Security Analytics
Introduction
CoreStack provides managed vulnerability assessment scanning that automatically detects the highest severity vulnerabilities and misconfigurations for your cloud assets. The reports are powered by rich data transformation and data visualization layers to give you intelligent insights.
| Report Group | Report Name | Report Description |
|---|---|---|
| Vulnerability Analytics | AWS Security Vulnerability | Security vulnerabilities fetched from native AWS services for your selected cloud accounts. |
| Vulnerability Analytics | Azure Security Vulnerability | Security vulnerabilities fetched from native Azure services for your selected cloud accounts. |
| Threat Analytics | AWS Security Threat | Detect and act on important security events. |
| Threat Analytics | Azure Security Threat | Detect and act on important security events. |
Vulnerability Trend
You can view historical data quickly and easily for any vulnerabilities in your AWS cloud resources.
In order to properly govern and get the most out of your cloud deployments, it’s crucial to have clear visibility into any vulnerabilities your cloud resources might have.
The vulnerability trend feature provided in CoreStack with help from 24.7ai allows you to analyze historical cloud data for vulnerabilities reported by the system (daily, weekly, and monthly). Additionally, you can also download the vulnerability data for reference.
Note
This feature is only applicable to data from AWS.
Follow the below steps to learn how you can access and view analytics for vulnerability trends in CoreStack.
- In the CoreStack left navigation bar, Click Reports.
- Click Security.
- Click AWS.
- Click AWS Security Vulnerability.
- Click Trend. The vulnerability trends for day, week, and month time periods should appear.
- To track any active trends, select the Status drop-down menu near the top of the screen and then select Active.
Azure Secure Score and Recommendations Report
The Azure Secure Score report performs an assessment on a user’s cloud account and provides a Secure Score report along with recommendations. The Secure Score ratings are calculated based on best practices followed across the industry. A maximum score of 100 is ideal, and any score below 100 means there are potential improvement factors to consider. Any score below 100 implies that there are security vulnerabilities, and so to improve the score it’s strongly advised that users follow the recommendations provided.
The Azure Secure Score Report can be accessed by navigating to the following places in CoreStack:
- Reports > Operations > Azure > Operations Governance > Azure Cloud Assessment Report > Section 4.0
- CoreStack External API Site > Report Section > Secure Score Mapping Report
For example, refer to the Security Score Report for the month of July and its Score Recommendation Details chart. The graph shown below shows a Secure Score of 20.5, which is extremely low. To improve the score, it’s important to act as per the Score Recommendation Details chart.
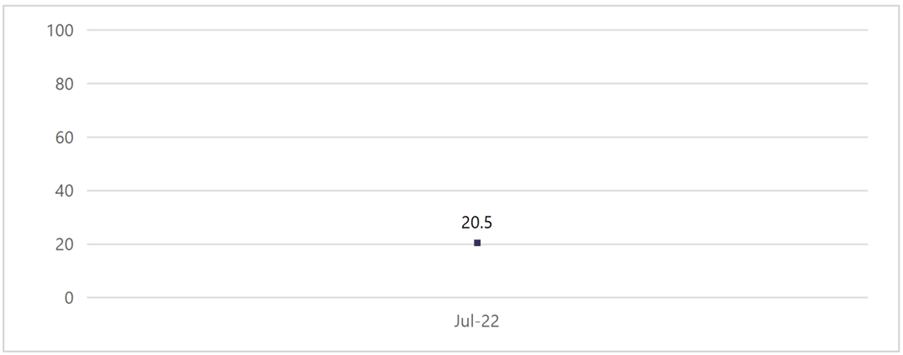
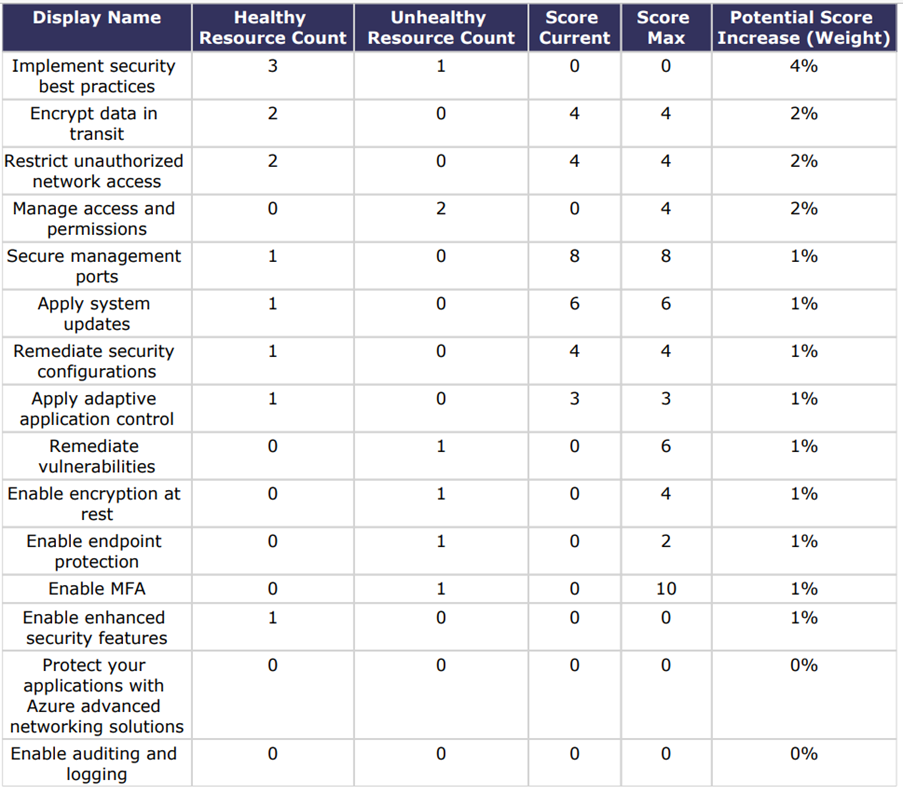
Score Recommendation Details
As per the Score Recommendation Details chart, the Unhealthy Resource Count needs to be minimized to increase the overall secure score. The Score Recommendation Details chart displays the following columns:
- Display Name: This column lists best practices that needs to be followed.
- Healthy Resource Count: This column displays the count of healthy resources – ideally, the count should be high.
- Unhealthy Resource Count: This column displays the count of unhealthy resources – ideally, the count should be low.
- Score Current: This column displays the current Secure Score.
- Score Max: This column displays the maximum Secure Score available.
- Potential Score Increase (Weight): This column displays the increase in score percentage that can be achieved by following best practices.
Updated 8 months ago