SecOps Maturity Assessment
This user guide explains how to perform a SecOps Maturity Assessment for your cloud account using CoreStack.
Overview
CoreStack can assess your onboarded cloud accounts to identify any security issues as part of SecOps Maturity Assessment Report. The assessment analyzes how your cloud account is performing with respect to various security aspects.
CoreStack has a defined set of assessment scenarios based on your cloud platform, cloud services, and cloud resource types that are available in your cloud account. These assessment scenarios are based on industry standards and best practices, including those recommended by AWS, Azure, and GCP.
Security assessment will include checks for multiple aspects, such as threats, vulnerabilities, config violations, and compliance.
Required Permissions (AWS, Azure, and GCP)
A cloud account must first be configured with the required privileges prior to onboarding the cloud account to perform a SecOps Maturity Assessment.
Read-only access to most services should be sufficient for the SecOps Maturity Assessment.
Account Onboarding
Follow the links provided below for account onboarding:
AWS
Azure
- How to Onboard an Azure Subscription (Pay as You Go)
- How to Onboard an Azure CSP Direct Account
- How to Onboard an Azure CSP Subscription
- How to Onboard an Azure EA Subscription
GCP
Report Generation after Onboarding
Upon successful onboarding of a cloud account, threat and vulnerability data gets synced from cloud provider’s native tools to CoreStack. This information can be viewed on Security Posture and the same information will be part of Security Maturity Assessment Report. Threat and Vulnerability data has latency of up to 14 hours. It takes up to 14 hours to display this data on Security Maturity Report from the time it is initially reported on CoreStack Security Posture.
Perform the following steps to access the SecOps Maturity Assessment Report:
- Click Reports.
- In the Global tab, click Security > SecOps Assessment.
- You can select the required cloud account and view its report(s).
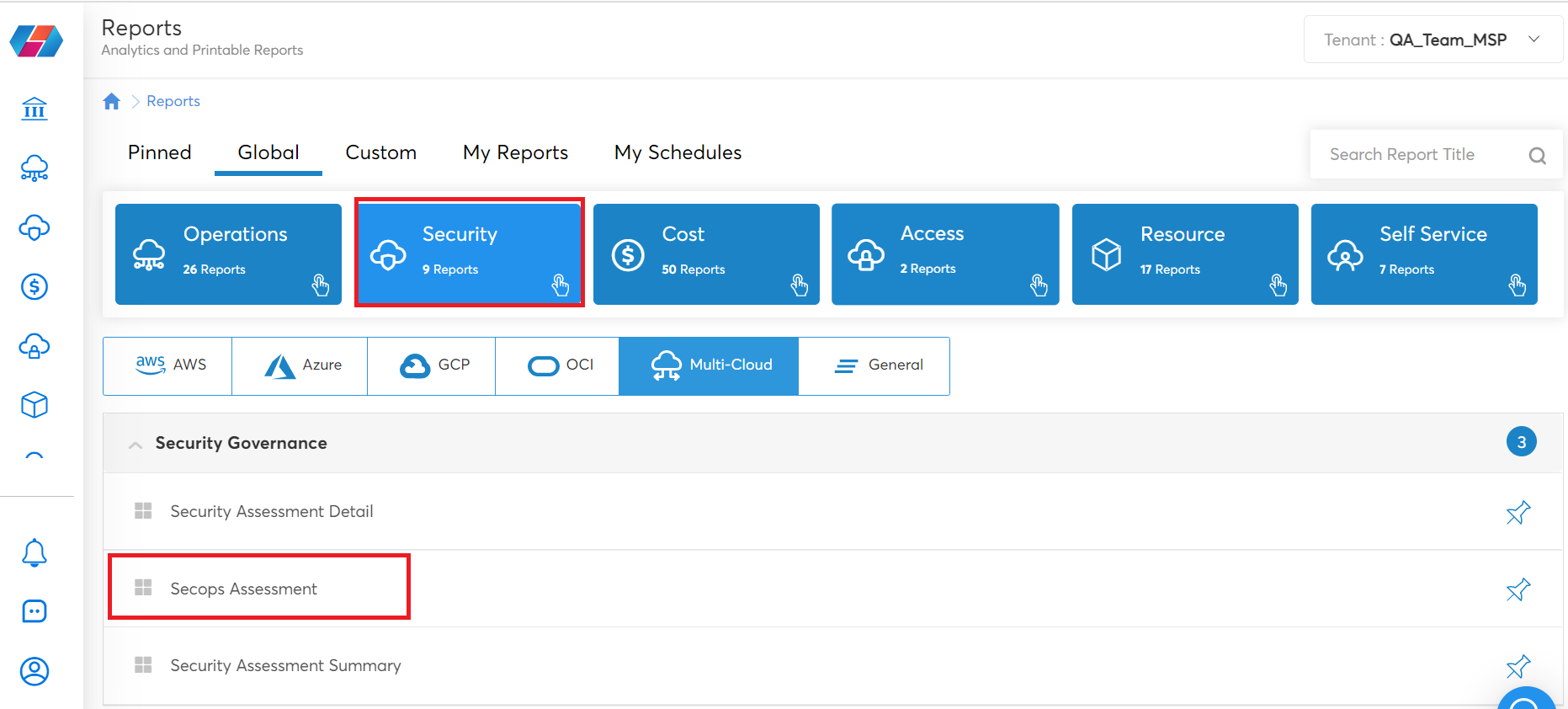
Assessment Reports
CoreStack provides a detailed SecOps Maturity Assessment for the selected cloud accounts. The report summary provides information about each assessment scenario for the selected cloud account. This helps users understand the specific areas where the account requires improvements, and makes recommendations for any necessary next steps.
The Assessment Report shows the following information:
- Executive Summary
- Report Summary with respect to vulnerabilities, threat, config violation, and compliance.
- Deeper Assessment of vulnerabilities, threat, and compliance.
SecOps Maturity Assessment Report
The SecOps Maturity Assessment Report contains the following sections:
- Executive Summary: This page shows the standards compliant, potential threats, and potential vulnerabilities.
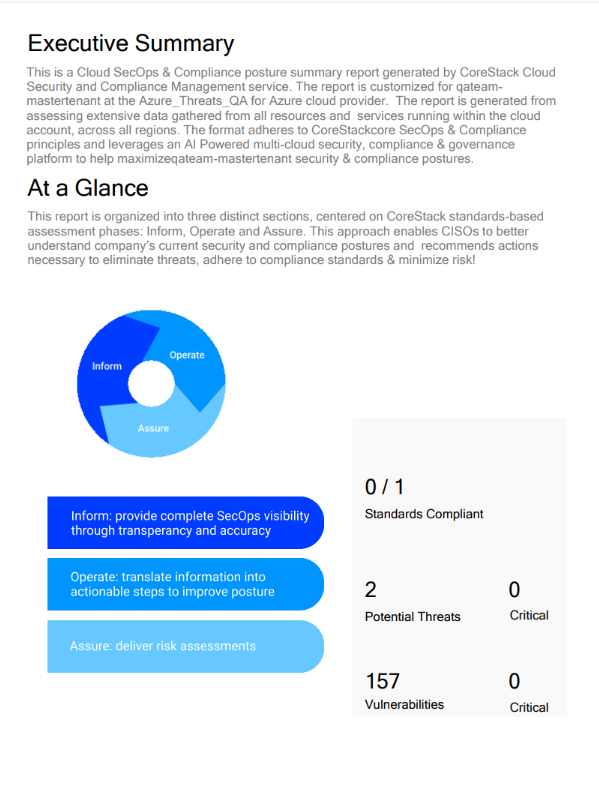
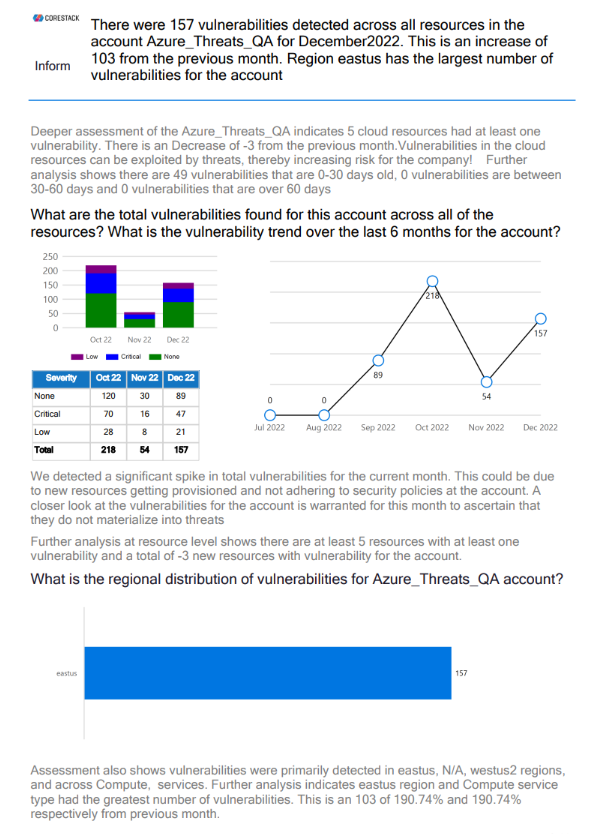
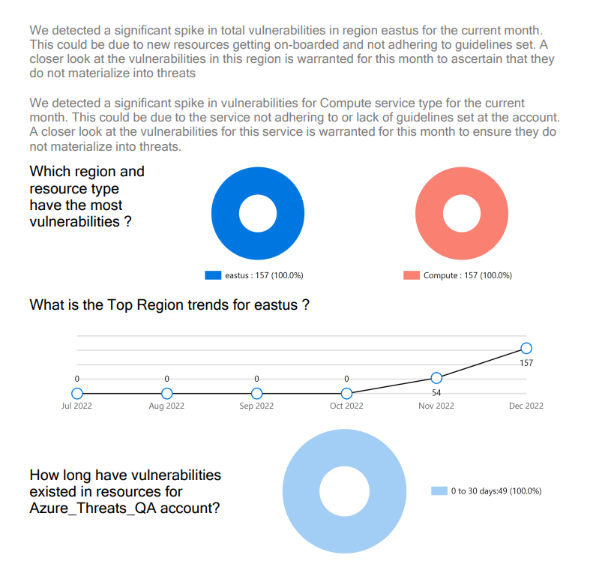
- Report Summary - Vulnerabilities: This page shows the vulnerability breakdown by severity and concentration of high vulnerability levels by region.
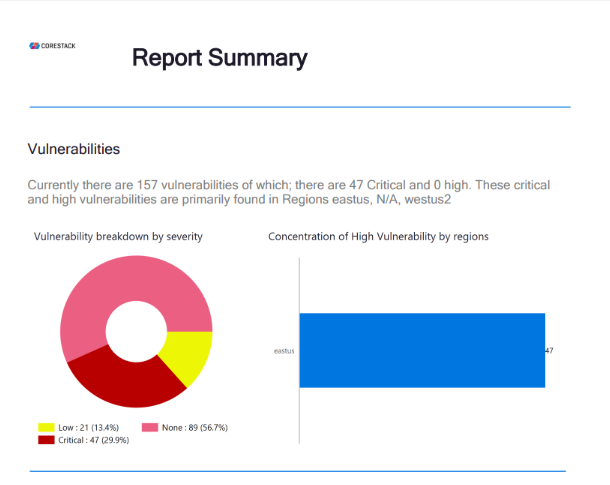
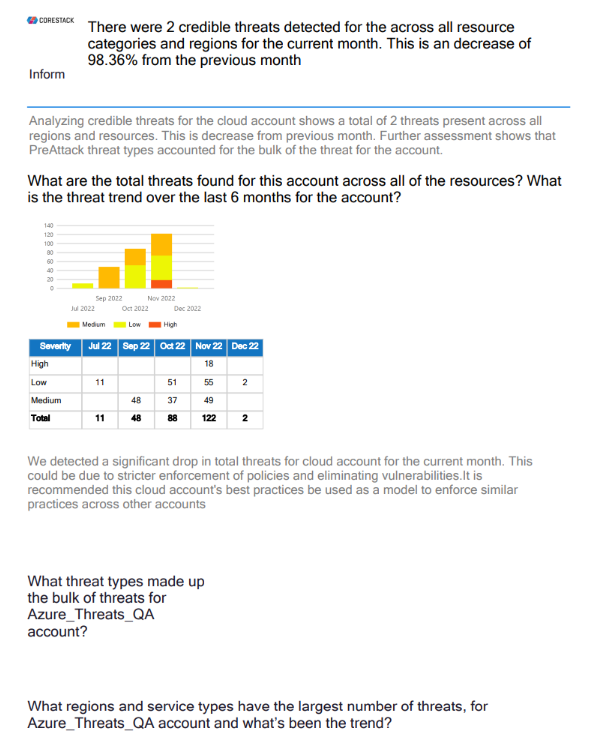
- Report Summary - Threat: This page shows the threat breakdown by severity and concentration of high threat levels by region.
- Report Summary - Config Violation: This page shows the top configuration violations by resource type and concentration of high configuration violations by region. This is same as guardrails that is part of Security Posture.
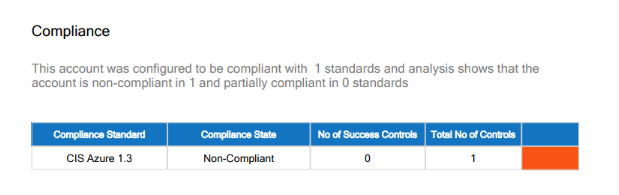
- Report Summary - Compliance: This page shows the compliance standards of the account, compliance state, number of success controls, and total number of controls.
- Deep Vulnerability Analysis: This page shows the total number of vulnerabilities for an account, the regional distribution of vulnerabilities, the vulnerability trend over the last six months, regions and resource types with the most vulnerabilities, the vulnerability trend for a region, and the duration for which the vulnerabilities existed in resources.
- Deep Threat Analysis: This page shows the threats for resource categories and regions in a month, the threat trend over the last six months for an account, threat count, threat types, regions and service types with the highest threats, and the regional threat trend over the last six months.
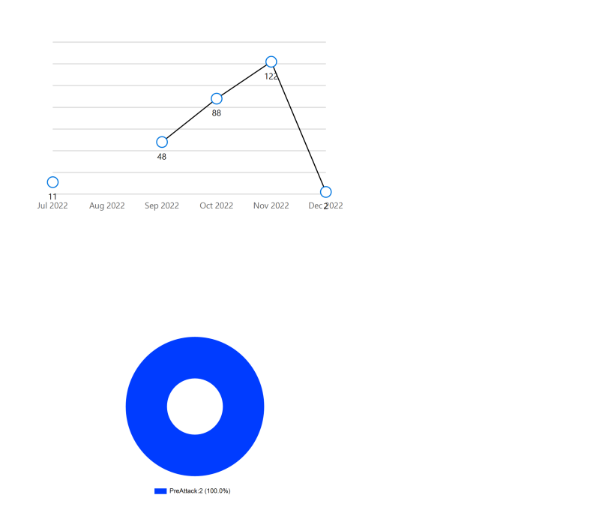
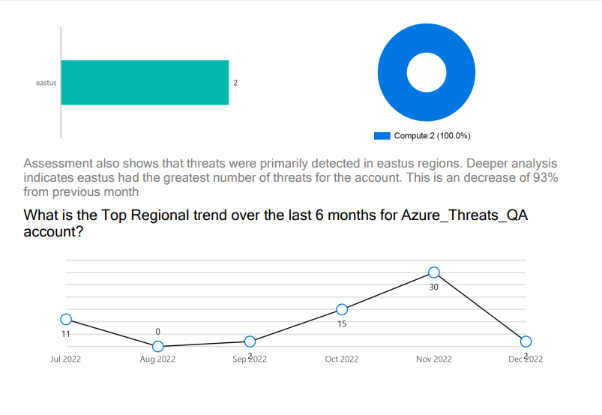
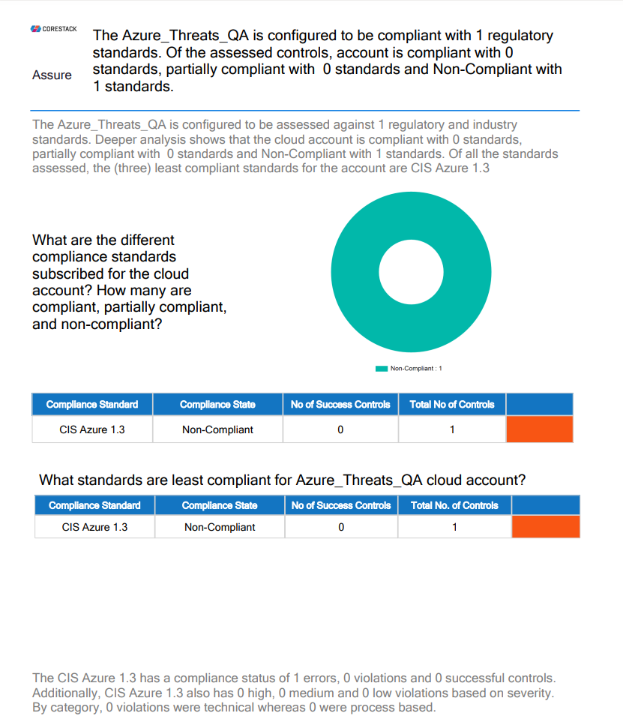
- Deep Compliance Analysis: This page shows a deeper analysis of compliance standards for the cloud account.
Updated over 1 year ago