AWS Security Hub
AWS Security Hub is a tool available in the AWS cloud platform. Integrating AWS Security Hub with CoreStack helps users to view all security details in CoreStack. In other words, this integration helps users see all security-related findings for their AWS cloud accounts in one place. With this integration, they don’t have to refer to different sources to learn about security findings across their accounts.
AWS Security Hub aggregates all the security findings from AWS, then all those details are made available in CoreStack. Users can only view the details. No remediation steps can be taken from CoreStack. If a Security Hub master account is integrated with CoreStack, then accounts that are not onboarded in CoreStack are also displayed in the findings. To view the relevant list of onboarded accounts that are integrated with AWS Security Hub, users must use the available filter options to filter out any irrelevant accounts. If a Security Hub account is not the account master and is integrated with CoreStack, then accounts that are onboarded in CoreStack will be displayed in the findings.
The cloud account details from AWS are synced at particular periods, and any updated details will be shown in the findings list within CoreStack.
Configuring AWS Security Hub
Perform the following steps to enable AWS Security Hub settings in CoreStack:
- Access the CoreStack application.
- On the left navigation pane, click Governance > Account Governance.
- For an AWS account, click VIEW > View Settings.
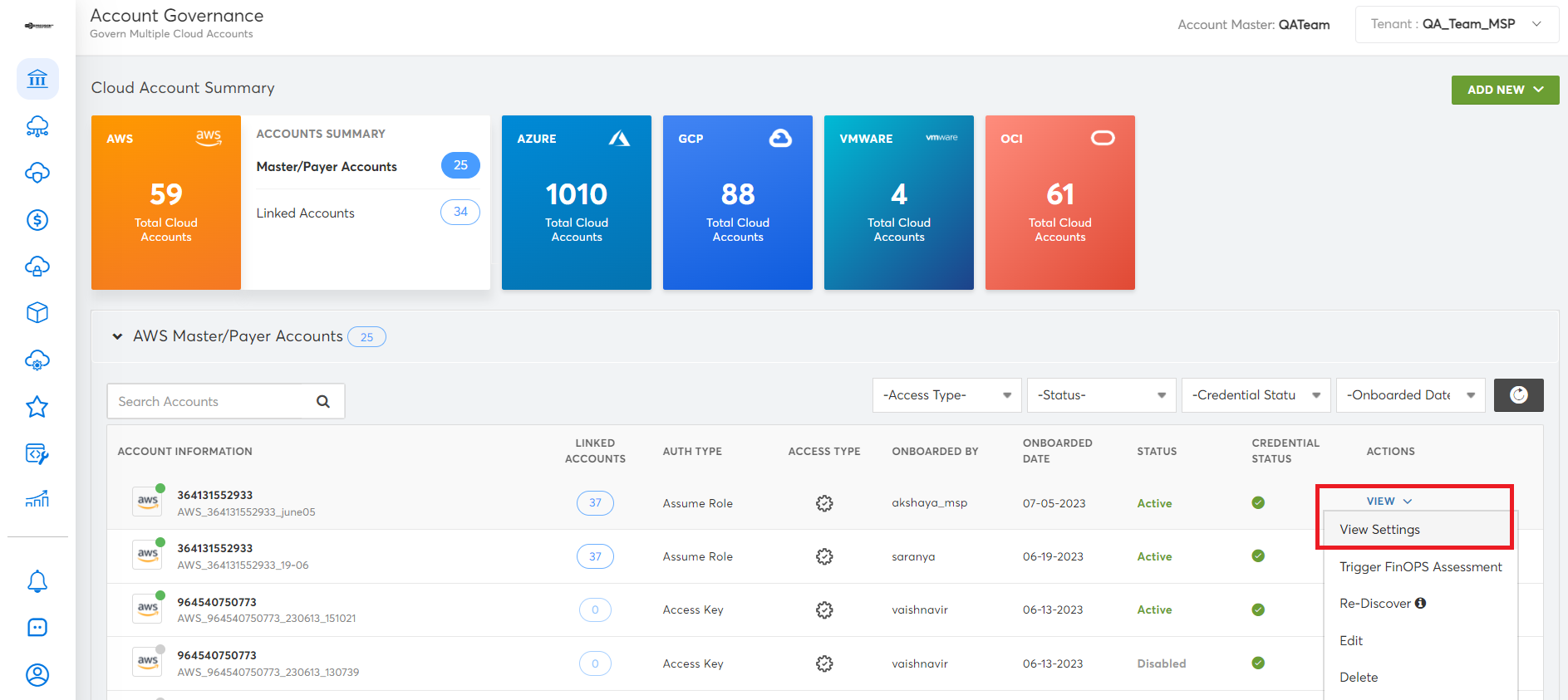
- Click Additional Account Settings > Security Tools Integration tab.
- Select the Integrate with AWS Security Hub checkbox and click SAVE.
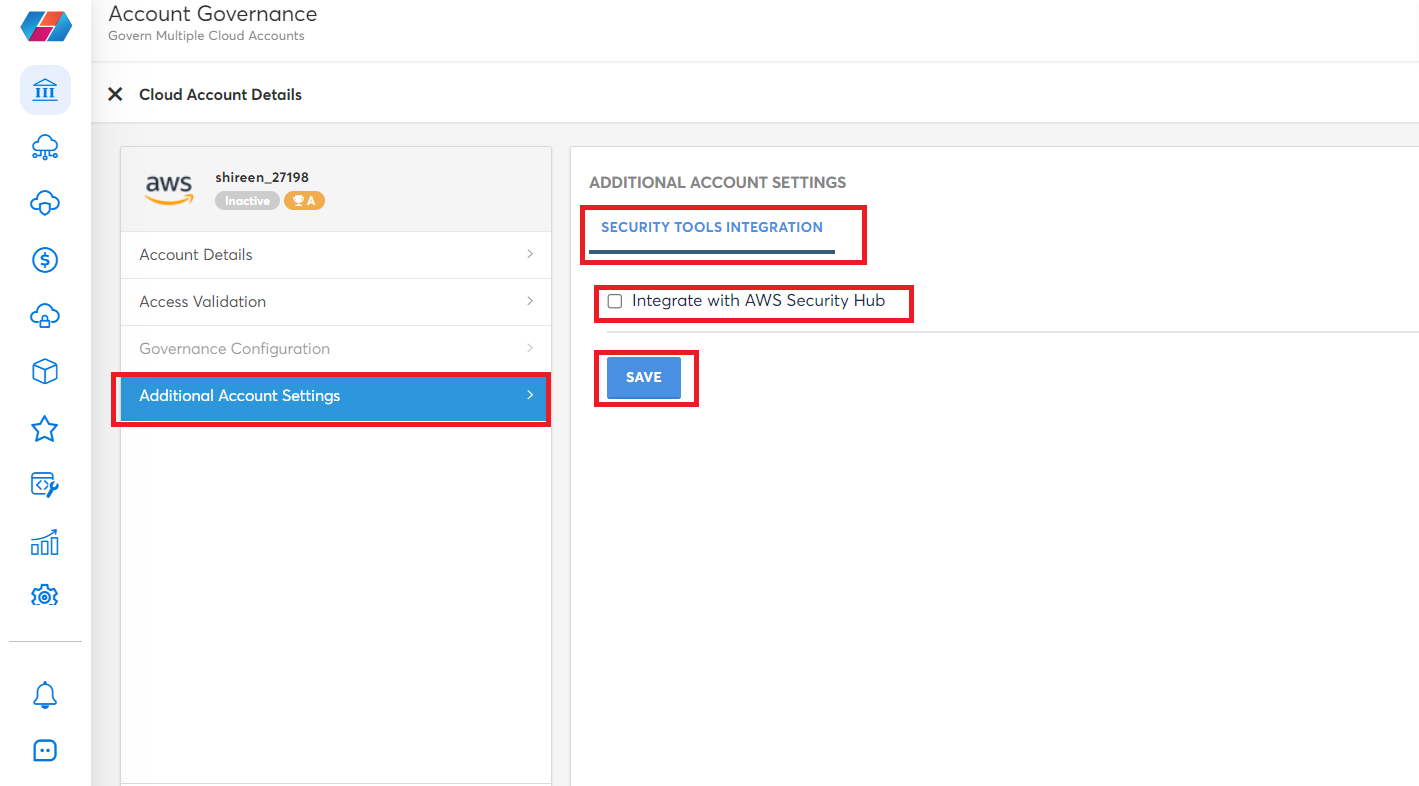
A confirmation message is displayed.
View Security Findings
After the AWS Security Hub integration setting is enabled, you can view the security findings from within the CoreStack application.
Perform the following steps to view security findings:
- Click Tools Integrations > Security > AWS Security Hub.
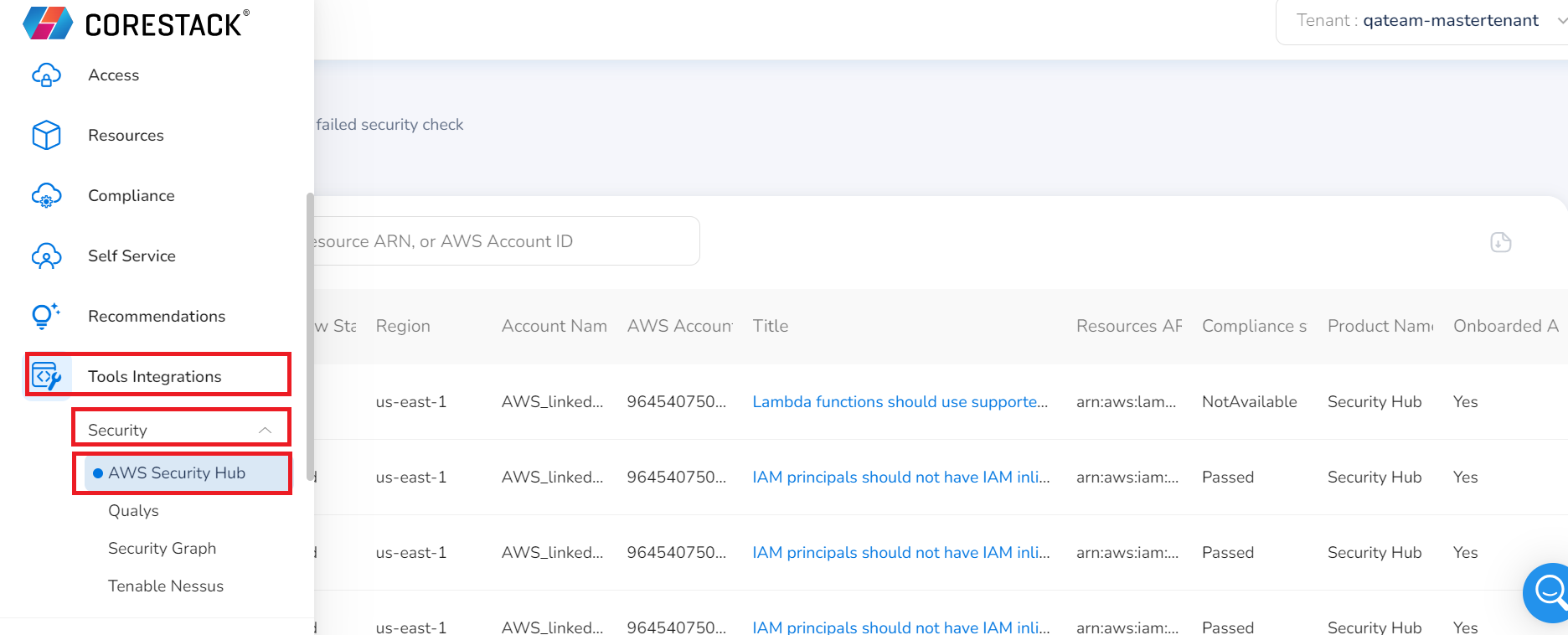
The next screen shows the findings related to your AWS cloud accounts. You can view severity, workflow status, region, cloud account name, whether the cloud account was onboarded or not, AWS account ID, compliance status, etc.
- Click on a title corresponding to a row to view the finding ID, severity, recommendations, workflow status, AWS account ID, created date, updated date, company name, product name, etc. You can expand the sections at the end of the screen to view additional details.
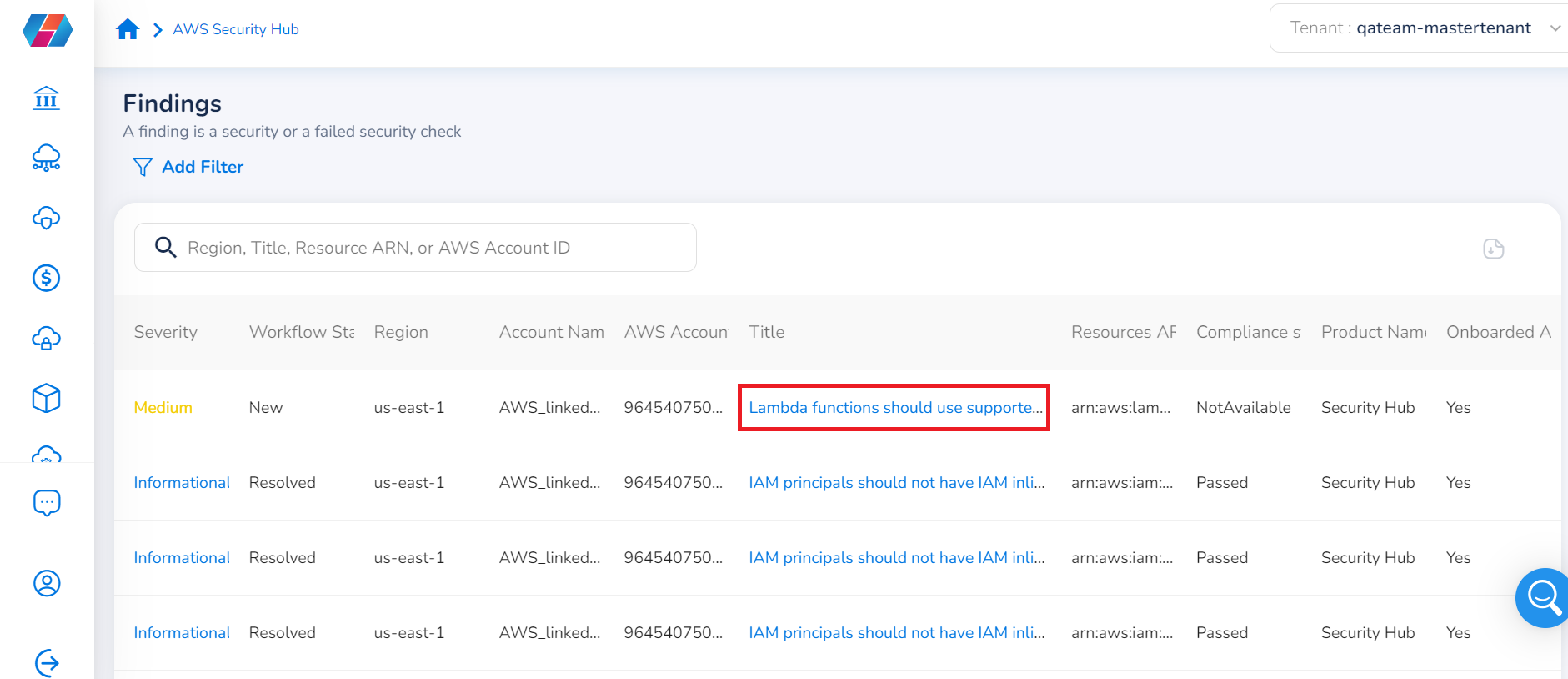
- Click the square download icon on the top-right corner of the screen to download the findings.
The security findings can be downloaded in .CSV format, and a maximum of 50,000 records can be downloaded at once.
Note:
- You can select the columns you want to view in the findings list and can readjust the columns.
- You can also use the Add Filter option and apply additional filters like Cloud Account, Severity, Product Name, Region, and Resource ARN, to refine the findings.
Notification for AWS Security Hub
The Notifications section of AWS Security Hub can be configured to send summary emails to configured users or trigger webhook(s)/Teams webhook(s). The Notifications section appears only if permission to integrate with Security Hub is validated successfully and saved. For accounts that are not integrated with Security Hub, this notification configuration cannot be done.
The notification summary sent to users provides information about the total new findings in Security Hub for the specified cloud account. It includes the split of different products by severity (critical/high/medium/low). It also informs users about the number of findings that were archived since the last sync date. These notification emails are sent every 24 hours after the data sync with the source is completed.
Configuring Notifications
Perform the following steps to configure emails for notification:
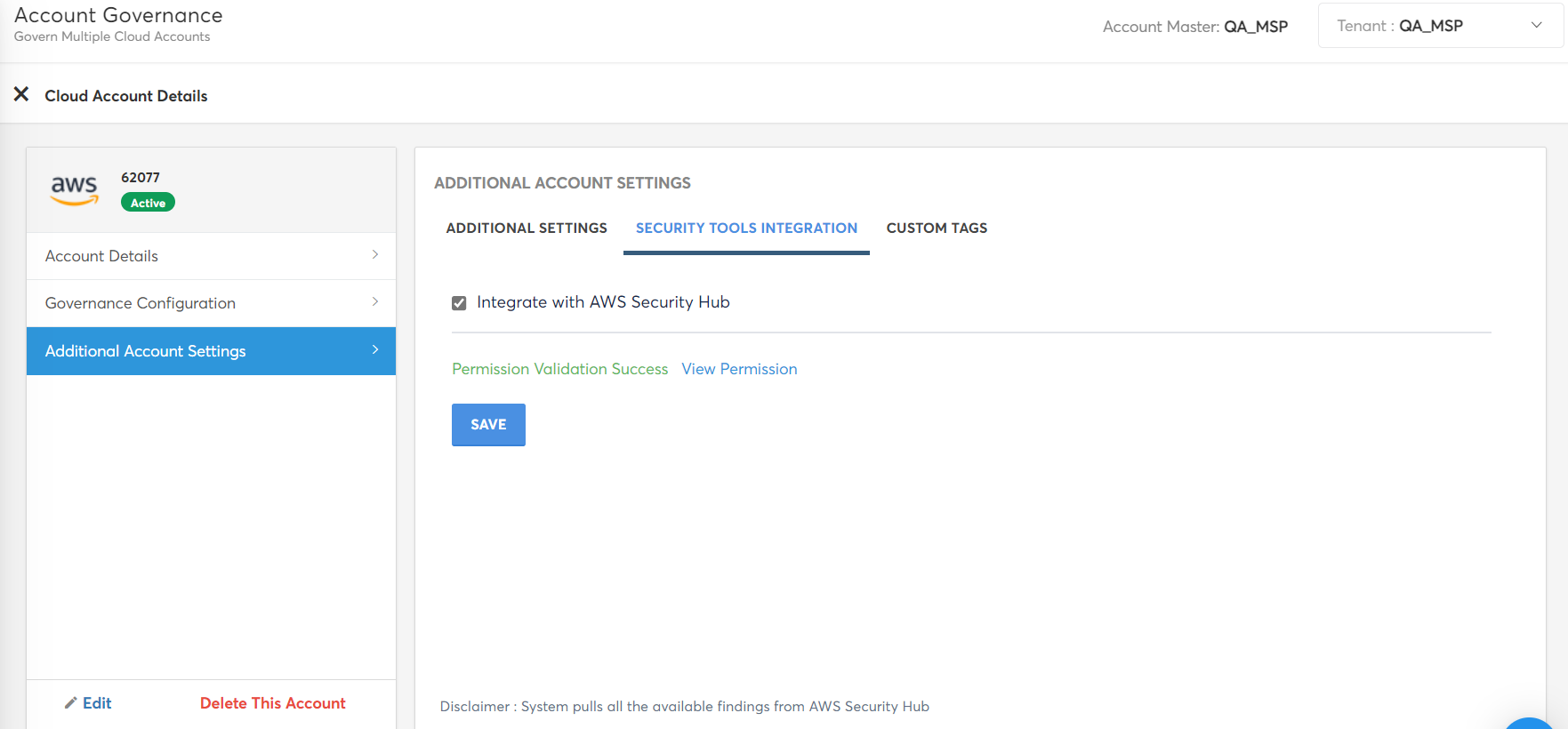
- Navigate to the Account Governance dashboard and browse to your desired AWS cloud account, then select VIEW > VIEW SETTINGS. The Cloud Account Details page should appear.
- On the Cloud Account Details page, select Additional Account Settings from the left menu then select the Security Tools Integration tab.
- Click CONFIGURE. The NOTIFICATION SETTINGS section appears.
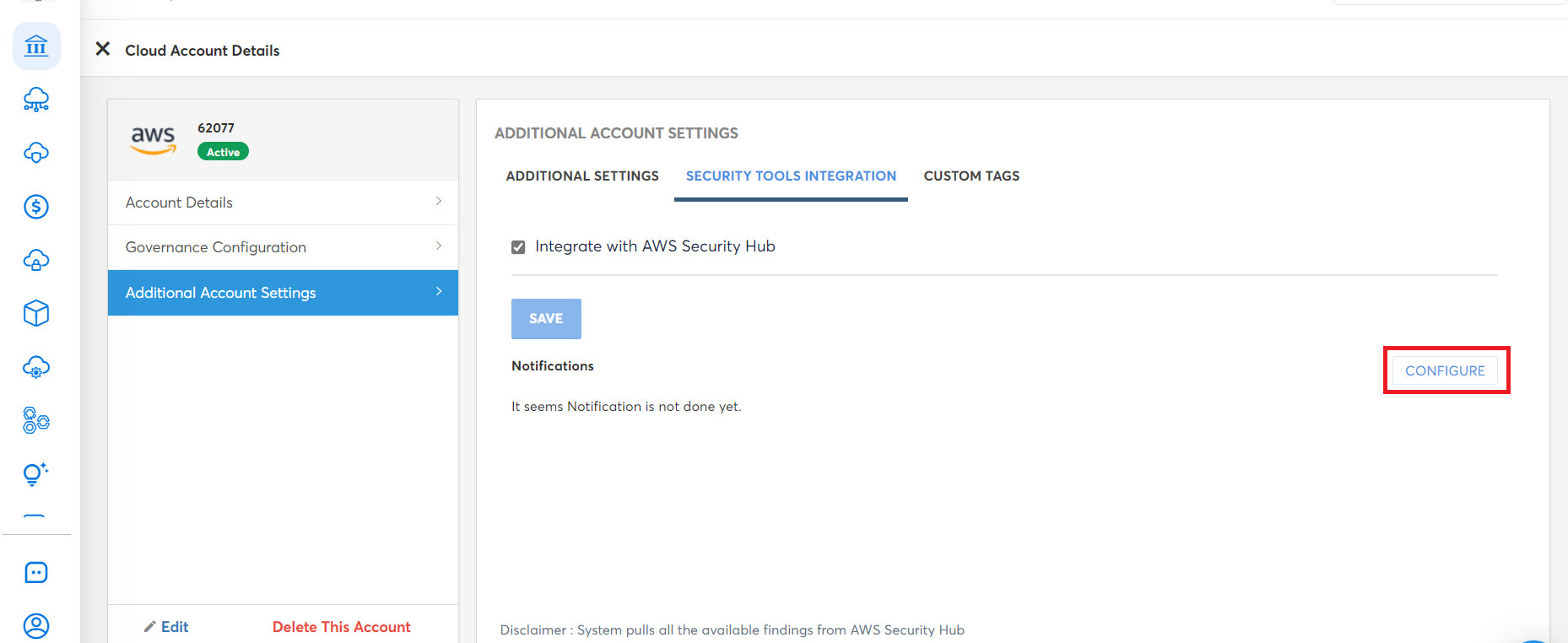
- In the Email Address box, type the email address of the recipient. You can enter up to 50 email IDs in this field.
- In the Webhook box, type the relevant webhook. You can enter up to 20 webhook links in this field.
- In the Microsoft Teams Webhook box, type the Microsoft Teams webhook. You can enter up to 20 webhook links in this field.
- Click to select Exclude My Email Address checkbox if you do not wish to receive the notification email.
- Click Save & Apply.
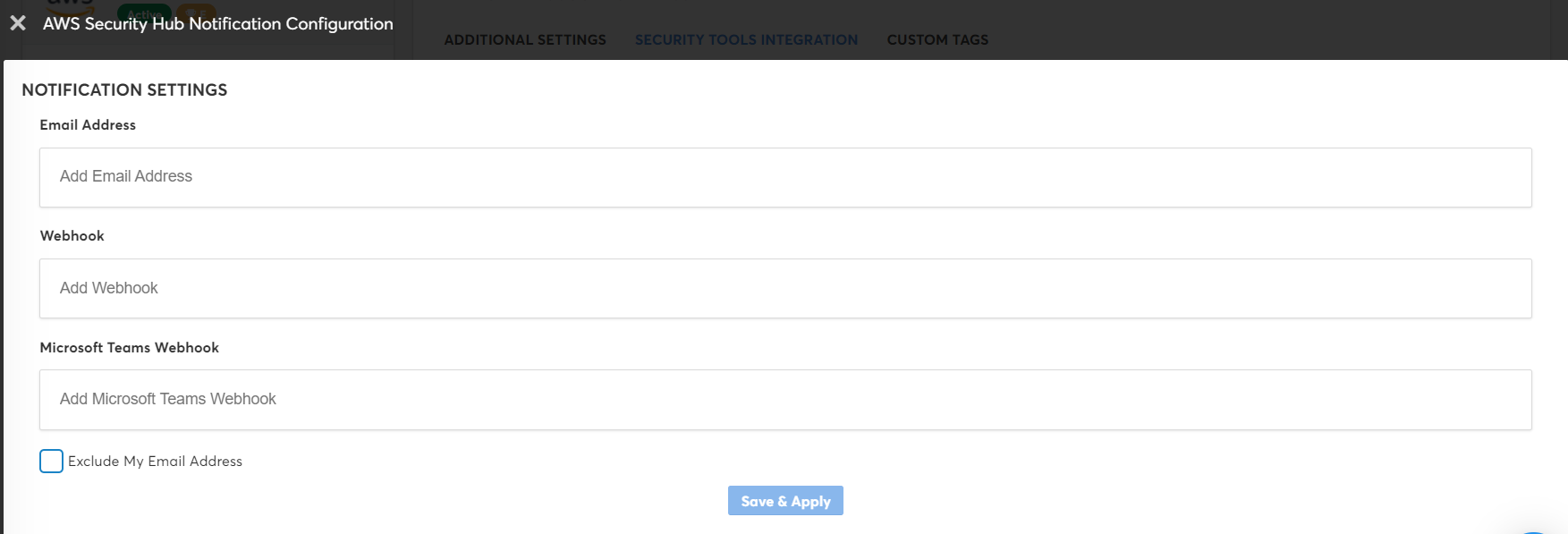
The saved details are displayed in the Notifications section as shown below.
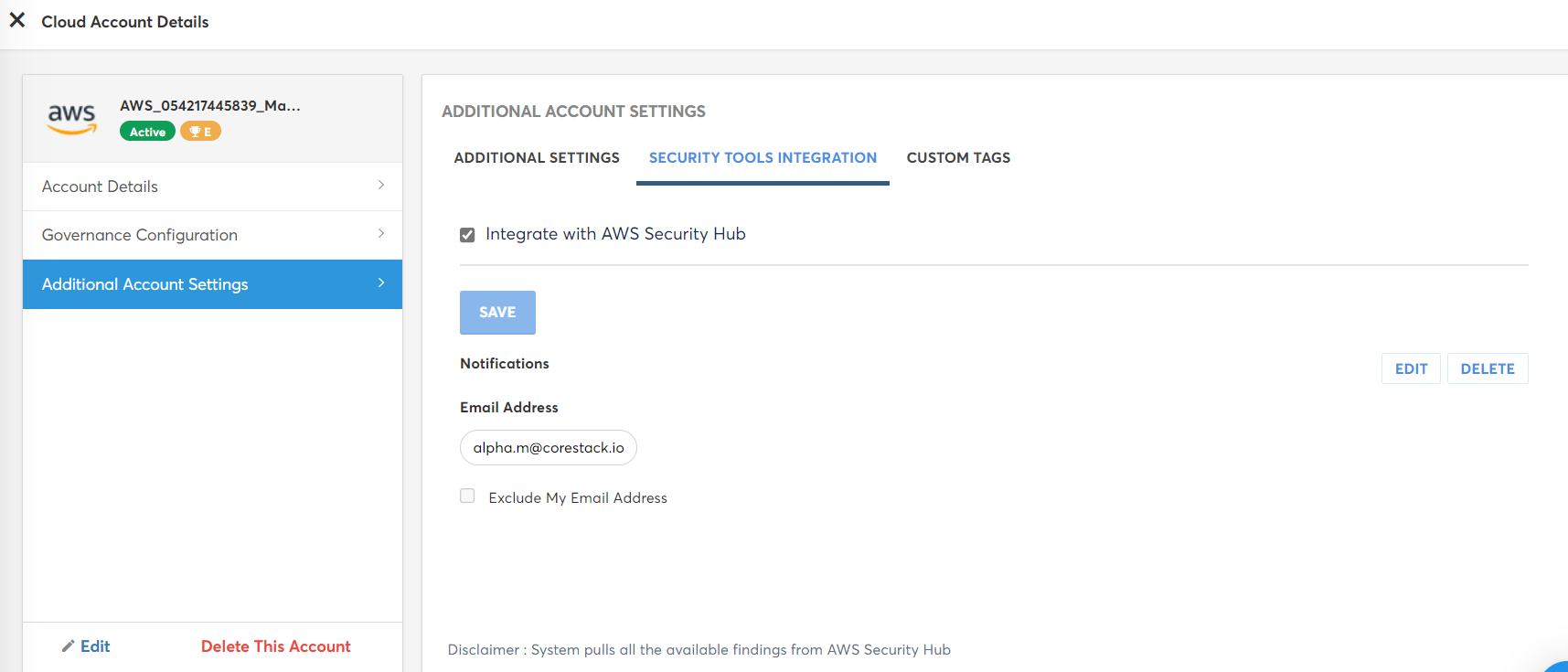
- Click EDIT to update any existing details and click DELETE to delete the notification configuration.
Roles
Users with the following out-of-the-box roles can configure or edit Security Hub notifications from the Account Governance screen:
- Account Admin
- Compliance Admin
- Security Admin
- Partner Service Admin
- Tenant Admin
- Provider Admin
- Delegation Admin
- Workload Owner
Updated 3 months ago