Tagging Governance
Overview
Users with cloud accounts often use metadata to manage various resources. Resources can be managed in the CoreStack application with the help of tags. Tags are added to metadata in key-value pair format. The tag keys and tag values are defined by users. It’s important to standardize tag keys and tag values for organizing resources. A group of these standardized tags is known as baseline tags.
Some of the advantages of using tags are operation support, cost allocation, security, access control, resource consistency, and accountability. Tagging Governance is important to ensure that any tags defined in your baseline are applied properly to cloud resources.
Applying Tags to a Resource
To apply a tag to resource, there are three steps that need to be followed:
- Add baseline for a scope.
- Select the tag and add value.
- Review tags.
Adding Baseline
The first step in Tag Governance is to define the baseline for a scope. The baseline is group of standard tags that can be applied to resources within a scope.
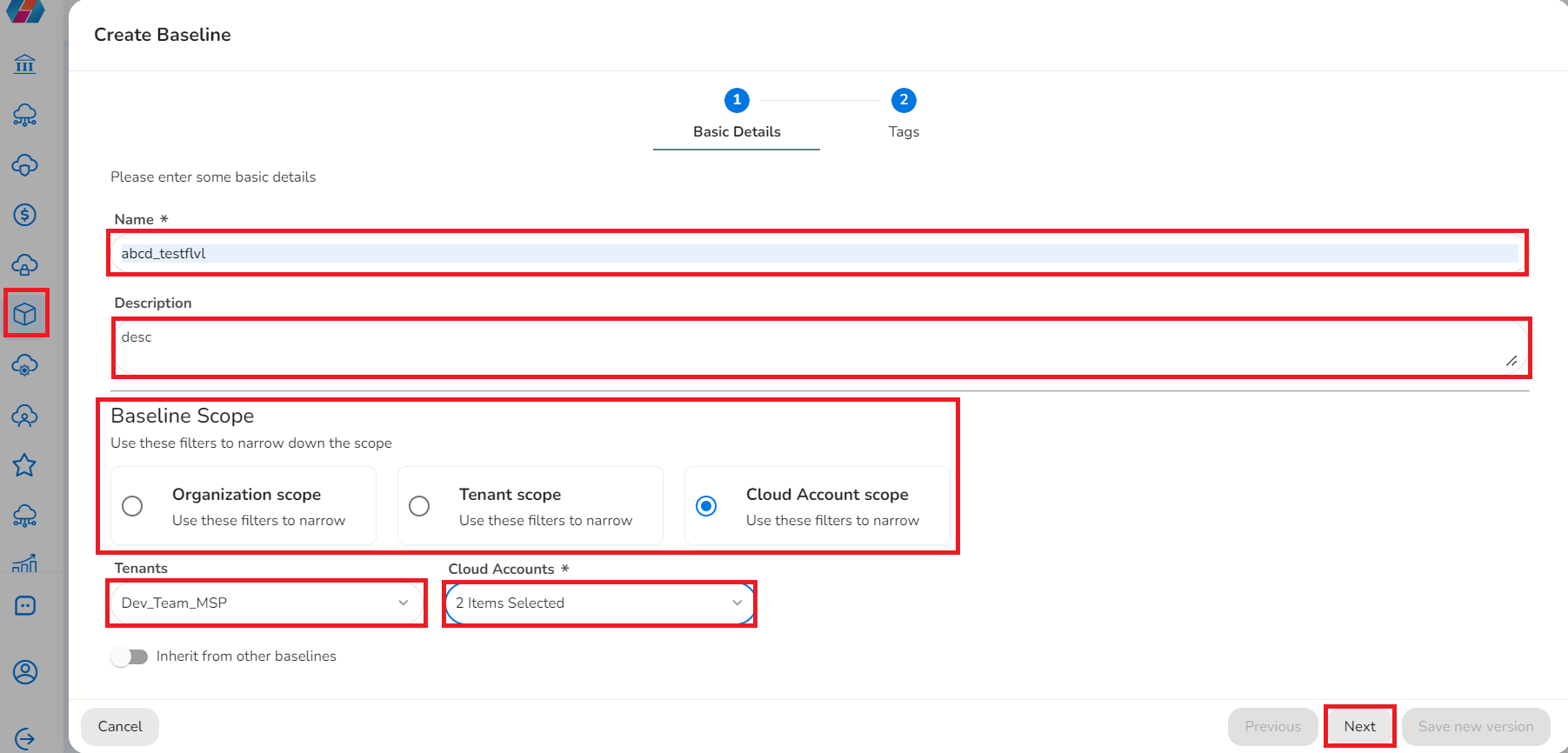
To add a baseline, perform the following steps :
- In the CoreStack application, click Resource > Tag Governance > Baseline > Create Baseline.
- In the Name box, type the name of the baseline tag and in the Description box, type the baseline tag description.
- In the Baseline Scope field, click to select one option among Organization Scope, Tenant Scope, and Cloud Account Scope.
- If you select Organization Scope, then nothing else needs to be selected.
- If you select Tenant Scope , then in the Tenant list, select the appropriate checkboxes.
- If you select Cloud Account Scope, then in the Tenant and Cloud Account lists, select the appropriate checkboxes.
- To inherit tags from other baselines, click to move the slider to right.
- Click Next.
Note:
- On the Baselines tab, the list of baselines can be viewed.
- For a particular baseline, in the Actions list, a user can select one option from Edit, View More, and Delete and take appropriate action.
Selecting Tag and Adding Values
After a baseline scope is defined for tags, the next step is to select tags and set their values.
There are four sources of tags:
-
Available Tag
-
CS Baseline Tag
-
Custom Tag
-
Inherited Tag
The Available Tags are the tags that are already applied to the resources. CS Baseline Tags are baseline tags recommended by CoreStack. Custom Tags are additional tags that can be added by a user. Inherited Tags are tags that are part of the baseline if there is a baseline defined at higher level. Inherited tags are applied by default and a user cannot select or change these tags.
Perform the following steps to apply tags to resources for the scope defined above:
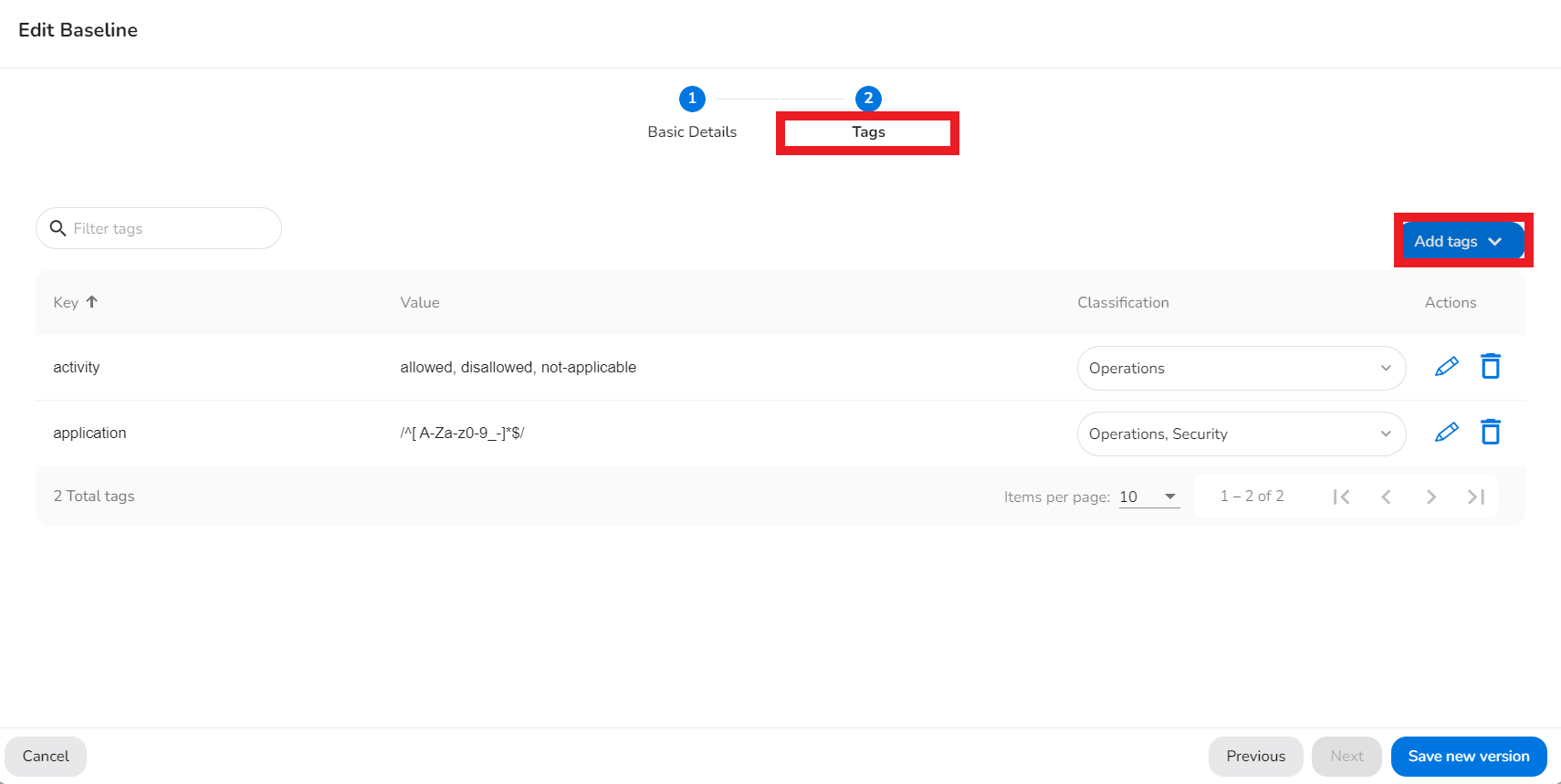
- In the Tags tab, in the Add Tags list, click to select one of the following:
- Add Custom Tag
- Add Existing Tag
- Add CS Baseline Tags
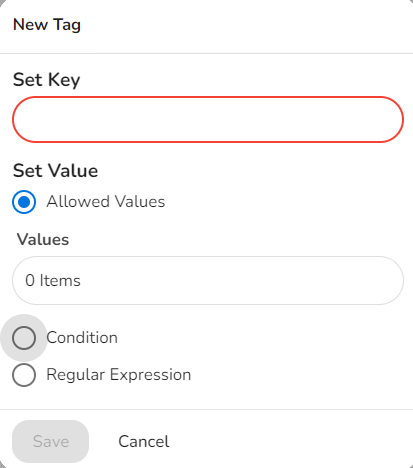
- If the user selects Add Custom Tag, then in the New Tag dialog box, in the Set Key box, type the key. Then select one of the following options to add a value, then click Save.
- Select the Allowed Values option. In the Values box, type a value and click OK. Alternatively, select an existing value.
- Select the Condition option and type the appropriate values in the following boxes:
- Start With
- End With
- Contains
- Select the Regular Expression option. In the Regular Expression box, type the required expression.
Note:
Click the pencil icon to edit an existing value and click the search icon to search for a tag.
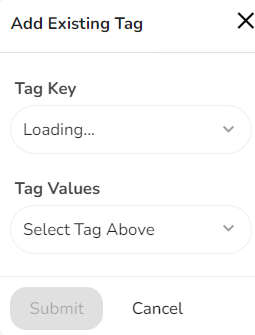
- If the user selects Add Existing Tag, then the Add Existing Tag dialog box displays. Select the appropriate values in the following fields then click Submit.
- In the Tag Key list, click to select an appropriate option.
- In the Tag Values list, click to select an appropriate option.
- If the user selects Add CS Baseline Tags, then select the appropriate boxes and click Submit.
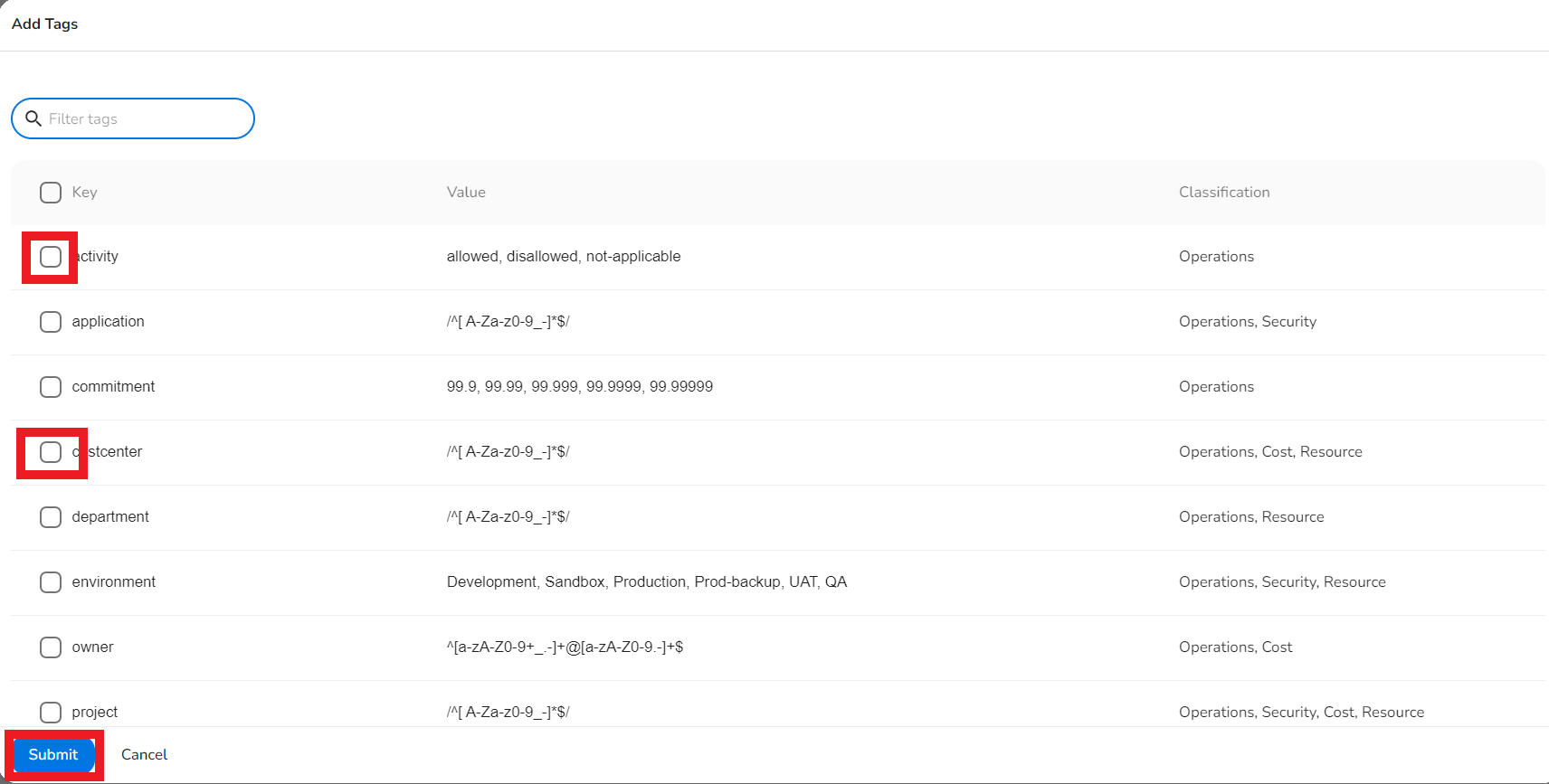
- Click Save new version.
All the keys selected in this procedure are now part of the baseline tags.
Reviewing Tags
On the Tag Governance screen, users can view two tabs: the Baselines tab and the Tag Posture tab. The Baselines tab shows the available baselines. That is, the list of baselines created, when it was last updated, whether it is active or not, etc.
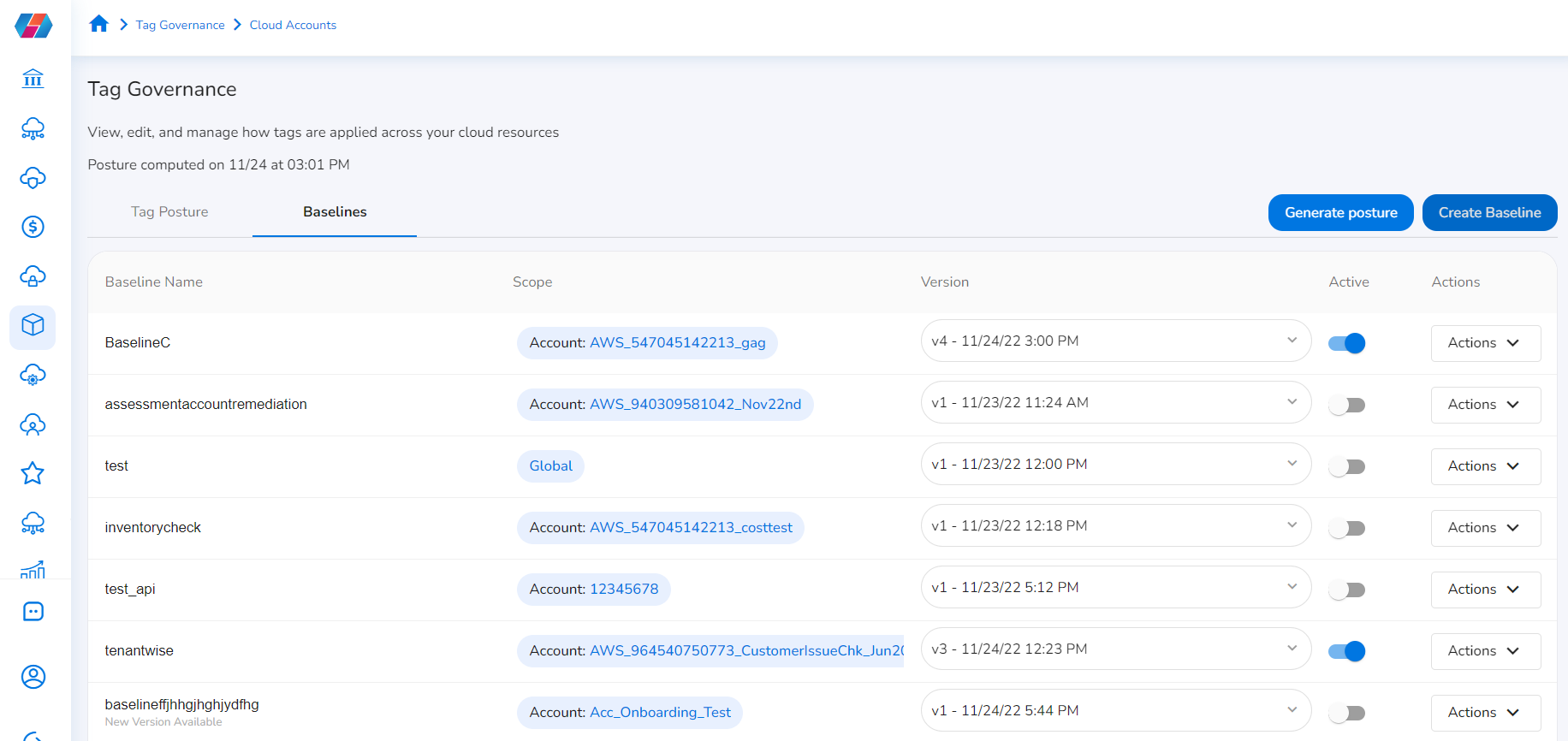
Tag Posture
The Tag Posture tab displays the details about tag coverage, resource coverage, and their respective counts. A user can click Generate Posture to generate or update tag posture. A user needs to refer to this screen to find out about gaps in tag coverage and resource coverage. After the gaps are identified, the user must add the missing tag keys or values to improve coverage. This screen also shows the percentage of tag coverage and resource coverage.
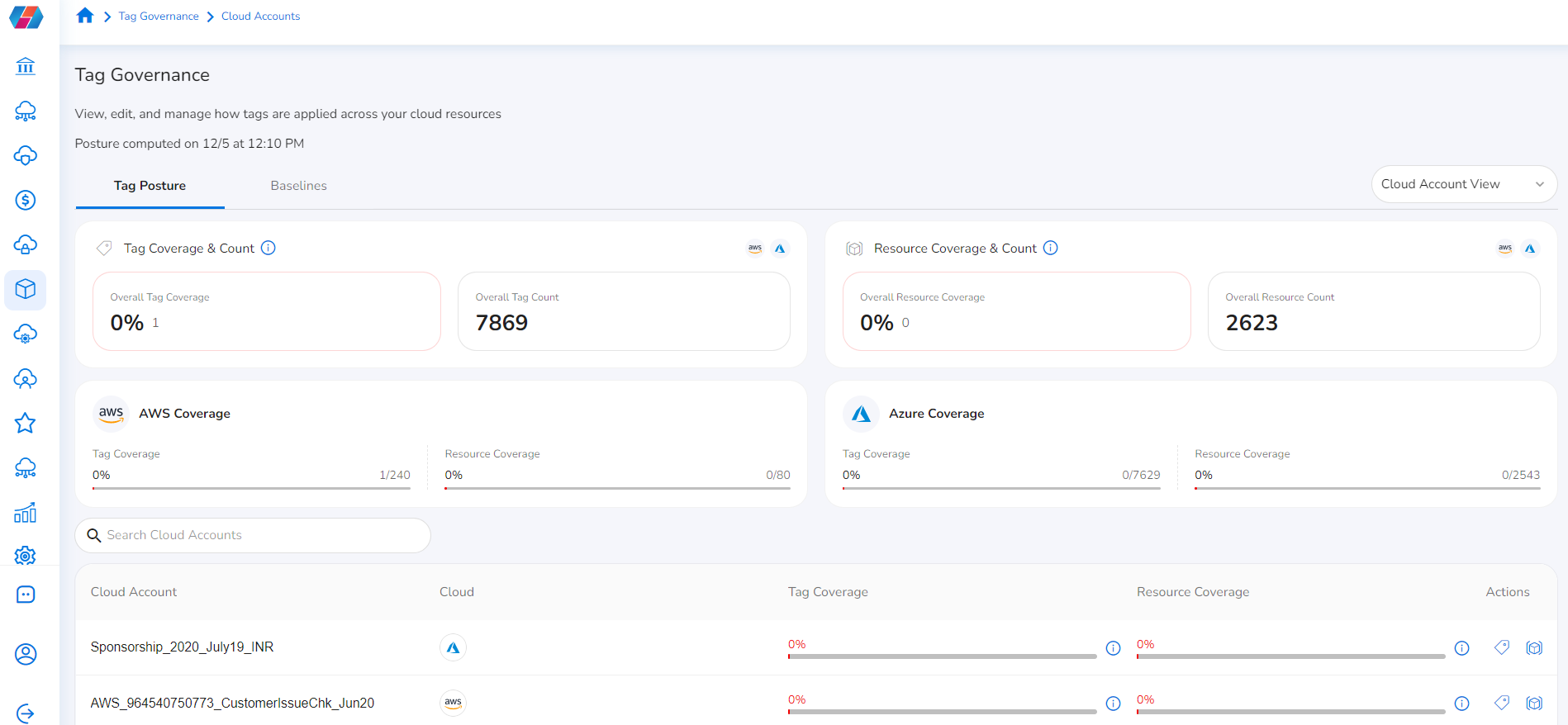
Perform the following steps to view coverage details:
- On the Tag Governance screen, click the Tag Posture tab.
A user can view Tag Coverage & Count as well as Resource Coverage & Count, and they can also view account-specific Tag Coverage and Resource Coverage. - In the drop-down list on the right side of the screen, click to select one option from Organization View, Tenant View, and Cloud Account View.
- For a particular cloud account, click the icon below Actions or click View More and then click the icon below Actions.
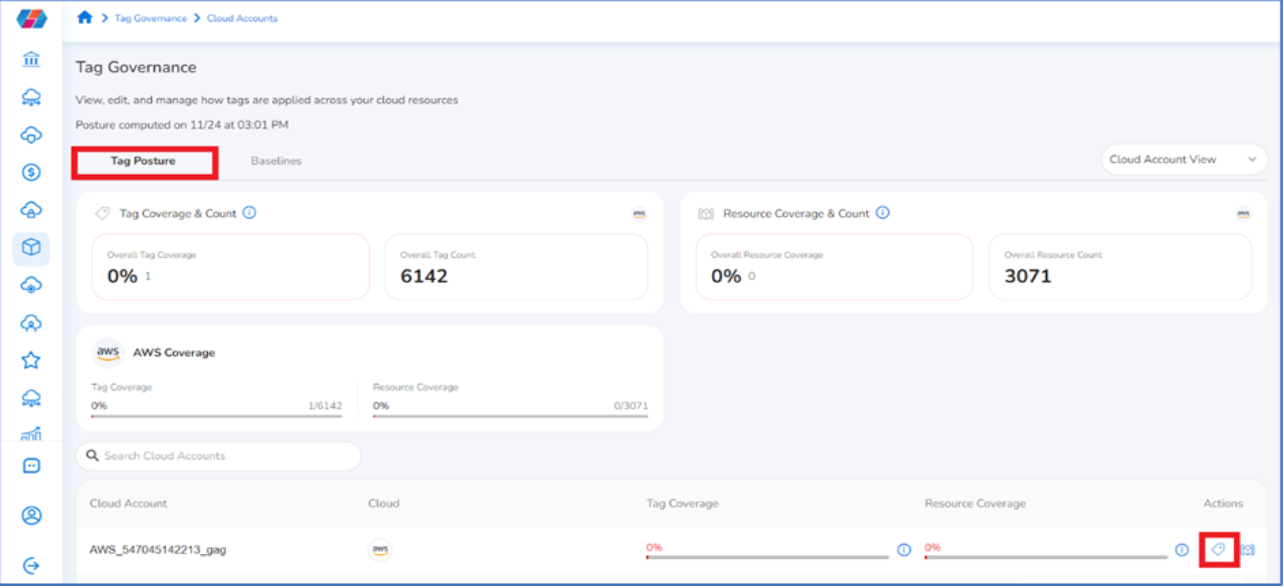
Users can then view the following details:
- The Tag View tab shows Tag Keys, Resources Missing Tag Key, Resources Invalid Tag Value, and tag percentage.
- Tag Key: This column shows the tag keys defined for a baseline.
- Resources Missing Tag Key: This column lists the number of resources that have missing tag keys.
- Resources Invalid Tag Value: This column lists the number of resources that have incorrect tag values.
- Coverage: This shows the coverage percentage.
- The Resource View tab shows Resource Coverage, Missing Tag Keys, and Invalid Tag Values.
- This tab displays details in tabular format and users can click View Coverage to see the coverage details.
- In the Tag View tab, select a tag key and click Improve Coverage. The Tag Remediation screen displays.
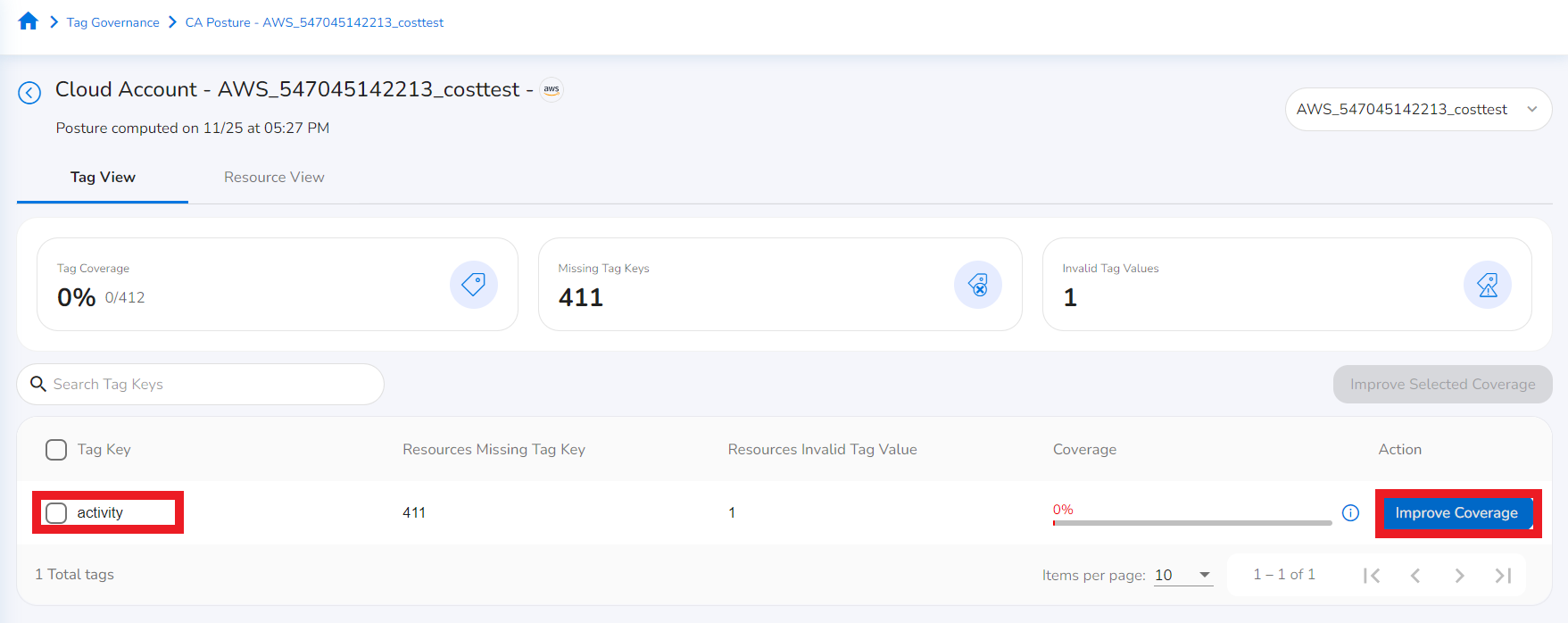
The resource name, resource type, coverage status, and key values for a baseline are displayed.
Alternatively, on the Resource View tab, a user can select a resource and click View Coverage to view the coverage details. On the Resource Remediation screen, if the Improve Coverage button is active, then users can add a value for the tag and improve the coverage.
- On the Tag Remediation screen, click Improve Coverage corresponding to a resource.
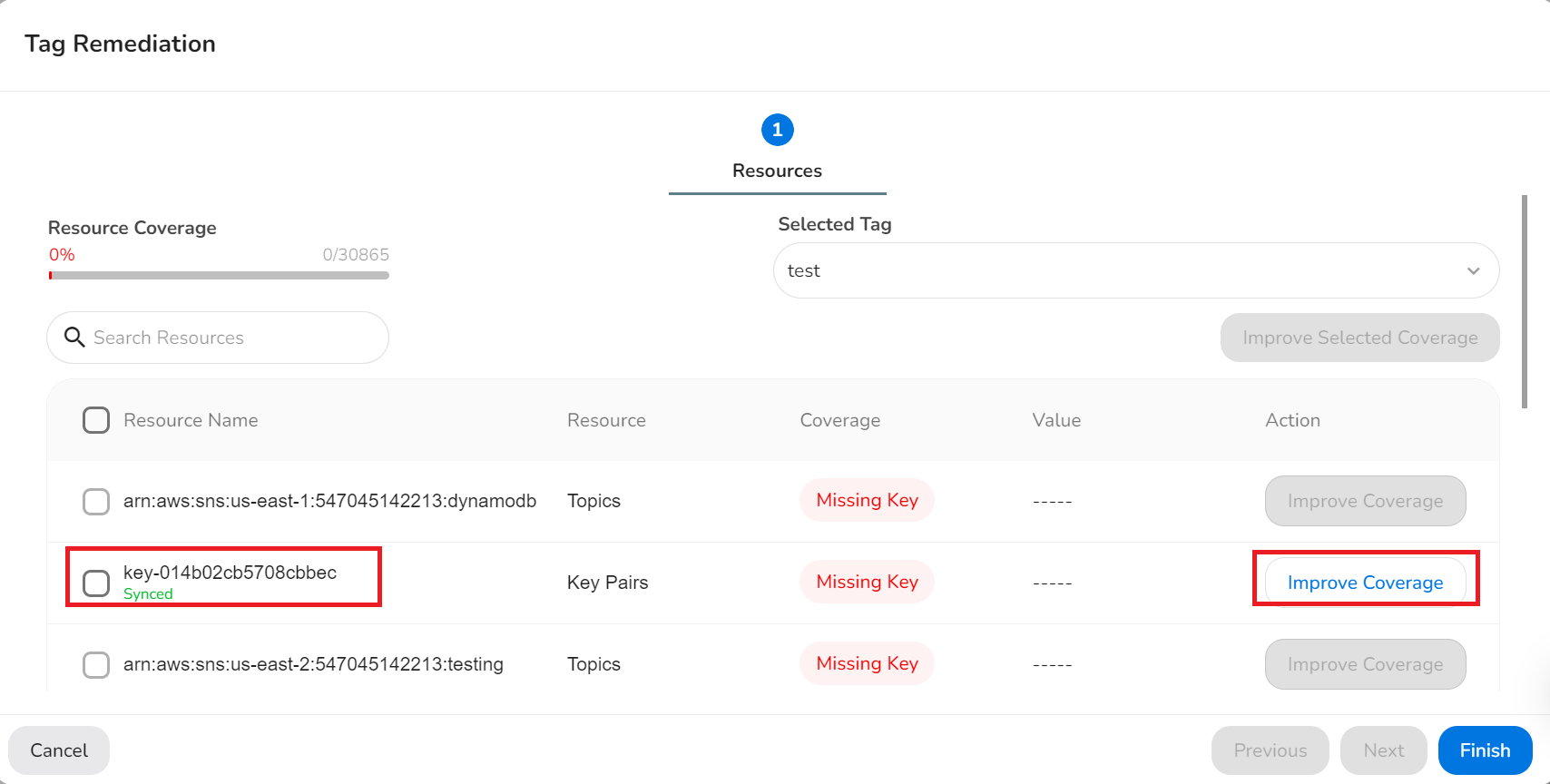
Note:
If the Improve Coverage button is disabled or grayed out, then no action can be taken.
- Users can click the Resource Name check box to select all the listed resources and then click Improve Selected Coverage to improve coverage. The resources for which Improve Coverage button is greyed out are not considered for improving coverage.
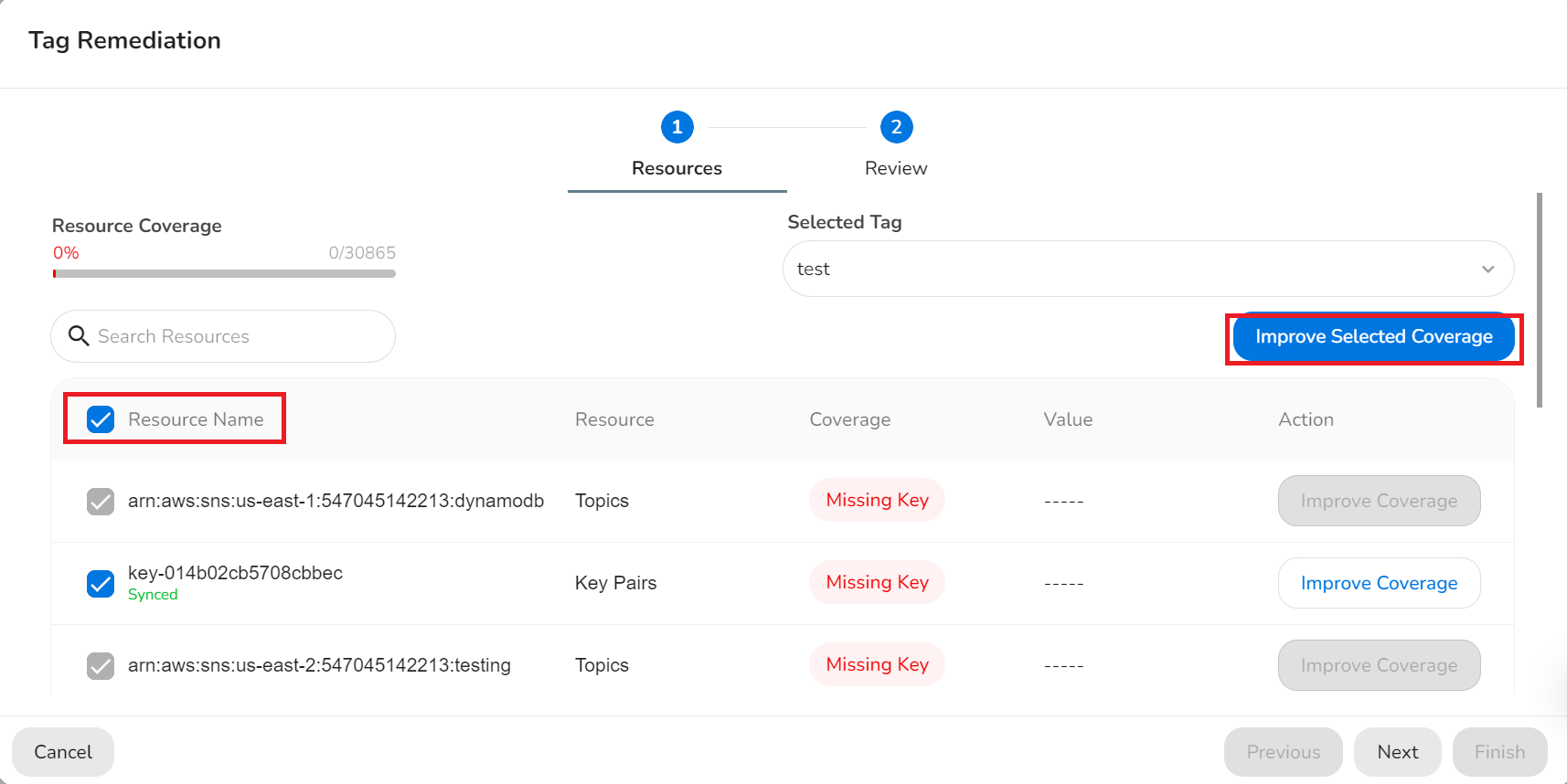
- Users can also select check boxes corresponding to particular resources for which coverage needs to be improved and then click Improve Selected Coverage.
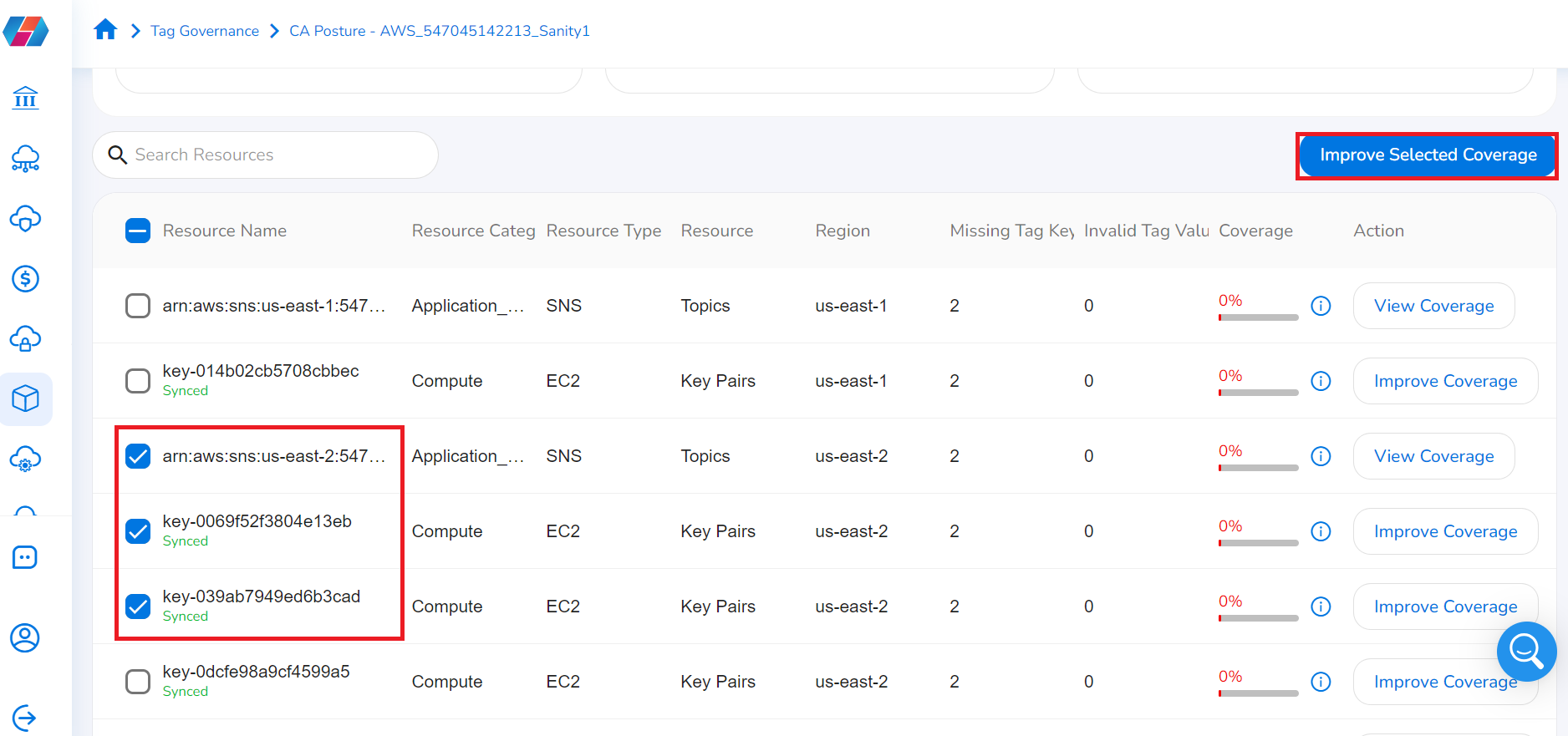
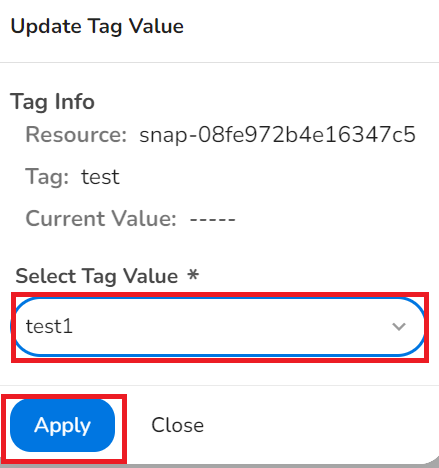
- To take remediation steps, in the Update Tag Value dialog box, in the Select Tag Value list, select an appropriate value as per baseline, and click Apply.
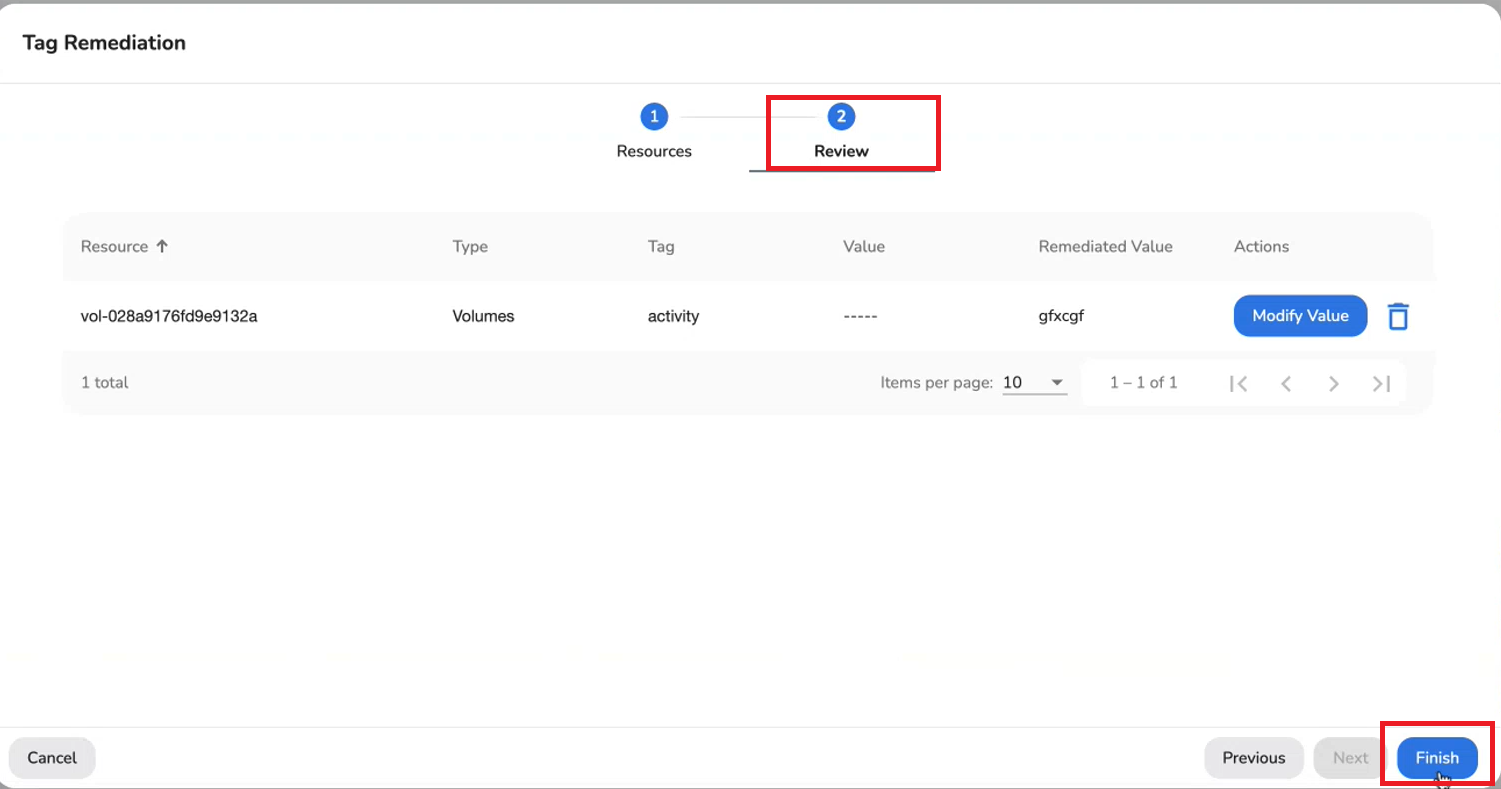
- On the Tag Remediation screen, click Next. In the Review tab, review the values that are added in the previous steps. If any tag value needs to be changed, then click Modify Value and make the change.
- Click Finish.
After the key values are updated for a tag, the status Synced appears below the resource name (on the Tag Remediation screen). This means that the tag has been synced with the could provider and the coverage status will change to Complete. This will increase the coverage percentage.
If Not Synced appears below the resource name, then this means that the tag has issues to sync with the could provider and the status Missing Key shows for that resource. The user should take remediation steps to add a valid key value and increase the coverage.
- Repeat the above steps to fill valid tag keys and tag values.
After the key values are added successfully, the coverage percentage increases and can be viewed on the Tag Posture, Tag View, and Resource View tabs.
Note:
Refer to this link to view the list of resources that allows remediation of tags.
Roles for Posture Generation and Baseline Access
There are defined roles allocated to users, based on which they can generate posture and access baselines. Every role has different permissions, and based on the role type assigned to a user they will have certain action/access rights (e.g. create/read/update/delete).
Refer to the topics explained below to view lists of roles with access to baseline tags at the Organization scope and Tenant scope levels, and roles that can execute postures and view postures.
RBAC for Baseline Tags
The role types that can access baseline tags at Organization and Tenant scope are explained below.
Baseline Tags at Organization Scope
Only an Account Admin has the permission to create, read, update, and delete baseline tags at the Organization scope.
Users with the following roles only have read permissions for baseline tags at Organization scope:
- Tenant Admin
- CloudOps Admin
- CloudOps Member
- CloudOps Reader
- Compliance Admin
- Compliance Member
- Security Admin
- Security Member
- SecOps Admin
- SecOps Reader
- FinOps Admin
- FinOps Practitioner
- FinOps Reader
- Assessment Admin
- Assessment Member
- Assessment Reader
- Assessment Approver
- Workload Owner
Baseline Tags at Tenant and Account Scope
Users with the following roles have create, read, update, and delete permissions for baseline tags at Tenant scope:
- Account Admin
- Tenant Admin
- CloudOps Admin
- Compliance Admin
- Security Admin
- SecOps Admin
- FinOps Admin
- Workload Owner
Users with the following roles only have read permission for baseline tags at Tenant scope:
- CloudOps Member
- CloudOps Reader
- Compliance Member
- Security Member
- SecOps Reader
- FinOps Practitioner
- FinOps Reader
- Assessment Admin
- Assessment Member
- Assessment Reader
- Assessment Approver
RBAC for Generating Posture
Users can generate posture based on their access level. The roles that can generate postures and view postures are explained below.
Users with the following roles can execute posture:
- Account Admin
- Tenant Admin
- CloudOps Admin
- Compliance Admin
- Compliance Member
- Security Admin
- Security Member
- SecOps Admin
- FinOps Admin
- FinOps Practitioner
- Assessment Admin
- Assessment Member
- Assessment Reader
- Assessment Approver
- Workload Owner
Users with the following roles have read permission for Tag Posture - Tenant & Cloud Account View:
- Account Admin
- Tenant Admin
- CloudOps Admin
- CloudOps Member
- CloudOps Reader
- Compliance Admin
- Compliance Member
- Security Admin
- Security Member
- SecOps Admin
- SecOps Reader
- FinOps Admin
- FinOps Practitioner
- FinOps Reader
- Assessment Admin
- Assessment Member
- Assessment Reader
- Assessment Approver
- Workload Owner
Partial Posture Generation
For partial posture generation, users must note the following:
- Posture can be generated by users who have relevant RBAC permissions.
- Posture can be generated for the scope to which the user has access to.
- If the scope of a baseline is Organization, then users who have access to generate posture can execute it, but the posture will be generated for tenants -- wherein the user is part of the tenant.
Restrict Baseline Access
Users can create and view baselines based on their role. Global baselines can be viewed by all users. Refer to RBAC for Baseline Tags for more details.
Let us understand baseline access with the help of different scenarios explained below.
Case 1: If the baseline has scope for Tenant A and Tenant B, and if the user is a Tenant Admin for Tenant A but has no access for Tenant B, then the Tenant Admin can view the baseline (with the Tenant scope shown where they have access). They cannot edit the baseline as it is a shared baseline.
Case 2: If the baseline has scope for Tenant A and Tenant B, and if the user is a Tenant Admin for Tenant A and has read-only access for Tenant B, then the Tenant Admin can view the baseline (with the tenant scope shown where they have access to both). They cannot edit the baseline as it is a shared baseline but do have access to edit one tenant.
Case 3: If the baseline has scope for Tenant A and Tenant B, and if the user is a Tenant Admin for both Tenant A and Tenant B, then the Tenant Admin can view the baseline (with the tenant scope shown where they have access to both) and also edit the baseline as they have edit access for both tenants.
Note:
If the scope is updated in one version of a baseline, it will be updated across all other versions of that baseline.
Updated 8 months ago