Azure Security Center Vulnerability Assessment
Overview
This document explains how your Azure environment's vulnerabilities are automatically discovered, assessed, and tracked through our Azure Security Center integration. The system provides comprehensive vulnerability management by connecting to your Azure Security Center and Log Analytics workspaces to identify security risks across your cloud infrastructure.
How Vulnerability Data is Collected
Data Sources
The vulnerability assessment system collects security findings from multiple Azure data sources.
-
Azure Security Center Recommendation
- Security policy violations
- Configuration compliance issues
- Best practice recommendations
-
Vulnerability Assessments
- CVE-based security vulnerabilities
- Known security flaws in software components
- Critical and high-severity exposures
-
Update Management
- Missing security patches
- Critical Windows updates
- Security rollups and hotfixes
-
Security Baseline Assessments
- Configuration security violations
- Policy compliance failures
- Security hardening gaps
Collection Process
CoreStack schedules retrieval of vulnerabilities from each of the onboarded active Azure Subscriptions on a daily basis. For each of the active Subscription that has Azure Security Centre (now Defender) enabled, a default log analytics workspace is created. The process retrieves the list of all such available default workspaces. For each Log Analytics workspace, the system executes specialized queries to extract. Refer to some examples provided below.
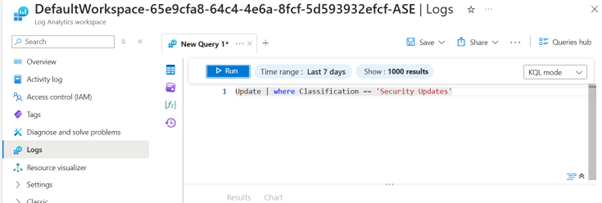
Update: (Time range: Last 7 days)
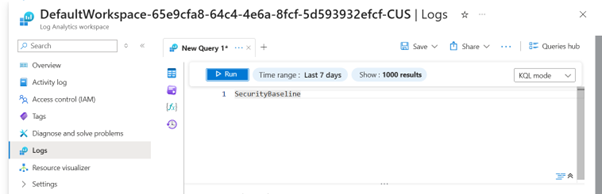
SecurityBaseline: (Time range: Last 7 days)
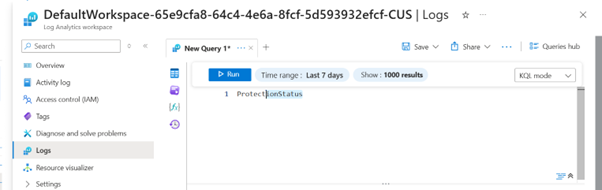
ProtectionStatus: (Time range: Last 7 days)
Updated about 9 hours ago