Pre-Onboarding for GCP Linked Project Accounts
Introduction
This user guide will explain how to perform the pre-onboarding steps required for onboarding a GCP Linked Project account into the platform.
Pre-onboarding (Read-Only)
There are certain prerequisites that need to be set up in your GCP project before it can be onboarded into the platform.
- We need to onboard a GCP Billing account before proceeding to onboard the Linked project.
- All the costs will be fetched from the billing account and the metadata sync for all the projects linked to this billing account will take 24 hours to be completed.
Note:
- The sync of the cost data will take 24 hours to reflect in the platform.
- We will be able to onboard the linked project account only after the sync is completed.
API Access
- In GCP, enable API Access for the Cloud Resource Manager API, Recommender API, Cloud Billing API, and Compute Engine API in the API & Services – Library screen.
Pre-Onboarding Steps in GCP Console
Perform the following steps to onboard GCP Linked Project - Read-Only Access:
- Sign in to the GCP console: https://console.cloud.google.com.
- Sign in to your organization’s cloud account with a user ID and a password.
- Click the icon for Command Line Interface as shown in the image below.
- On the Cloud Shell Terminal screen, clone the GitHub repository by running the below command in a specific folder.
git clone https://github.com/corestacklabs/Onboarding_Templates.git
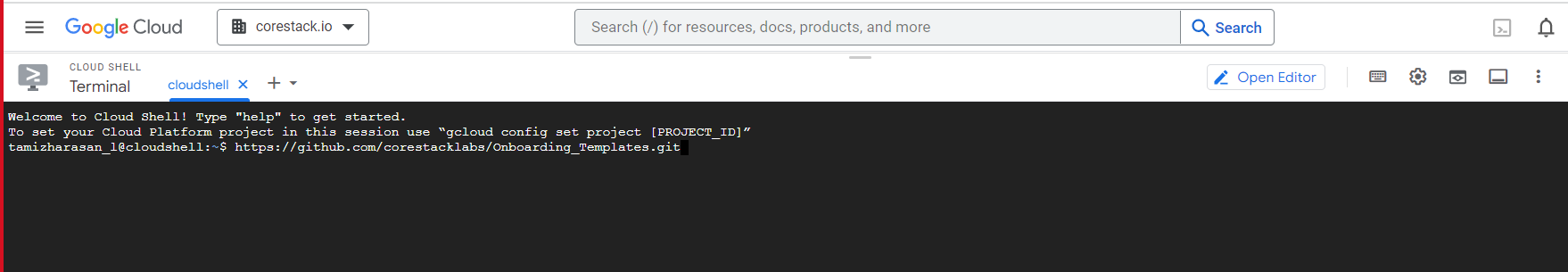
The repo is now downloaded.
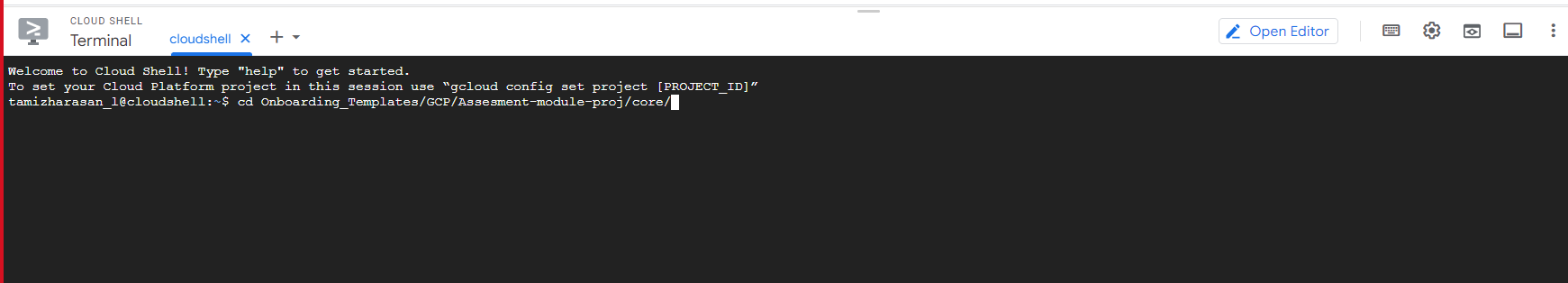
- To switch to a particular directory, use the command provided below.
cd Onboarding_Templates/GCP/Assesment-module-proj/core/
Before starting, be sure to collect the following values that will be requested when run.sh is executed:
- Project ID
- The service account email that is created during the onboarding of a Billing account.
- Role ID (Optional)
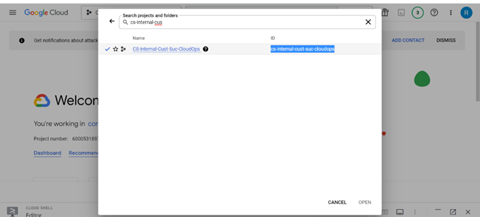
To get the Project ID, click on the drop-down menu before the search box.
You should see the Project ID in the ID section. Select and copy it.
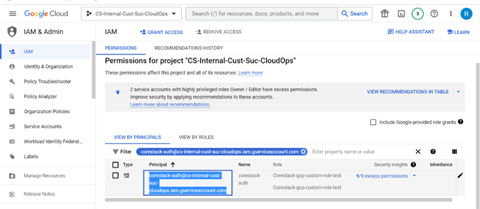
To get the email ID for the service account, navigate to the IAM section and search for the service account by name: for example, “$serviceaccount_abcd@$project_id.iam.gserviceaccount.com”, then copy the email ID.
The Role ID will only be requested if you enter ‘No’ for the “Assign predefined role” condition. Since it requires a user input, be sure to follow the regular expression rules: "^[a-zA-Z0-9_\\.]{3,64}$"
Executing Terraform in the Cloud Shell console
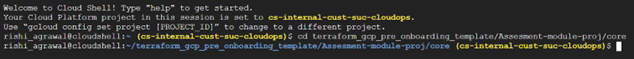
Next, start the Cloud Shell console and navigate to the following directory:
cd Onboarding_Templates/GCP/Assesment-module-proj/core
After this, run the following command in the directory:
chmod +x run.sh
This will make the script executable by the user.
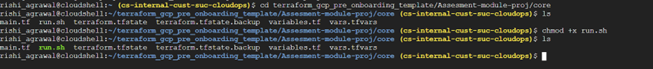
Next, run the following command:
sh run.sh
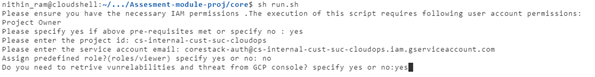
You will be asked whether you have the necessary permissions or not as part of the pre-check condition.
If you enter ‘No’, the script will terminate with exit code 0.
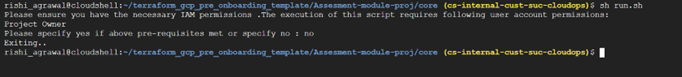
If you enter ‘Yes’, it will ask for further input: Project ID and service account email ID.
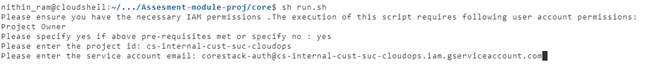
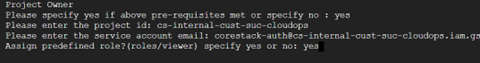
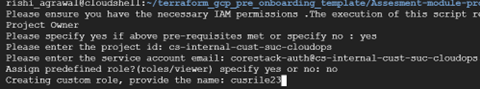
After this, users will be asked whether or not they want to provide GCP predefined roles or not:
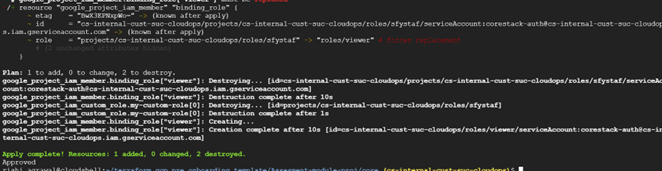
If you enter ‘Yes’, Terraform will take all the pre-defined roles that can be seen in the following screenshot.
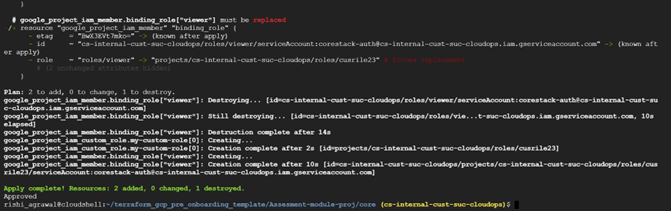
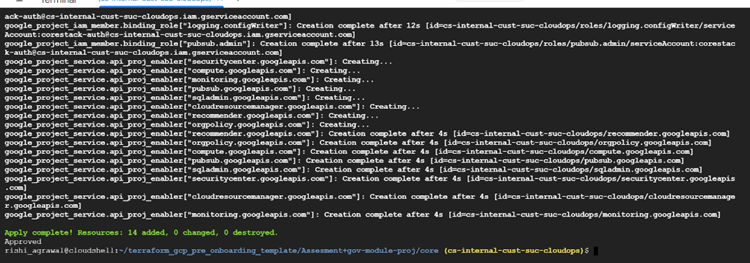
All the provisioning steps will be executed by Terraform, which you can see in the terminal.
Users will then be prompted to get the vulnerabilities and threats from the GCP console
If you enter ‘No’, you will be prompted to give the input for the Role ID, which should follow the regular expression pattern: "^[a-zA-Z0-9_\\.]{3,64}$"
This role is configured as part of the least permissions required by CoreStack to function.
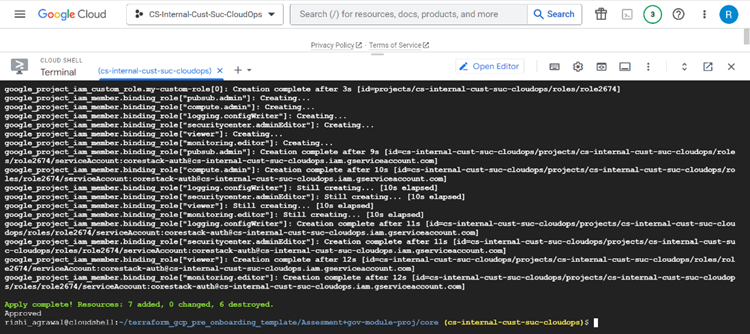
The Terraform execution will start, and you should be able to see the execution flow in the terminal.
Pre-onboarding (Read-Write)
There are certain prerequisites that need to be set up in your GCP project before it can be onboarded into the platform.
API Access
- In GCP, enable API Access for the Cloud Resource Manager API, Recommender API, Cloud Billing API, and Compute Engine API in the API & Services – Library screen.
Pre-Onboarding Steps in GCP Console
- We need to onboard a GCP Billing account before proceeding to onboard the Linked project.
- All the costs will be fetched from the billing account and the metadata sync for all the projects linked to this billing account will take 24 hours to be completed.
Note:
- The sync of the cost data will take 24 hours to reflect in the platform.
- We will be able to onboard the linked project account only after the sync is completed.
Perform the following steps to onboard GCP Linked Project - Read-Write Access:
- Sign in to the GCP console: https://console.cloud.google.com.
- Sign in to your organization’s cloud account with a user ID and a password.
- Click the icon for Command Line Interface as shown in the image below.
- On the Cloud Shell Terminal screen, clone the GitHub repository by running the below command in a specific folder.
git clone https://github.com/corestacklabs/Onboarding_Templates.git
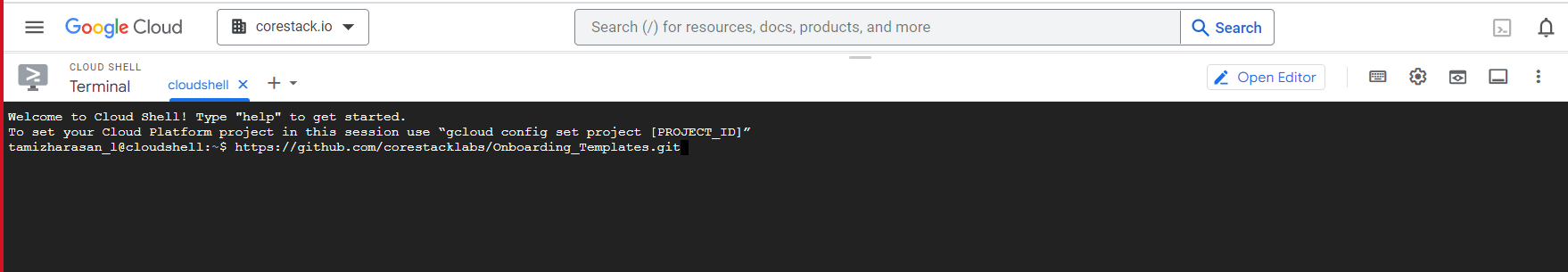
The repo is now downloaded.
Before starting, collect the following details that will be prompted when run.sh is executed:
- Project ID
- The service account email that is created during the onboarding of billing account.
- Role ID (optional)
Perform the following steps to onboard a GCP linked project account with Terraform:
To get the project ID, click the dropdown on the left of the Search box.
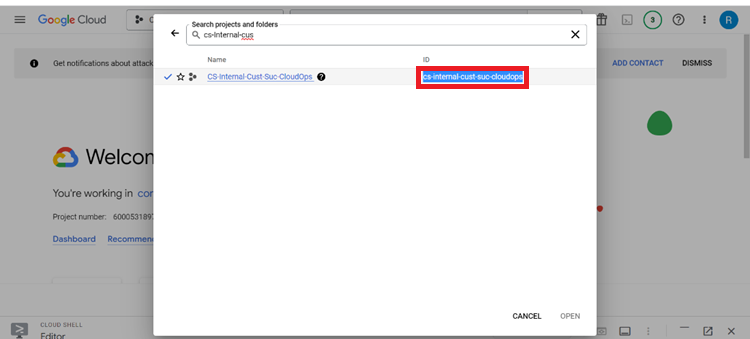
In the ID section, select the project ID and copy it.
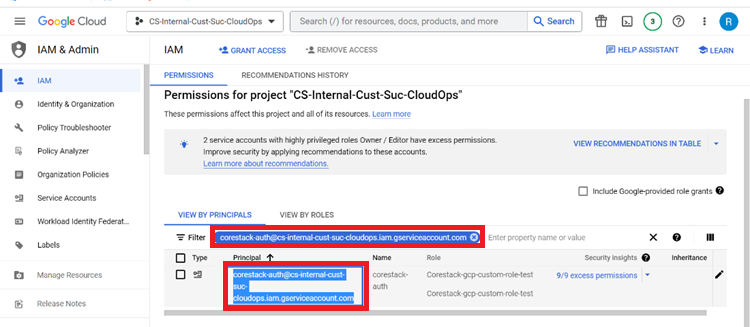
To get the email ID for the service account, navigate to the IAM section and search for the service account by name: for example, “$serviceaccount_abcd@$project_id.iam.gserviceaccount.com”. Copy the email ID.
The Role ID will only be requested if you enter ‘No’ for the “Assign predefined role” condition. Since it requires user input, make sure to follow the regular expression rules: "^[a-zA-Z0-9_\\.]{3,64}$"
Executing Terraform in the Cloud Shell console
Open the cloud console and navigate to the following directory:
cd Onboarding_Templates/GCP/Assesment+gov-module-proj/core
Run this command in the directory: chmod +x run.sh. This will execute the script.
Run the command: sh run.sh
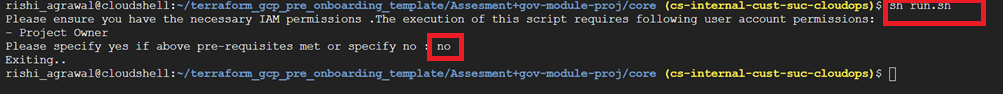
Type either yes or no when prompted for the pre-check condition of whether you have the necessary permissions or not.
If you type no, the script will terminate with exit code 0.
If you type yes, it will ask for further input: the project ID and service account email ID.
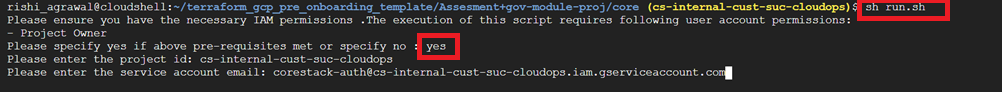
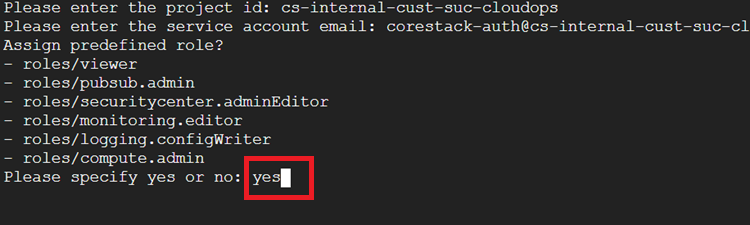
Type yes or no when prompted to provide the GCP predefined roles.
If you type yes:
The Terraform template will take all the pre-defined roles as shown in the screenshot below.
Check the terminal for all the provisioning steps that will be executed by Terraform.
Return to the CoreStack portal and continue with the onboarding process.
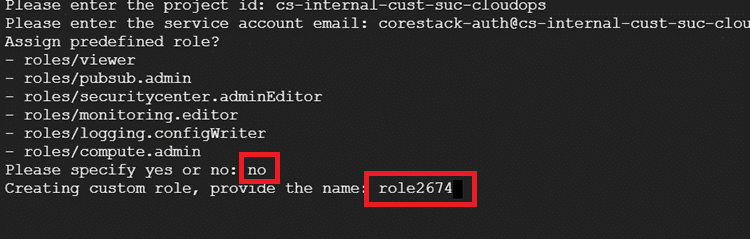
If you type no:
When the prompt asks for the assigned custom role, type the role ID in this format: ^[a-zA-Z0-9_\\.]{3,64}$
This role is configured as the least permission required by CoreStack to function.
Check the Terraform execution flow in the terminal.
Return to the CoreStack portal and continue with the onboarding process.
GCP Billing Impact Due to Onboarding
Refer to the GCP pricing details explained in the table below.
| Area | Module | Resources Created Through the Platform | Pricing | References |
|---|---|---|---|---|
| CloudOps | Activity Configuration | - Cloud Pub/Sub-Topic - Subscription - Sink Router | Throughput cost: Free up to 10 GB for a billing account and $40 per TB beyond that. Storage cost: $0.27 per GB per month. Egress cost: This depends on the egress internet traffic, and costs are consistent with VPC network rates. For details, refer to: https://cloud.google.com/vpc/network-pricing#vpc-pricing | https://cloud.google.com/pubsub/pricing#pubsub |
| CloudOps | Alerts Configuration | - Notification Channel - Alert Policies | Alert Policies: Free of charge. Monitoring: $0.2580/MB: first 150–100,000 MB. $0.1510/MB: next 100,000–250,000 MB. $0.0610/MB: >250,000 MB. | https://cloud.google.com/stackdriver/pricing#monitoring-pricing-summary |
| SecOps | Vulnerability | Need to enable GCP Security Command Center (Standard Tier) | GCP Security Command Center (Standard Tier): Free of charge. | https://cloud.google.com/security-command-center/pricing#tier-pricing |
| SecOps | Threat Management (Optional) | Need to enable GCP Security Command Center (Premium) | GCP Security Command Center (Premium): If annual cloud spend or commit is less than $15 million, then it's 5% of committed annual cloud spend or actual annual current annualized cloud spend (whichever is higher). | https://cloud.google.com/security-command-center/pricing#tier-pricing |
| FinOps | BigQuery Billing Export | Need to enable standard export and create a Dataset | Storage cost for dataset: $0.02 per GB (First 10 GB is free per month). | https://cloud.google.com/bigquery/pricing#storage |
| FinOps | Scheduled Queries | - Daily Scheduled Query - Monthly Scheduled Query - On-demand Scheduled Query | $5 per TB (First 1 TB is free per month). | https://cloud.google.com/bigquery/pricing#on_demand_pricing |
| FinOps | Transferred Billing Data | Storage Bucket | $0.02–$0.023 per GB per month. | https://cloud.google.com/storage/pricing#price-tables |
Note:
These charges are based on the GCP pricing references. Actual cost may vary based on volume and consumption.
Updated 24 days ago