How to Onboard an AWS Member Account
This user guide will explain how to onboard an AWS member account into CoreStack.
Note:
AWS management and member accounts were formerly known as master and linked accounts, respectively. Some areas in the platform UI may still use the old naming conventions.
This user guide uses the latest naming conventions as per AWS. We appreciate your patience while we update the platform UI to align with this.
Pre-onboarding
There are certain prerequisites that need to be set up in your AWS account before it can be onboarded into CoreStack. It primarily involves creating an IAM Role for CoreStack and providing it with necessary access.
Authorize CoreStack to Access Your AWS Account
You can use IAM roles to delegate access to your AWS resources. With IAM roles, you can establish trust relationships between your trusting account and other AWS trusted (CoreStack) accounts. The trusting account owns the resource to be accessed and the trusted account contains the users who need access to the resource.
Note:
IAM User (Access Key and Secret Key) based authentication is no longer supported. This is in compliance with the security standards and recommendations prescribed by AWS.
CoreStack would use the AWS Security Token Service (AWS STS) “AssumeRole” API operation. This operation provides temporary security credentials that enable access to AWS resources in your account.
Refer this link for more information: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-user.html
Required Credentials:
- Role ARN: The Amazon Resource Name (ARN) of IAM Role.
- External ID: The external ID can be any word or number that is agreed upon between you and the third-party account.
- Require MFA: Flag to identify if the role is restricted with multi-factor authentication (MFA).
The IAM role must be created with the following access permissions.
- For Assessment: Read-Only Access.
- For Assessment + Governance: Read-Write Access.
CoreStack simplifies this process by providing a CloudFormation Template that will take care of creating an IAM Role and assign the necessary permissions automatically.
You can use the S3 URLs provided based on the type of access you wish to provide for CoreStack.
- S3 URL with Template for Assessment Only (Read-Only Access): Click here
- S3 URL with Template for Assessment + Automation (Read-Write Access): Click here
Setting Up the IAM Role
- Login to the AWS account.
- Navigate to CloudFormation.
- Click Create Stack with new resources. The Step 1 screen of Create Stack section appears.
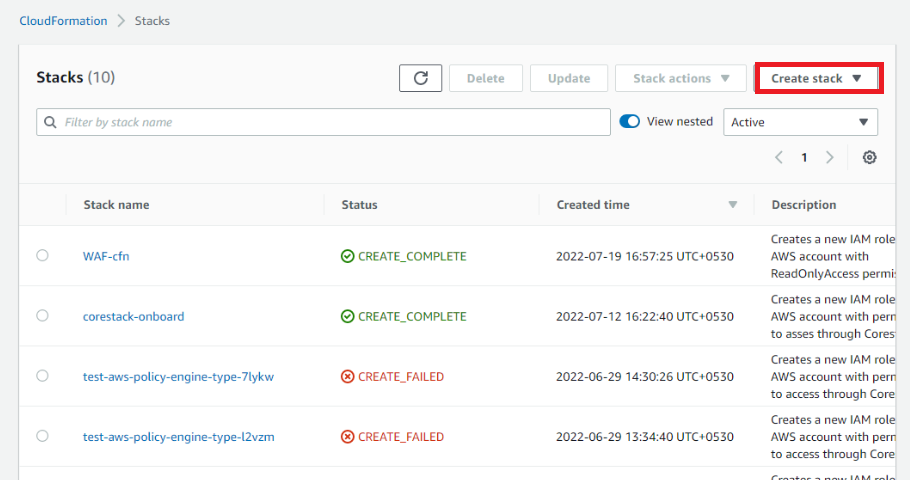
- Select Template is ready option in the Prepare template field.
- Select Amazon S3 URL option in the Template source field.
- Copy the required S3 URL with Template from the above section and paste it in the Amazon S3 URL text field.
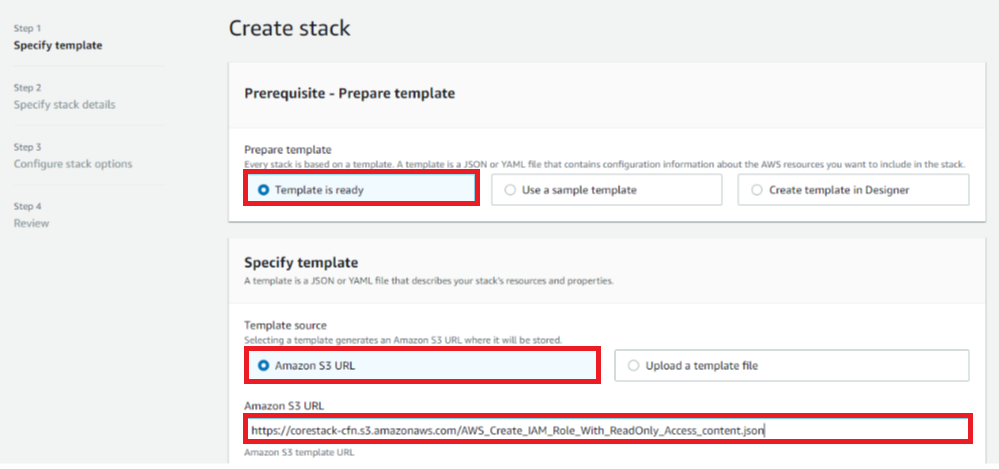
- Click Next. The Step 2 screen appears.
- Provide values for the Stack name and Role name fields. If you have used the Amazon S3 URL with template for Read-Write Access, you can view additional fields that can be left with default values. However, if you do NOT want to configure CFN or GuardDuty or Inspector for your AWS account, you can set them as “false”.
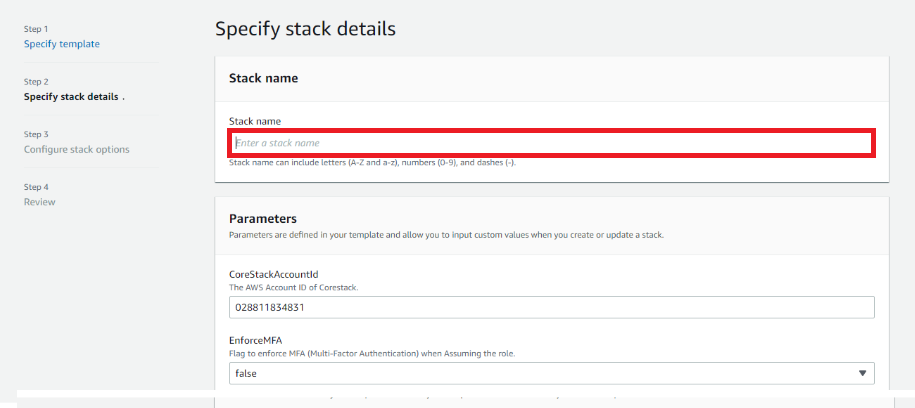
- Click Next. The Step 3 screen appears.
- You can leave the values for the fields in this screen as default or make changes as necessary including assigning Tags, providing notification options, etc.
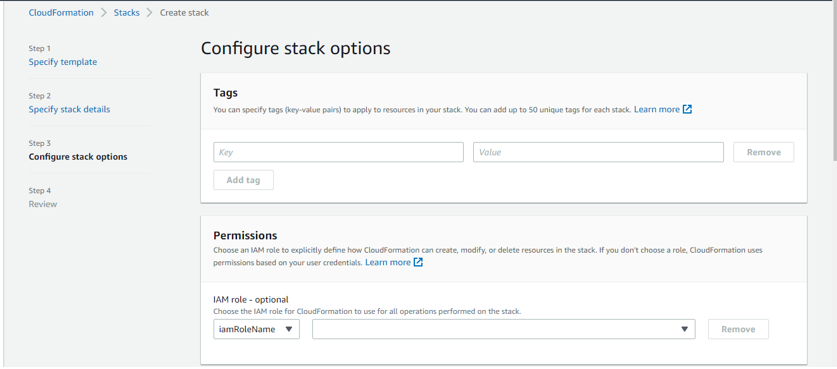
- Click Next. The Step 4 screen appears.
- The information provided in all the steps will be displayed. After reviewing the provided information for correctness, scroll down to the end of the screen and click on the acknowledge checkbox.
- Click Create Stack.
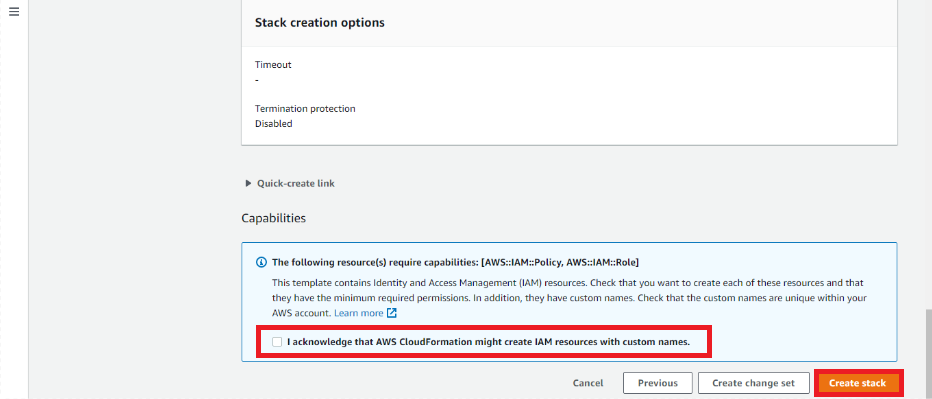
The stack creation process will be initiated, and the status can be viewed.
- Navigate to Stack Info tab to see the overview of the stack and the final status.
- Click Refresh icon to retrieve the updated status. When it is successfully completed, you will see the status as “CREATE_COMPLETE”.
- Navigate to Outputs tab to view the access credentials (ARN).
You need to copy this information and keep it ready in a notepad to be able to copy paste into CoreStack while onboarding. This is the information required to onboard the account into CoreStack.
Setting up Cost Reports
Cost and Usage Report (CUR) must be enabled in your AWS account which enables the platform to fetch the Billing data from your account. This is required for providing Cost Visibility and Cost Analytics for your accounts. If you already have this enabled, you can skip the below step and just be ready with the S3 Bucket name where the CUR files are being placed by AWS.
Note:
AWS used to provide billing data only at the Management (Payer) Account level. From Dec-2020, AWS provides billing data for member accounts as well. If you have onboarded both your management and member accounts, the platform can directly fetch the billing data from the management account for all the member accounts.
To set up the Cost Usage Report, you should login as “Root User” into your management (Payer) AWS account and complete the following steps:
-
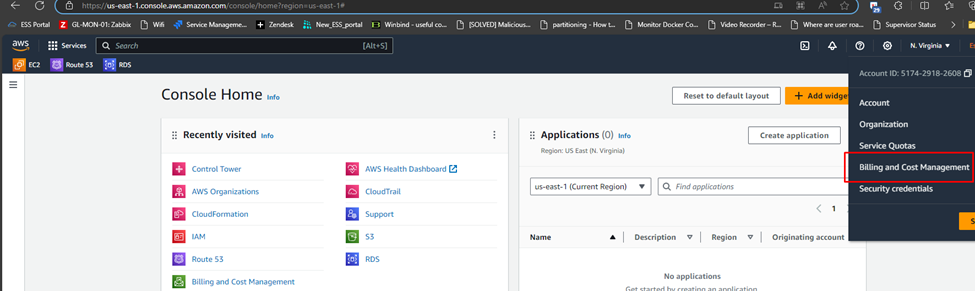
Login to the AWS management account as a Root User.
-
Navigate to Billing and Cost Management.
-
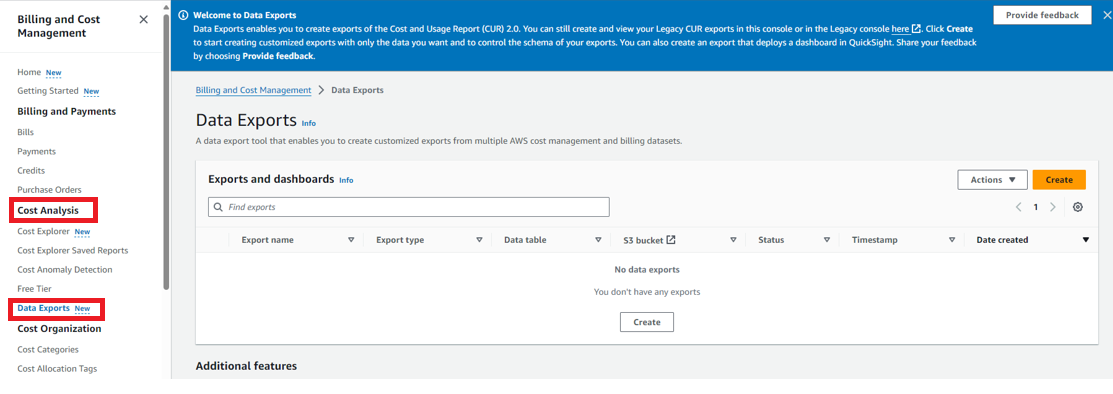
On the left navigation menu, select Cost Analysis > Data Exports.
-
Click Create.
-
In the Export type field, select the Legacy CUR export option.
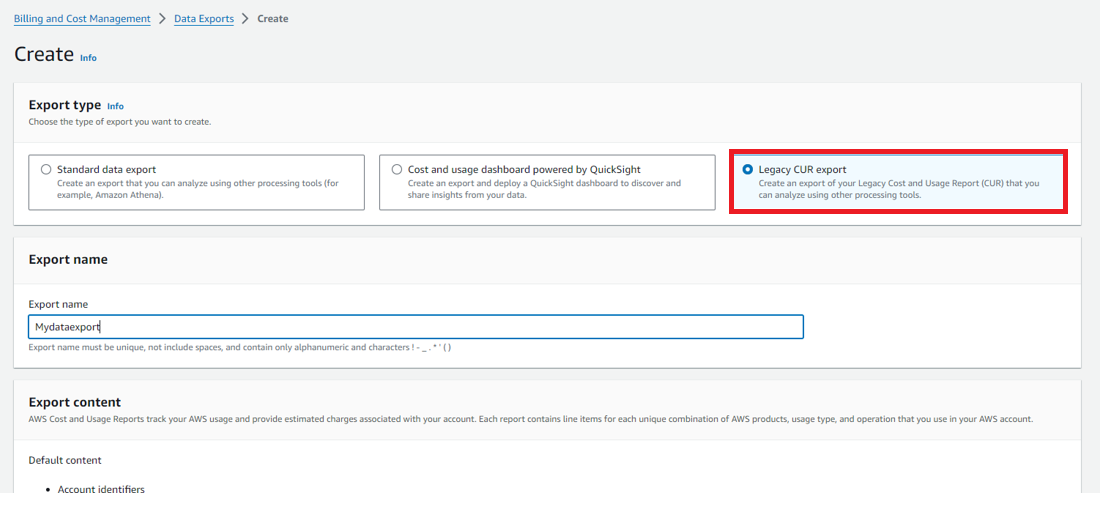
Note:
If you already have a report configured, you can still review the following steps to ensure that all the settings are configured properly. Use the Edit option to make any changes.
- Provide necessary details about the report content in the first step. Ensure that the checkboxes Include Resource IDs and Automatically refresh are enabled.
- Click Next. The screen with Delivery Options appears.
- Select the following values for the respective fields:
- Report Path Prefix: Optional field. It can be left blank. There will be no impact even if some prefix is provided.
- Time Granularity: Daily
- Report Versioning: Create new report version.
- Compression Type: GZIP
- Also, the S3 Bucket configuration must be performed in this step:
- Click Configure.
- If you already have a bucket with the appropriate permissions, you can select the same or you can select Create a bucket (this is recommended).
AWS will take care of creating this new bucket and attaching the necessary policies. - Click Next to view the policy to be applied.
- Enable the checkbox I have confirmed that is available below.
- Click Save to complete the process. The S3 Bucket will be successfully configured.
- Click Next to proceed to the next step.
- The last step is to review the provided values and complete CUR configuration. Ensure that the following values are configured correctly.
- Time Granularity: Daily
- Report Versioning: Create new report version.
- Compression Type: GZIP
- Click Review and Complete.
The report will be created successfully. You can now continue with onboarding the account to the platform. It will take up to 24 hours before AWS places the first report (CSV file in Gzip format) in the S3 bucket. Hence, the cost data will not be available for the platform until then.
Select Cost Allocation Tags
It is mandatory to configure cost allocation tags in order to process the cost data.
To set up Cost Allocation Tags, perform the following steps:
- Navigate to Billing Dashboard.
- Select Cost Allocation Tags from the left navigation menu.
- Click Activate button.
The recommended tags to be activated are: Application, Environment, Cost Center, Owner. You can also choose to add additional tags as per your requirement.
Impact on the AWS Account
Read-Only Access (Assessment Only):
Since the access is read-only, there are no resources with configurations done by CoreStack in your AWS account. There is absolutely no resource or billing impact in this case.
Note:
- If you had enabled Cost & Usage Report specifically for CoreStack, the S3 Bucket will incur some minimal cost based on the size of the usage reports placed by AWS.
- If you had enabled AWS Cost Explorer API to be used by CoreStack for a faster cost data retrieval, additional cost will be incurred based on the API requests initiated. Approximately, each request will incur a cost of $0.01. Refer to AWS Cost Explorer API pricing page for more details.
Read-Write Permissions (Assessment + Governance):
Following resources will be created based on your selection during onboarding:
- Cloud Trail: CoreStack requires a cloud trail to be available in each of your preferred AWS regions. You may select an existing trail to be used or choose the option to create a new trail. Such new trails created may attract additional charges.
Note:
If the one created is the first trail, it is free of cost. If it is an additional trail, it may involve charges.
- S3 Buckets: As part of the Cloud Trail configurations, S3 buckets are also created in the respective AWS regions to collect the logs.
- If you had chosen to use existing trail, there are no new buckets created.
- If you had chosen to create a new trail, the corresponding S3 Bucket will be created and there will be a charge associated.
- CloudWatch Alarms will be created for selected metrics for various resource types supported by CoreStack. As part of post onboarding, you will see the list of metrics for each resource type for which you can define monitoring thresholds and alerts.
Billing Impact due to CoreStack Onboarding
There could be additional charges based on the configuration done for your accounts after onboarding:
| Configuration | Description | Billing Impact |
|---|---|---|
| CloudTrail | Case-1: An existing trail is configured for CoreStack. Case-2: There are other Trails that were created before / after onboarding your account to CoreStack. | Case-1: Charges for the S3-Bucket where the Cloud Trails logs are stored. This is usually very minimal. Case-2: Charges for the S3-Bucket where the Cloud Trails logs are stored. Management event charges for the second trail at the rate of $2.00 per 100,000 events. |
| CloudWatch Alarm | Standard Resolution (60 sec) | $0.10 per alarm metric |
| CloudWatch Metric Data | GetMetricData – CoreStack fetches the metric data from AWS | $0.01 per 1,000 metrics requested |
| AWS Configuration Recorder, GuardDuty Notifications, AWS KMS Keys, AWS Config Policy | These services will be used only for Assessment + Governance access type and it is optional for the user to enable them. If enabled, relevant charges will be applicable. • AWS Configuration Recorder: Used to identify issues in resource configurations. • GuardDuty Notifications: Used for threat detection. • AWS KMS Keys: Used to execute guardrail policies for KMS auditing and finding violations. • AWS Config Policy: Used to execute configuration policies evaluation. | Refer to pricing pages of relevant AWS resources for more pricing details. |
Onboarding
The following steps need to be performed to onboard an AWS account.
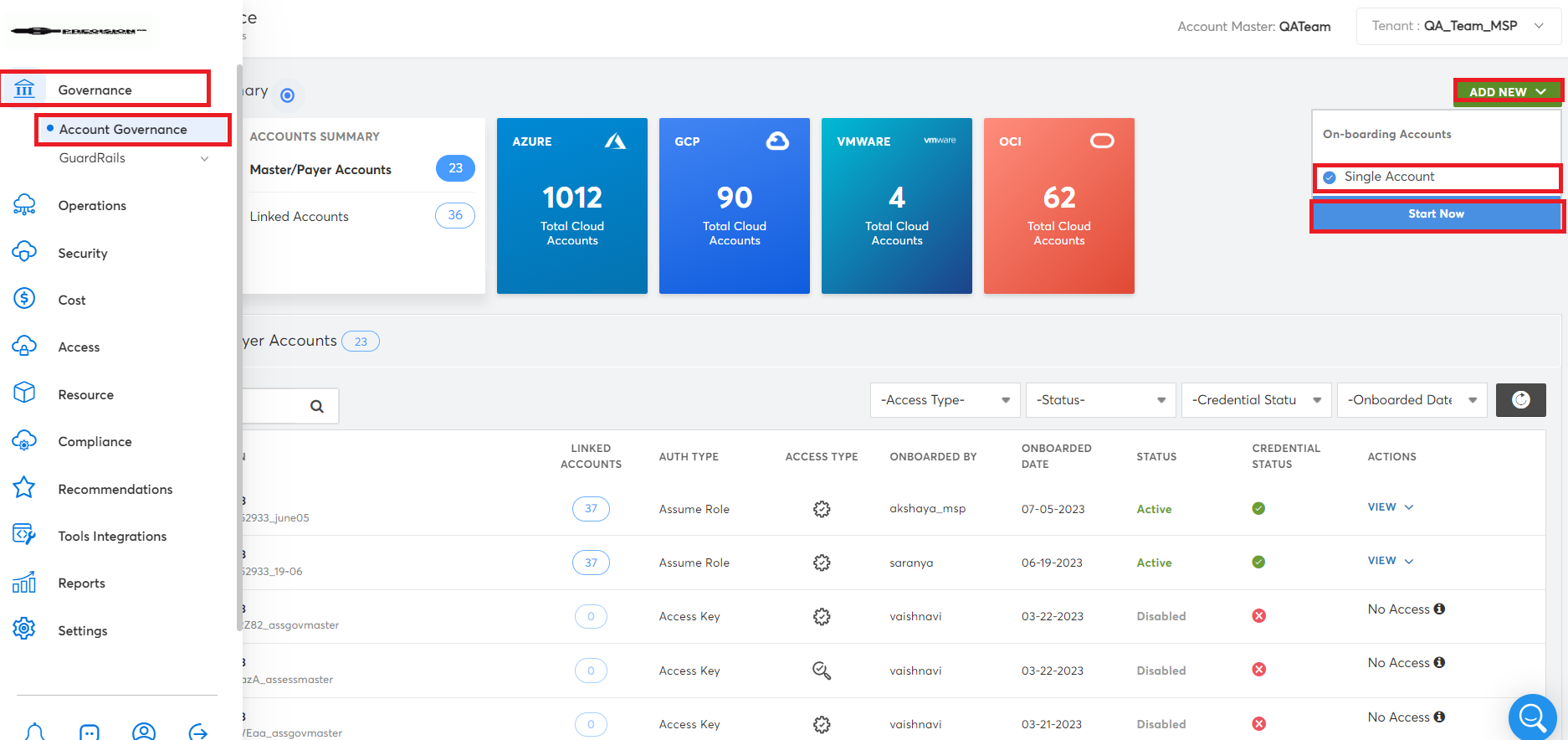
- Click Governance > Account Governance > Add New button in the CoreStack dashboard and select Single Account.
- Click Start Now. The onboarding screen appears.
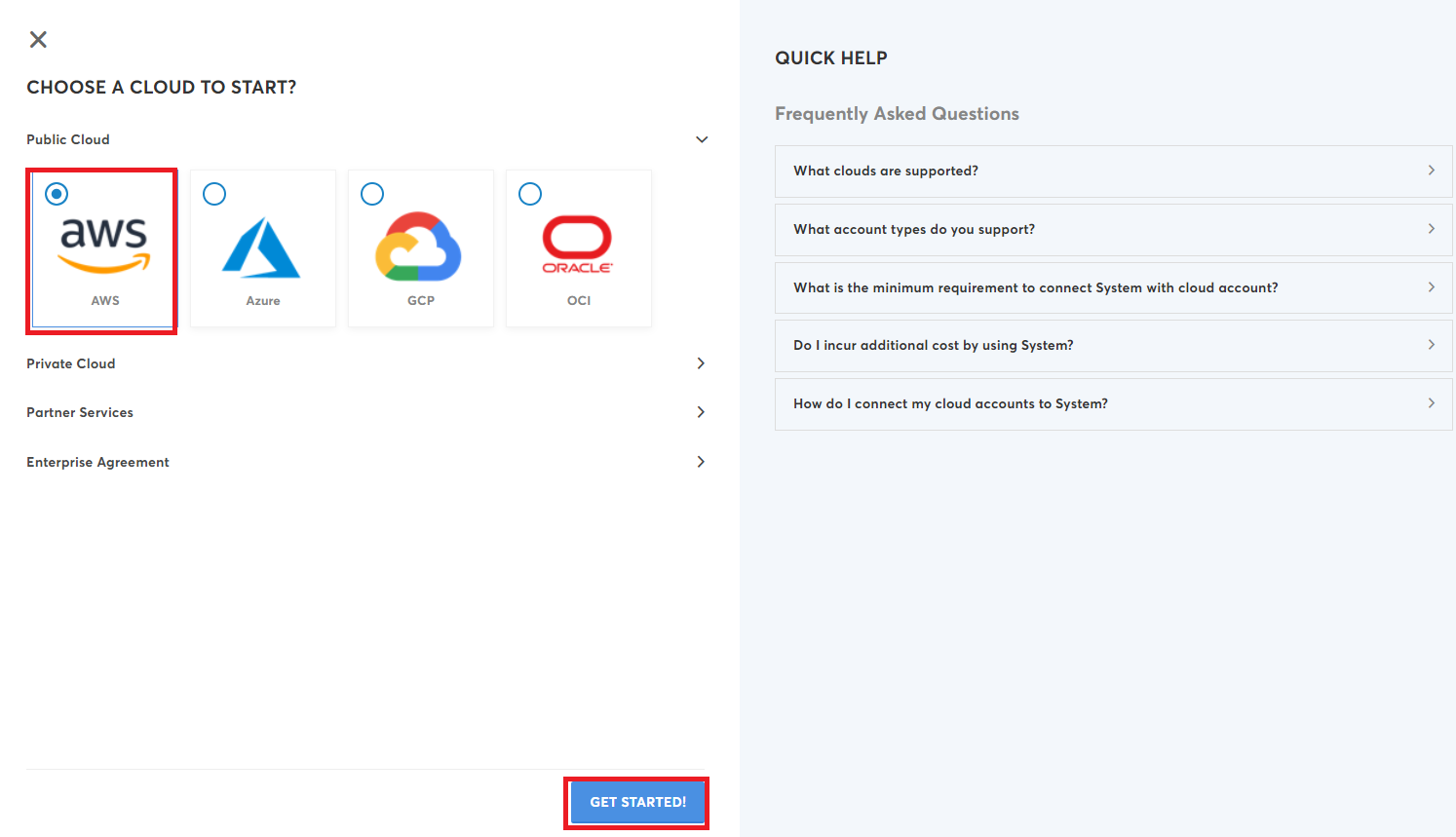
- Select AWS option in the Public Cloud field.
- Click Get Started button.
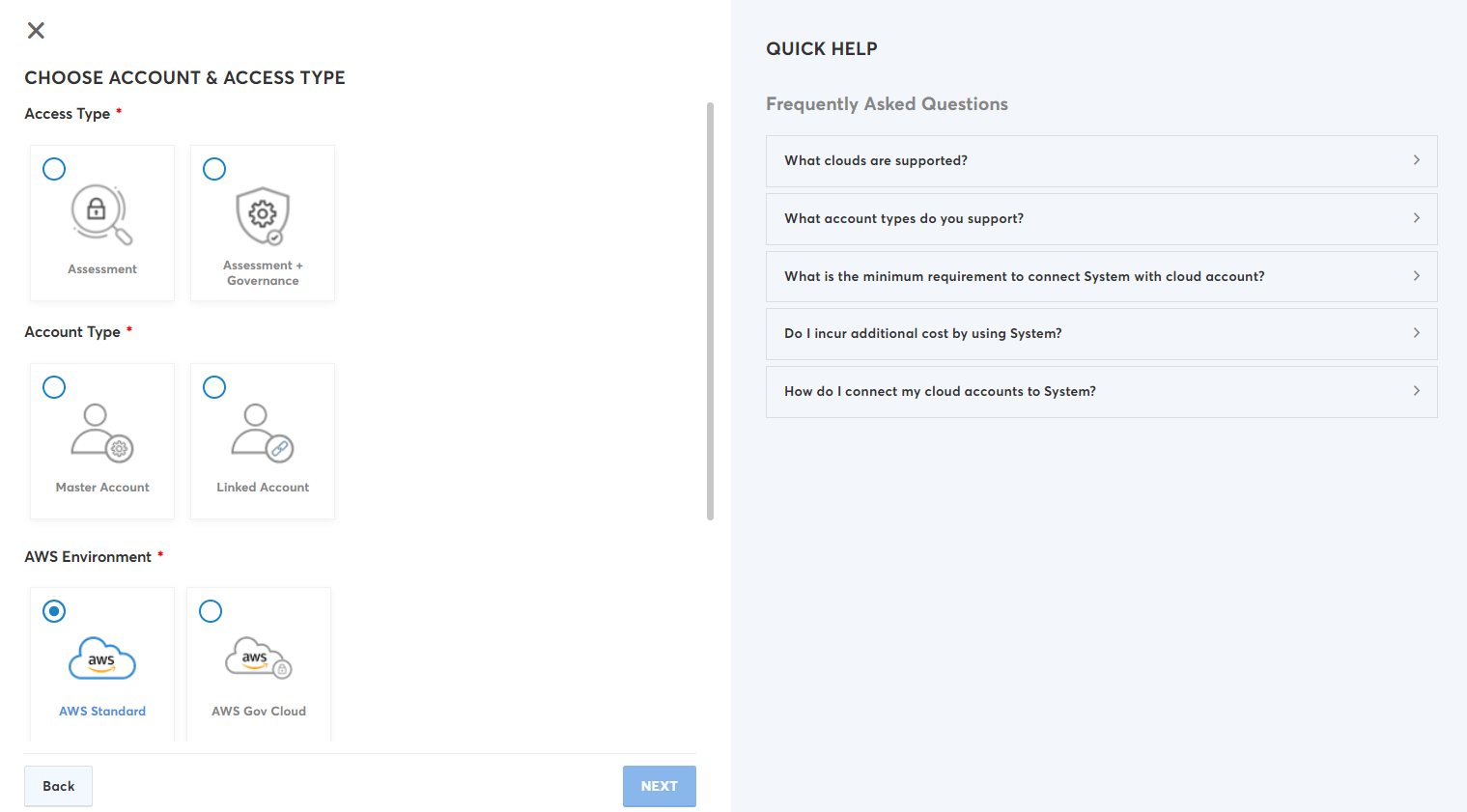
- Select the required option in the Access Type field. The options are: Assessment and Assessment + Governance.
- Select the Linked Account option in the Account Type field.
- Select the required option in the AWS Environment field. The options are: AWS Standard and AWS Gov Cloud.
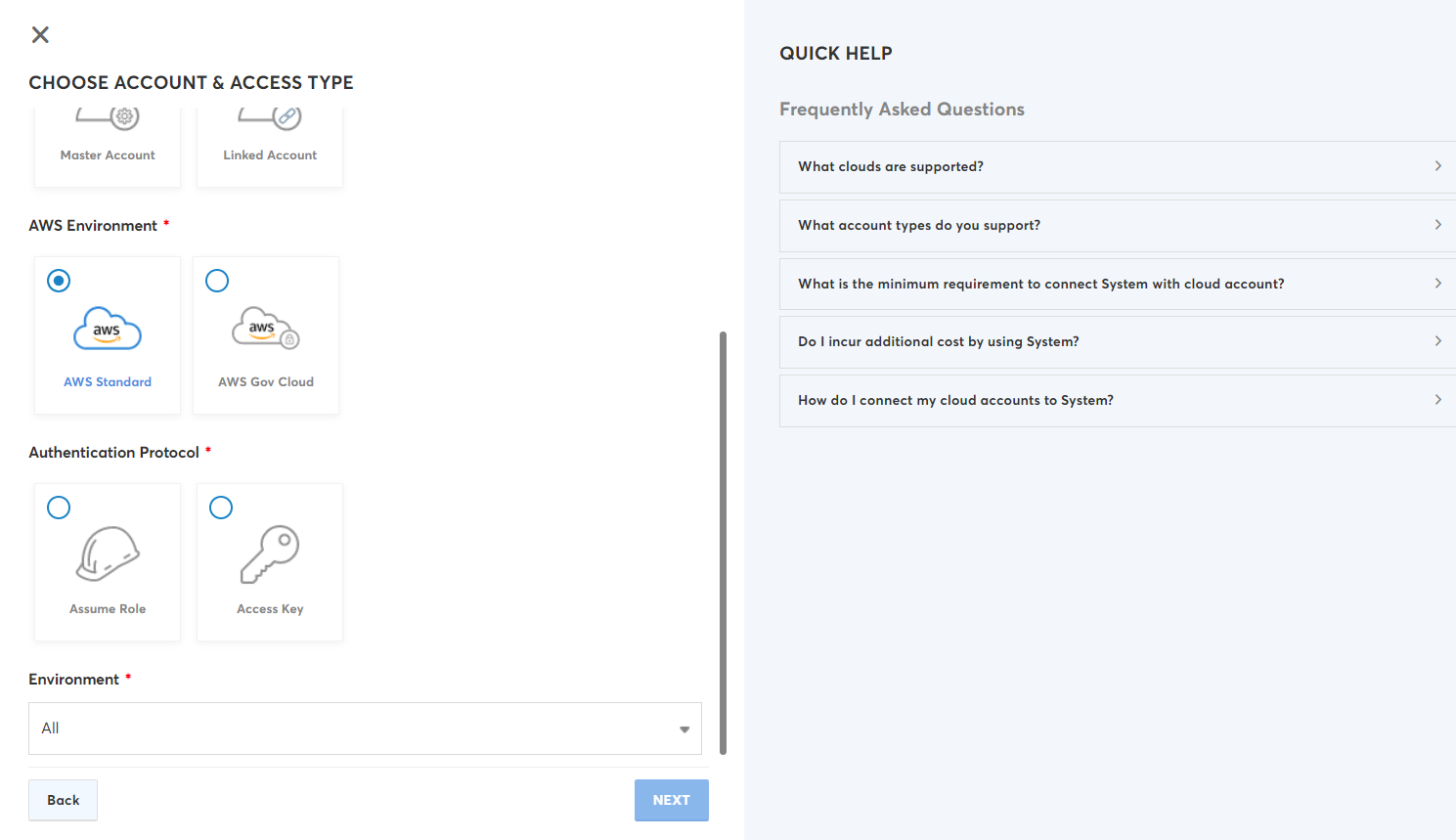
- Select the required option in the Authentication Protocol field. The options are: Assume Role and Access Key.
- In the Environment list, select an appropriate option. The options are: All, Production, Staging, QA, and Development.
- Click Next.
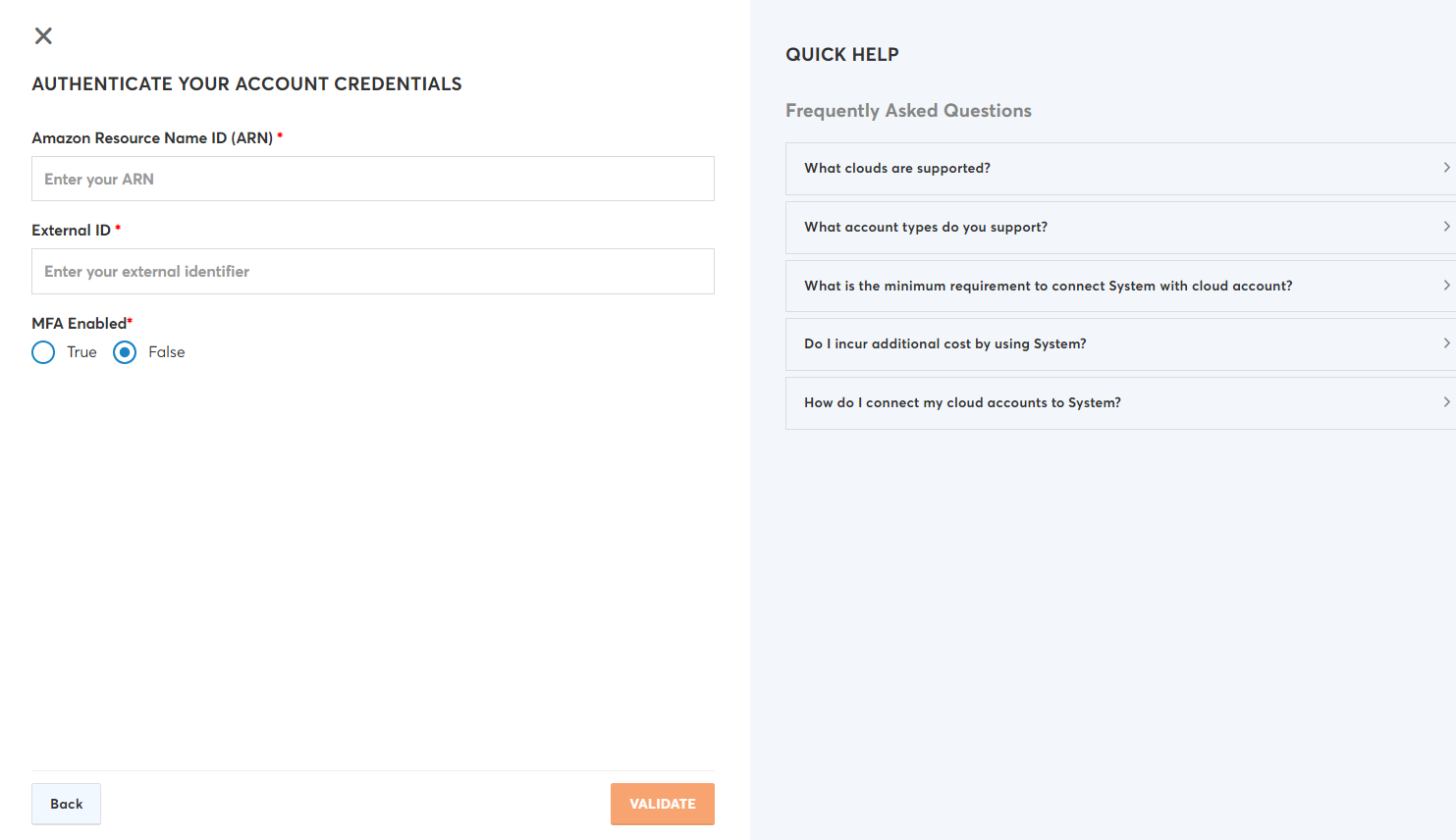
- Provide the necessary details (Amazon Resource Name ID (ARN), External ID, & MFA Enabled OR Access Key & Secret Key) explained in the Pre-onboarding section based on the option selected in the Authentication Protocol field.
Note:
For MFA Enabled field, select True or False based on whether your account is restricted with Multi-Factor Authentication.
- Click Validate button.
- The Advanced Settings section will be displayed with additional fields (Name, Master Account, Cost Report Access, S3 Bucket URI, Preferred Regions, and Scope).
- Modify the pre-populated name of the account in the Name field, if required.
- Select the associated AWS management account in the Master Account drop-down list. This field will be displayed only while onboarding an AWS Member Account.
- Select the required option in the Cost Report Access field. The options are: Master Account, Delegated Account, Current Account, and None.
- Master Account: This option will enable the cost reports be gathered in the associated AWS management account and utilized by CoreStack. S3 Buckets and Cost & Usage Reports must be configured in the relevant AWS management account. The S3 Bucket URI field will not be available for this selection.
- Delegated Account: This option will enable the cost reports be gathered in any one of your AWS Account and utilized by CoreStack. S3 Buckets and Cost & Usage Reports must be configured in the relevant AWS Account. Specify the URL of the S3 Bucket in the S3 Bucket URI field.
- Current Account: This option will enable the cost reports be gathered in the AWS Account that is being onboarded and utilized by CoreStack. S3 Buckets and Cost & Usage Reports must be configured in the AWS member account that is onboarded. Specify the name of the S3 Bucket in the S3 Bucket URI field.
- None: This option can be used if you do not want to use the cost data of your AWS member account. The S3 Bucket URI field will not be available for this selection.
Note:
The S3 Buckets and Cost & Usage Reports must be configured, as explained in the Pre-onboarding section, in the relevant AWS accounts associated with this selection.
- Specify the required S3 Bucket details, as explained above, in the S3 Bucket URI field.
- Select the required regions in the Preferred Regions dropdown list. Multiple regions can be selected.
- Select the required option in the Scope field. The options are: Account, Private, and Tenant.
- Click I’m Done button.
The AWS Account will be onboarded successfully into CoreStack. Relevant insights and information about the resources available in the account will be populated under each cloud governance pillars in CoreStack.
Updated 8 months ago