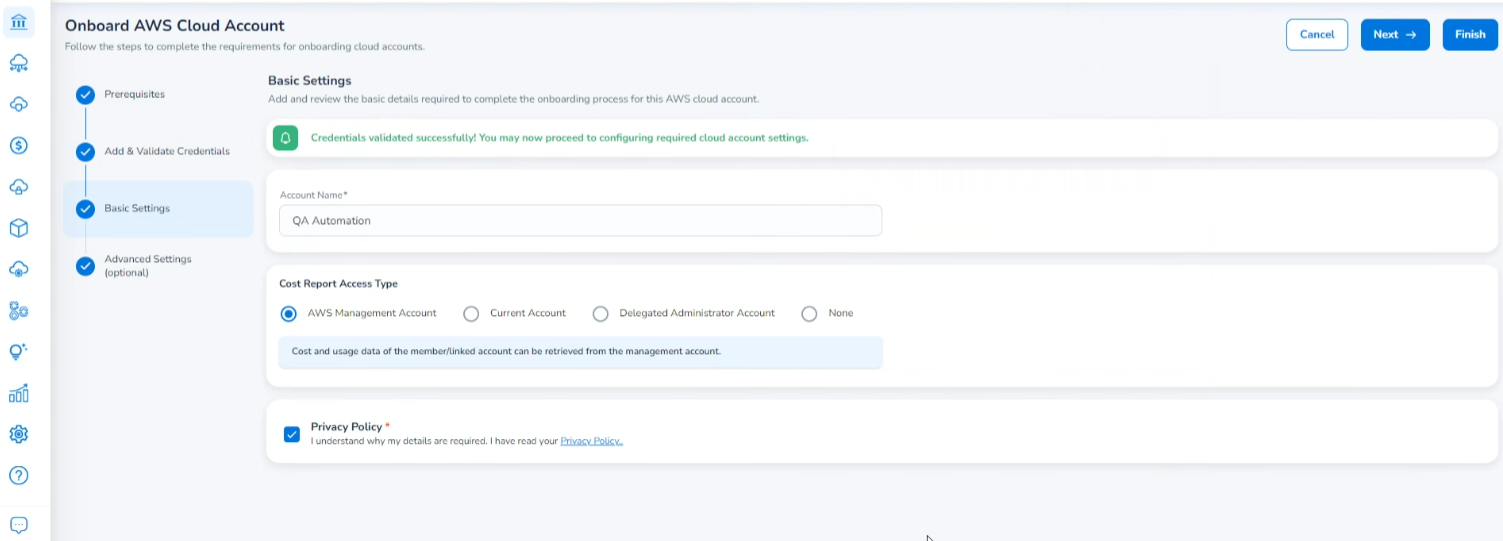
Basic Settings
On the Basic Settings page, you’ll need to provide some basic details for the cloud account(s) being onboarded.
The following basic details can be provided on this page:
- In the Cost Report Access Type field, select one option from AWS Management Account, Current Account, Delegated Administrator Account, and None.
- Select the Privacy Policy checkbox to accept the terms and continue with the onboarding process.
- The Account Name box will be prefilled, but if required, you can update it.
Note:While onboarding AWS accounts, the Account Name field should not exceed the maximum character limit of 50 characters including special characters.
You can click Next to set up advanced settings or click Finish to complete the account onboarding. Please note that the step for configuring advanced settings is not mandatory and can be skipped.
If you click Next, then the Advanced Settings section will be displayed.
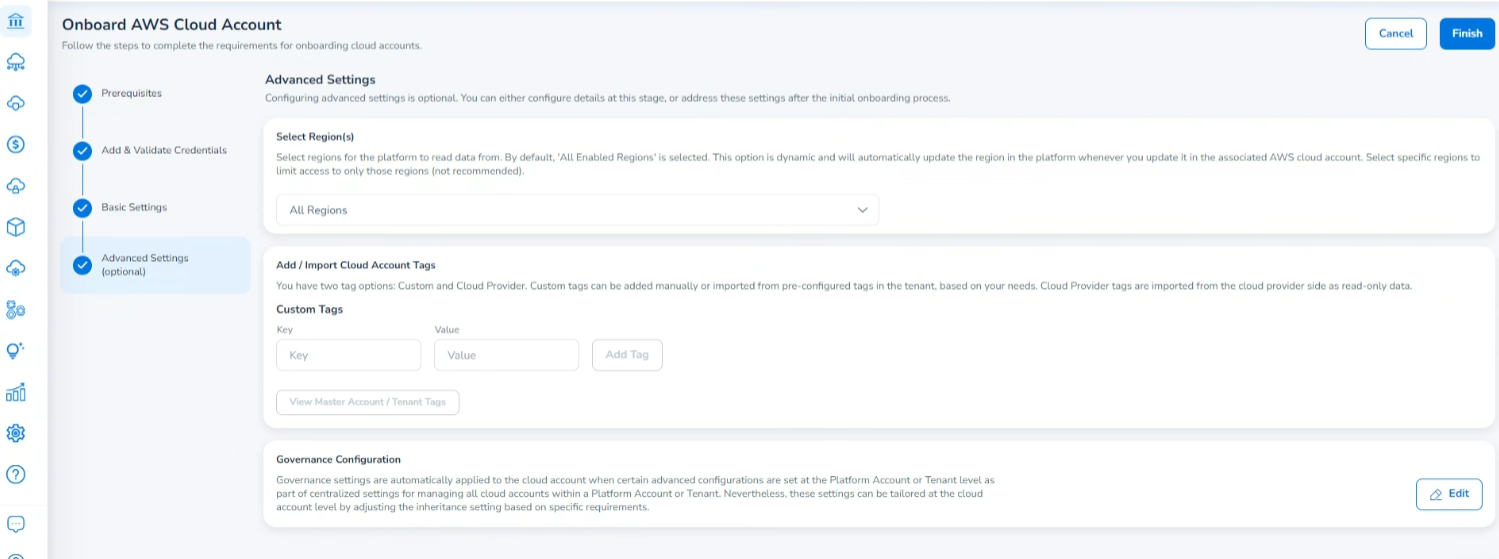
Advanced Settings (Optional)
The Advanced Settings page is where users can make additional configurations of the cloud account being onboarded, like tags and governance settings. Again, this section is optional and can be completed later, if desired.
Select Region
In the Region(s) drop-down list, click to select all applicable regions and then click Ok. This field is used to select regions for the platform to read data from. You can select specific regions to limit access to only those regions.
Add/Import Cloud Account Tags
In the Add/Import Cloud Account Tags section, do any of the following to fill in the tag details.
In the Custom Tags field:
- In the Key box, type the tag key.
- In the Value box, type the tag value.
- Lastly, click Add Tag.
The added tag appears below.
When you click View Master Account/Tenant Tags, the Custom Tags dialog box opens where you can select the required tags and click Insert Selected Tags. The selected tags will now show up for the account to be onboarded.
Governance Configuration
In the Governance Configuration field, click Edit to configure the required settings. Refer to Governance Configuration for detailed steps.
Once you’re done with your configurations, select Finish.
The Onboarding Status dialog box appears that shows the progress of account onboarding. You can click Go to the Dashboard to return to the Account Governance Dashboard.
Governance Configuration
The Governance Configuration page includes many sections where configurations can be made. You need to select the configuration you want to apply to your onboarded account. All the available configuration sections are explained below. Refer to the relevant configuration and follow the steps. These governance configurations can be made while onboarding the account or can be done post onboarding.
FinOps
The configurations that can be done for FinOps are explained below.
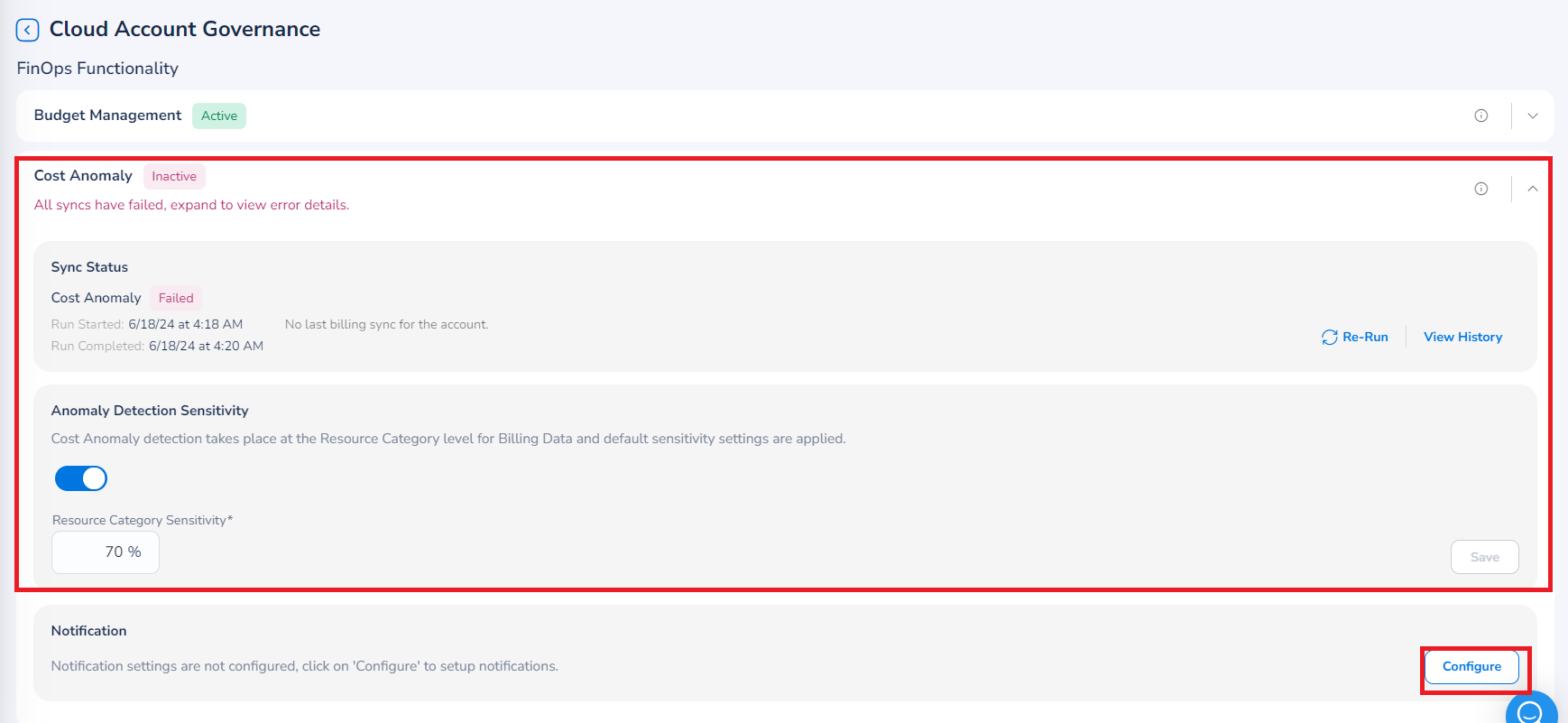
Cost Anomaly
-
Expand the Cost Anomaly section.
-
Ensure that Anomaly Detection Sensitivity field is enabled (the slider is on the right side).
-
In the Resource Category Sensitivity box, the settings are applied by default. If you want to edit the default setting, add the sensitivity based on which anomaly would be detected.
-
In the Notification section, click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
SecOps
The configurations that can be done for SecOps are explained below.
AWS Security Hub Security Posture
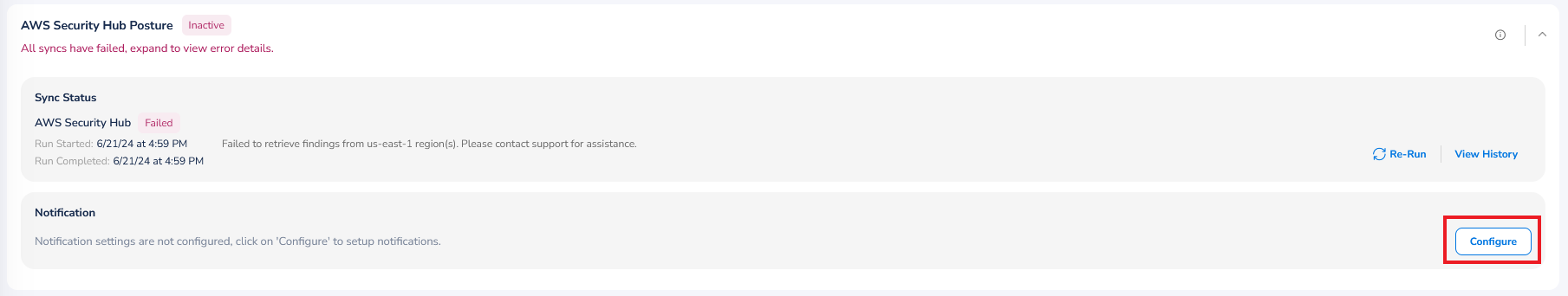
To configure notifications for AWS Security Hub Security Posture, perform the following:
- In the Notification section, click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
Threat Management
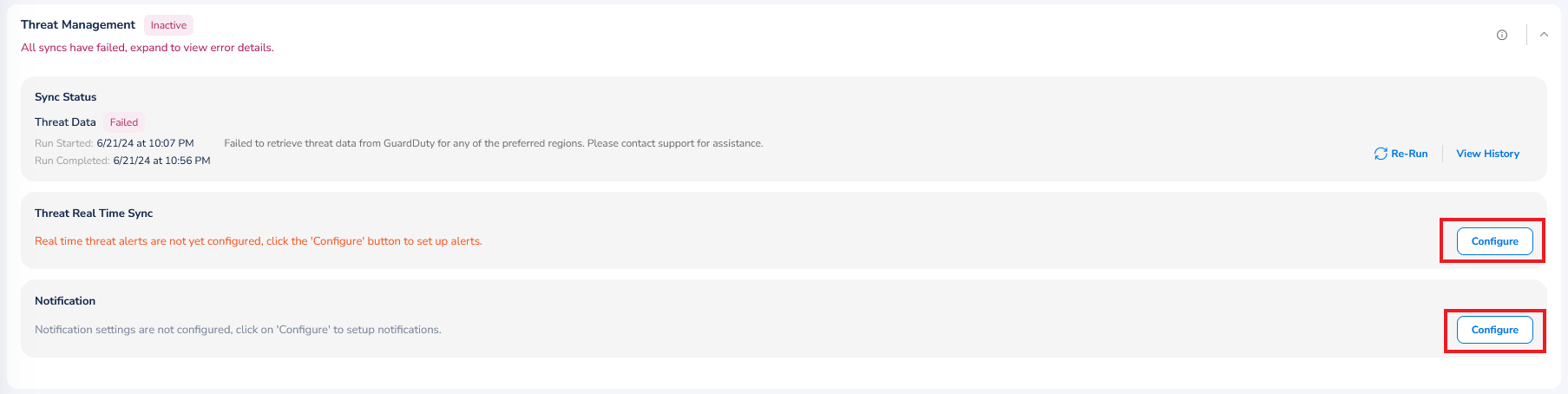
To make configuration for threat detection, perform the following steps:
- Click to expand the Threat Management section.
- To configure Threat Real Time Sync, click Configure. A dialog box displays.
- In the Select Region list, click to select the region where the configuration needs to be made, and then click Ok.
- Click Validate. If there are no errors, then go to next step, else click Re-Validate. Select/enter relevant details and validate. Upon successful validation, the configuration can be saved.
- Click Save & Exit.
If configuration is already made for Threat Management, then you can click View to see the existing configuration or you can click Delete to remove the configuration.
To configure notifications related to threat management, perform the following steps:
- In the Notification section, click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
Vulnerability Assessments

To configure notifications for Vulnerability Assessments, perform the following:
- In the Notification section, click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
CloudOps
The configurations that can be done for CloudOps are explained below.
Activity
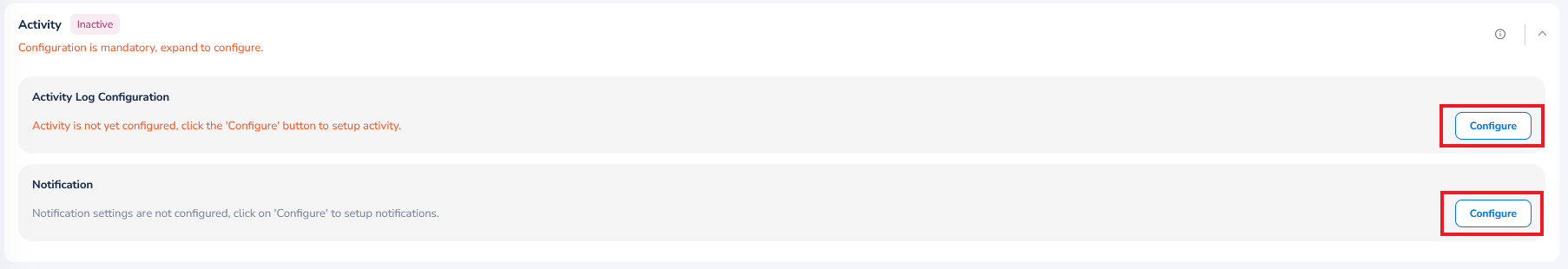
To view Activity for the AWS cloud environment, perform the following:
- Expand the Activity section.
- In the Activity Log Configuration section, click Configure. A dialog box appears.
- In the Select Region list, select the relevant option(s) and then click Ok.
Next you will have to configure activity logs individually for the selected regions. - Click Configure corresponding to a region.
- Select either Create New or Select Existing.
- If you select Create New, then in the CloudTrail Name box, type a name for the new CloudTrail and in the Bucket Name box, type the name of the bucket. You can select Setup multi-region trail checkbox, if required, and then click Continue.
- If you choose Select Existing, then in the CloudTrail list, select an appropriate option and then click Continue.
- Repeat steps 4 and 5 to configure other regions selected in step 3.
- If you want to apply default template for activities to monitor your AWS setup, then select the Apply Default Template checkbox.
- Click Validate.
- Click Save & Exit.
If configuration is already made for activities, then you can click View to see the existing configuration or you can click Delete to remove the configuration.
To configure notifications for activity:
- In the Notification section, click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
Assessments
The configurations that can be done for Assessments are explained below.
Assessments Functionality
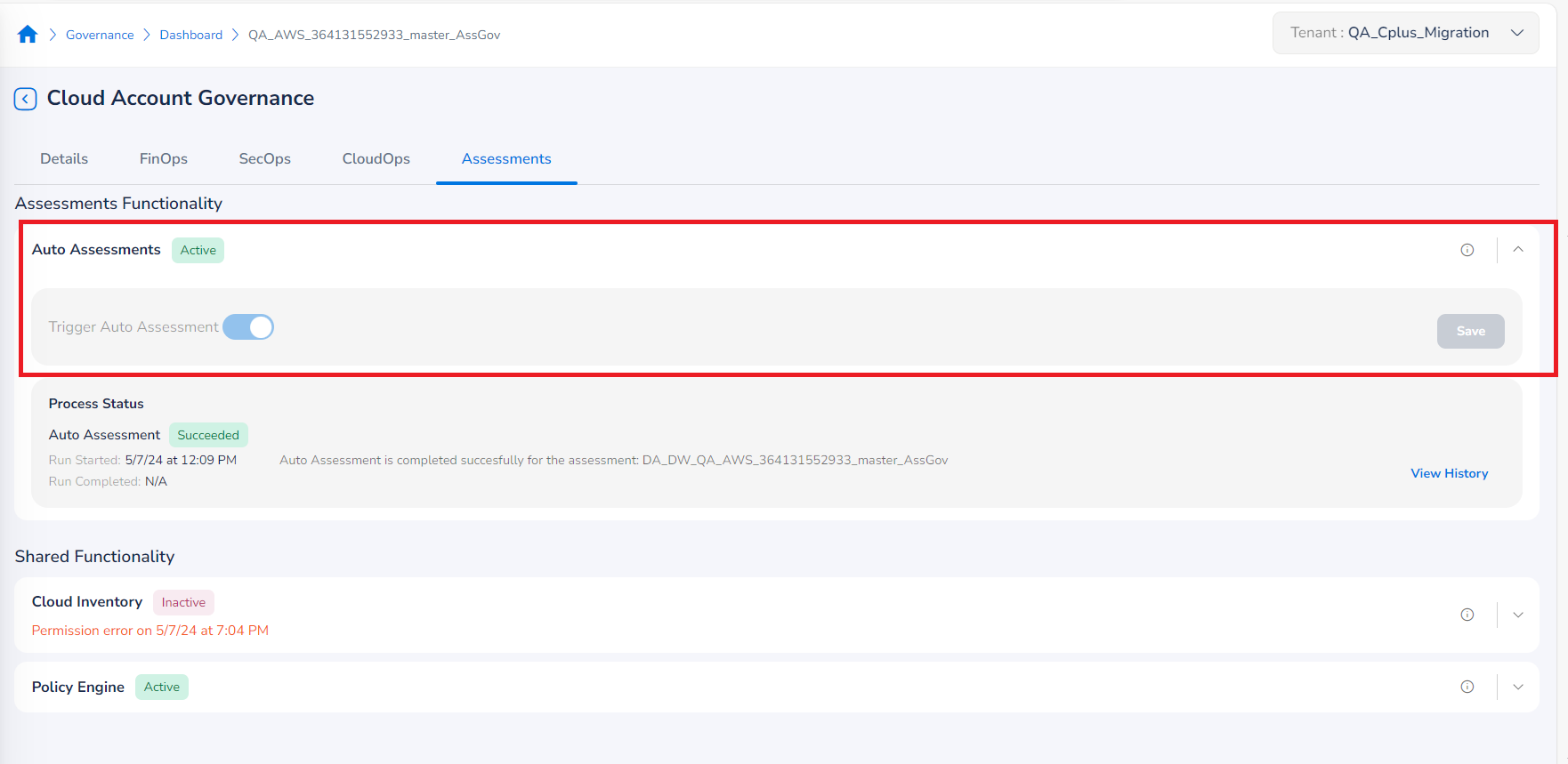
When a cloud account is onboarded, users can configure the auto-assessment functionality based on their requirements. Users can choose to either enable or disable the option for auto-assessment while an account is being onboarded (as part of account governance configurations). By default, the option to run an auto-assessment is disabled.
If a user disables the option for auto-assessment, no assessment will be triggered on the onboarded account. If a user enables the setting, it will be triggered automatically on the onboarded account.
If a cloud account is onboarded with auto-assessment disabled at first, but later the auto-assessment option is enabled, then the assessment will proceed to be triggered for that account.
- If the auto-assessment option is already enabled, users can disable it before the auto-assessment gets triggered.
- If the auto-assessment option is enabled and then the assessment is triggered, then after that point it cannot be disabled.
To enable auto assessments:
- Expand the Assessments Functionality section.
- In the Trigger Auto Assessment field, move the slider to right to enable it.
- Click Save.
Shared Functionality and Integrated Tools
The configurations that can be done for Shared Functionality and Integrated Tools (common across all products) are explained below.
Policy Engine
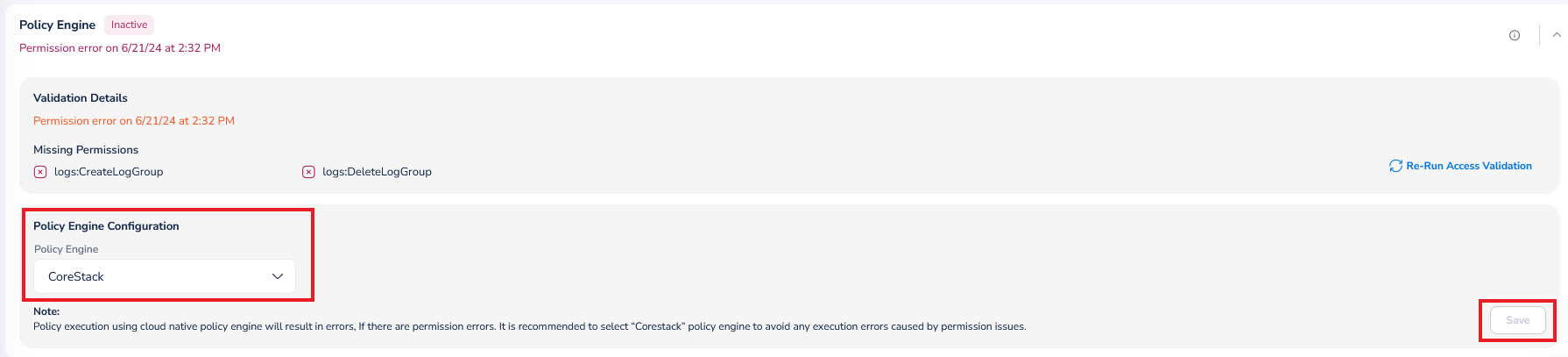
To configure the policy engine for an account, perform the following steps:
- Expand the Policy Engine section.
- In the Policy Engine list, click to select the policy engine for the account and click Ok.
- Click Save.
Monitoring
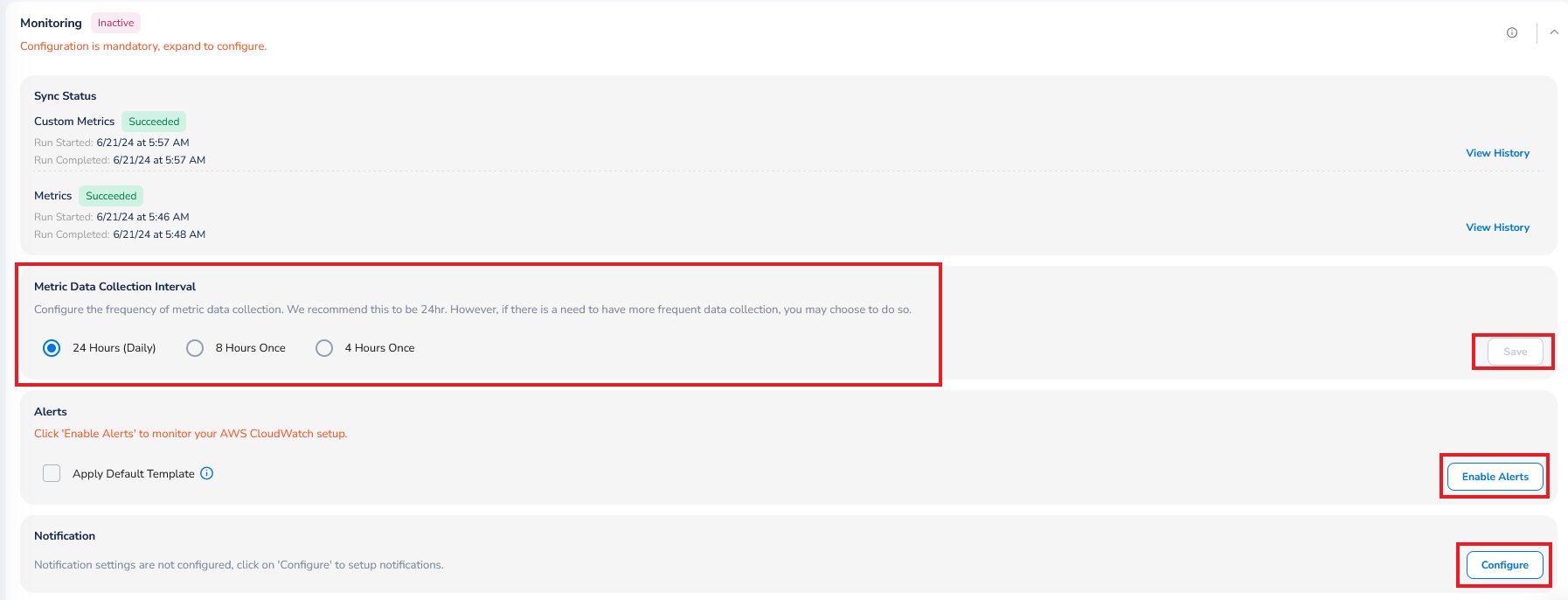
To configure monitoring of accounts, perform the following:
- Expand the Monitoring section.
- In the Metric Data Collection Interval field, select the frequency in which the metric data needs to be collected and click Save. The available options are 24 Hours (Daily), 8 Hours Once, and 4 Hours Once.
- Click Save.
To enable alerts, click Enable Alerts and to delete alert configuration, click Delete. To apply default template to monitor CloudWatch setup, select the Apply Default Template checkbox.
To configure notifications for monitoring alerts, perform the following:
- Click to expand the section, and then click Configure. The Notifications Settings dialog box appears.
- Select the Enable Notification checkbox. The Email Address, Webhook, and Microsoft Teams Webhook fields are displayed.
- In the Email Address box, type the email address of the user(s) and click Add.
- In the Webhook box, type the webhook link(s) and click Add.
- In the Microsoft Teams Webhook box, type the URL(s) for Microsoft Teams Webhook and click Add.
- Click Save & Apply.
Updated 4 months ago