Pre-Onboarding for OCI Tenancies
Introduction
This user guide will explain how to perform the pre-onboarding steps required for onboarding an OCI Tenancy into the platform.
To begin monitoring your resources for OCI, you must complete some tasks on the OCI Tenant Console and some on the platform. After you add your OCI tenant to the platform, the API integration between OCI and the platform is established and you can monitor resource configuration issues.
Prerequisites
- Root compartment (tenancyId).
- An IAM user with user id (authUserId).
- API key to be generated. Private Key and keyFingerprint used while onboarding.
- Policy to be created with required access to the APIs and attach the policy to the Group where the created user is added into the group.
Oracle Cloud IDs (OCIDs)
Most types of Oracle Cloud Infrastructure resources have an Oracle-assigned unique ID called an Oracle Cloud Identifier (OCID). It's included as part of the resource's information in both the Console and API.
To use the API, you need the OCID for your tenancy.
OCIDs use this syntax:
ocid1.<RESOURCE TYPE>.<REALM>.[REGION][.FUTURE USE].<UNIQUE ID>
-- ocid1: The literal string indicating the version of the OCID.
-- resource type: The type of resource (for example, instance, volume, vcn, subnet, user, group, and so on).
-- realm: The realm the resource is in. A realm is a set of regions that share entities. Possible values are oc1 for the commercial realm, oc2 for the Government Cloud realm, or oc3 for the Federal Government Cloud realm. The regions in the commercial realm (OC1) belong to the domain oraclecloud.com. The regions in the Government Cloud (OC2) belong to the domain oraclegovcloud.com.
-- region: The region the resource is in (for example, phx, iad, eu-frankfurt-1). With the introduction of the Frankfurt region, the format switched from a three-character code to a longer string. This part is present in the OCID only for regional resources or those specific to a single availability domain. If the region is not applicable to the resource, this part might be blank (see the example tenancy ID below).
-- future use: Reserved for future use. Currently blank.
-- unique ID: The unique portion of the ID. The format may vary depending on the type of resource or service
Where to Find Your Tenancy's OCID
If you use the Oracle Cloud Infrastructure API, you need your tenancy's OCID in order to sign the API requests. You also use the tenancy ID in some of the IAM API operations.
Get the tenancy OCID from the Oracle Cloud Infrastructure Console on the Tenancy Details page:
1). Open the Profile menu (User menu icon) and click Tenancy: <your_tenancy_name>.
2). The tenancy OCID is shown under Tenancy Information. Click Copy to copy it to your clipboard.
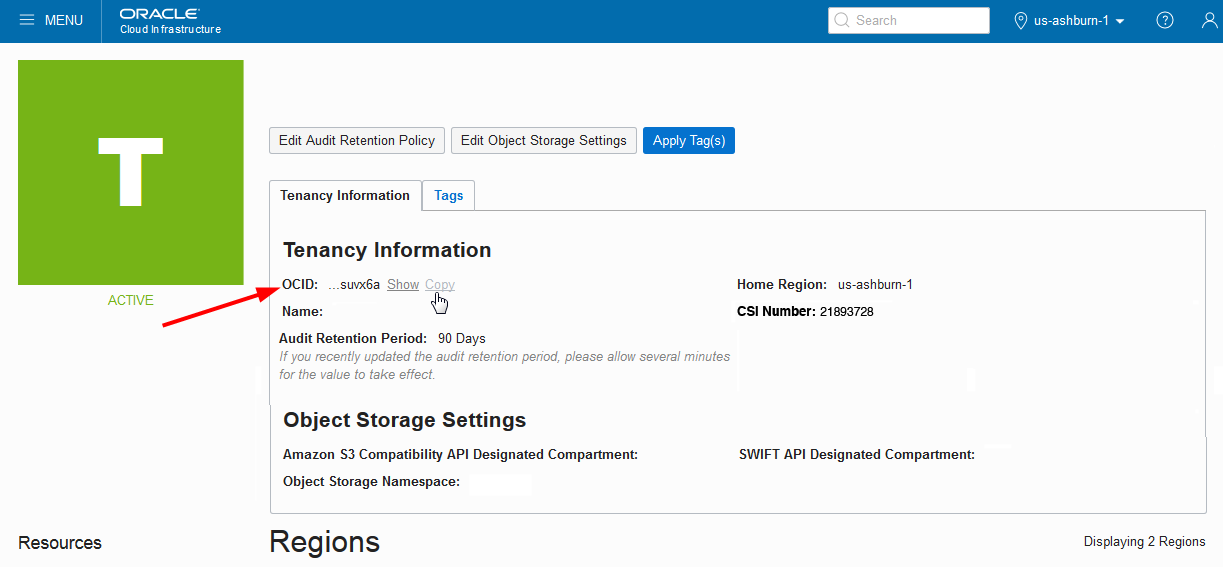
The tenancy OCID looks something like this (notice the word "tenancy" in it):
ocid1.tenancy.oc1..<unique_ID>
IAM Service
The IAM service requires you to assign a unique, unchangeable name to each of your IAM resources (users, groups, dynamic groups, federations, and policies). The name must be unique within the scope of the type of resource (for example, you can only have one user with the name BobSmith). Notice that this requirement is specific to IAM, but also applies to some other services. (Most services let you assign an optional display name.)
The name you assign to a user at creation is their login for the Console.
You can use these names instead of the OCID when writing a policy (for example, Allow group <GROUP NAME> to manage all-resources in compartment <COMPARTMENT NAME>).
In addition to the name, you must also assign a description to each of your IAM resources.
Required IAM Policy
If you're in the Administrators group, then you have the required access for managing users. You can create a policy that gives someone the power to create new users and credentials but not control which groups those users are in.
For users resource type, you can use target.user.id as variable and Entity (OCID) as variable type.
Required Keys
1). After you have created a user in IAM for the person or system who will be calling the API, put that user in at least one IAM group with any desired permissions.
2). Get below items:
-
RSA key pair in PEM format (minimum 2048 bits). See How to Generate an API Signing Key.
-
Fingerprint of the public key. See How to Get the Key's Fingerprint.
-
Tenancy's OCID and user's OCID. See Where to Get the Tenancy's OCID and User's OCID.
3). Upload the public key from the key pair in the Console. See How to Upload the Public Key.
Resource List
After onboarding, inventory will auto populate. We support below resources.
- Compute -> Compute -> Instances
- Compute -> Compute -> Dedicated_VM_Host
- Compute -> Compute -> Instance_Configuration
- Compute -> Compute -> Instance_Pools
- Compute -> Compute -> Cluster_Networks
- Compute -> Compute -> Autoscaling_Configuration
- Databases -> MySQL -> DB_Systems
- Databases -> MySQL -> Backups
- Databases -> Oracle_NoSQL_Database -> Tables
- Oracle_DataBase -> BareMetal_VM_Exadata -> ExaData_infrastructure
- Oracle_DataBase -> BareMetal_VM_Exadata -> ExaData_VM_Clusters
- Storage -> Block_Storage -> Block_Volumes
- Storage -> Block_Storage -> Block_VolumeBackups
- Storage -> Block_Storage -> Attached_Volumes
- Storage -> File_Storage -> File_Systems
- Storage -> Block_Storage -> Mount_Targets
- Networking -> Virtual_Cloud_Networks -> VCN
- Networking -> Virtual_Cloud_Networks -> Internet_Gateway
- Networking -> Virtual_Cloud_Networks -> LocalPeeringGateways
- Networking -> Virtual_Cloud_Networks -> Security_Lists
- Networking -> Virtual_Cloud_Networks -> NetworkSecurityGroups
- Networking -> Customer_Connectivity -> Fast_Connect
- Networking -> Customer_Connectivity -> Dynamic_Routing_Gateway
- Networking -> Ip_Management -> Reserved_Publics_IPs
- Networking -> Load_Balancers -> Load_Balancer
- Networking -> DNS_Management -> Zones
- Identity_Security -> Web_Application_Firewall -> Waf_Policy
- Identity_Security -> Identity -> Users
- Identity_Security -> Identity -> Groups
- Identity_Security -> Identity -> Policies
- Identity_Security -> Identity -> Users_Api_Keys
- Identity_Security -> Identity -> Users_Auth_Tokens
- Identity_Security -> Scanning -> HostScan
- Identity_Security -> Scanning -> PortScan
- Developer_Services -> Containers -> Container_Registry
- Developer_Services -> Containers -> Artifact_Registry
- Developer_Services -> Functions -> Applications
- Developer_Services -> Containers -> Kubernetes_Clusters
- Analytics_AI -> Data_Lake -> Data_Flow
- Application_Integration -> Content_Management -> Instances
Updated 8 months ago