Post-Onboarding Overview
This section covers how to validate your cloud accounts and configurations after onboarding.
Introduction
Once you have completed adding your cloud accounts into the platform, you can see them listed as part of the Account Governance Dashboard.
As a next step, you can check if your cloud account is ready for Assessment and understand the status of the assessment. The process may take 12-24 hours from the time the account was on-boarded or a Re-Assessment is triggered.
The process involves the below stages for each of the 5 OSCAR Governance Pillars:

You can view the current status of your cloud account from the Account Dashboard. The status can be different for each of the 5 Pillars (Operations, Security, Cost, Access and Resource). You can view the status by hovering on the info icon next to colored circle for each pillar.
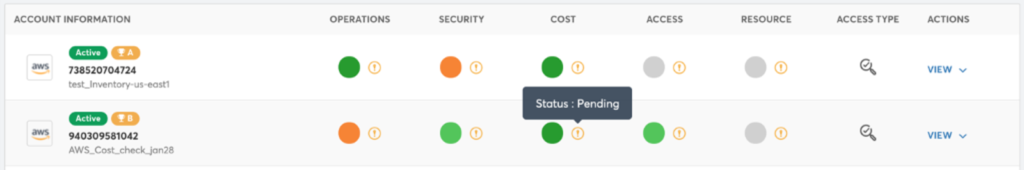
For more information on the Assessment Status and the Results for your account, you can click on view under the Actions column and select View Settings. Complete information about the account and the assessment status is available here. Refer the Account Dashboard section for more details.
Note:You may see status as “Currently Unavailable” for few pillars if the assessment feature is not yet available.
Updated 4 months ago